Audit Logging Standards

Quick Navigation:
- Audit Logging Standards Definition
- Audit Logging Standards Explained Easy
- Audit Logging Standards Origin
- Audit Logging Standards Etymology
- Audit Logging Standards Usage Trends
- Audit Logging Standards Usage
- Audit Logging Standards Examples in Context
- Audit Logging Standards FAQ
- Audit Logging Standards Related Words
Audit Logging Standards Definition
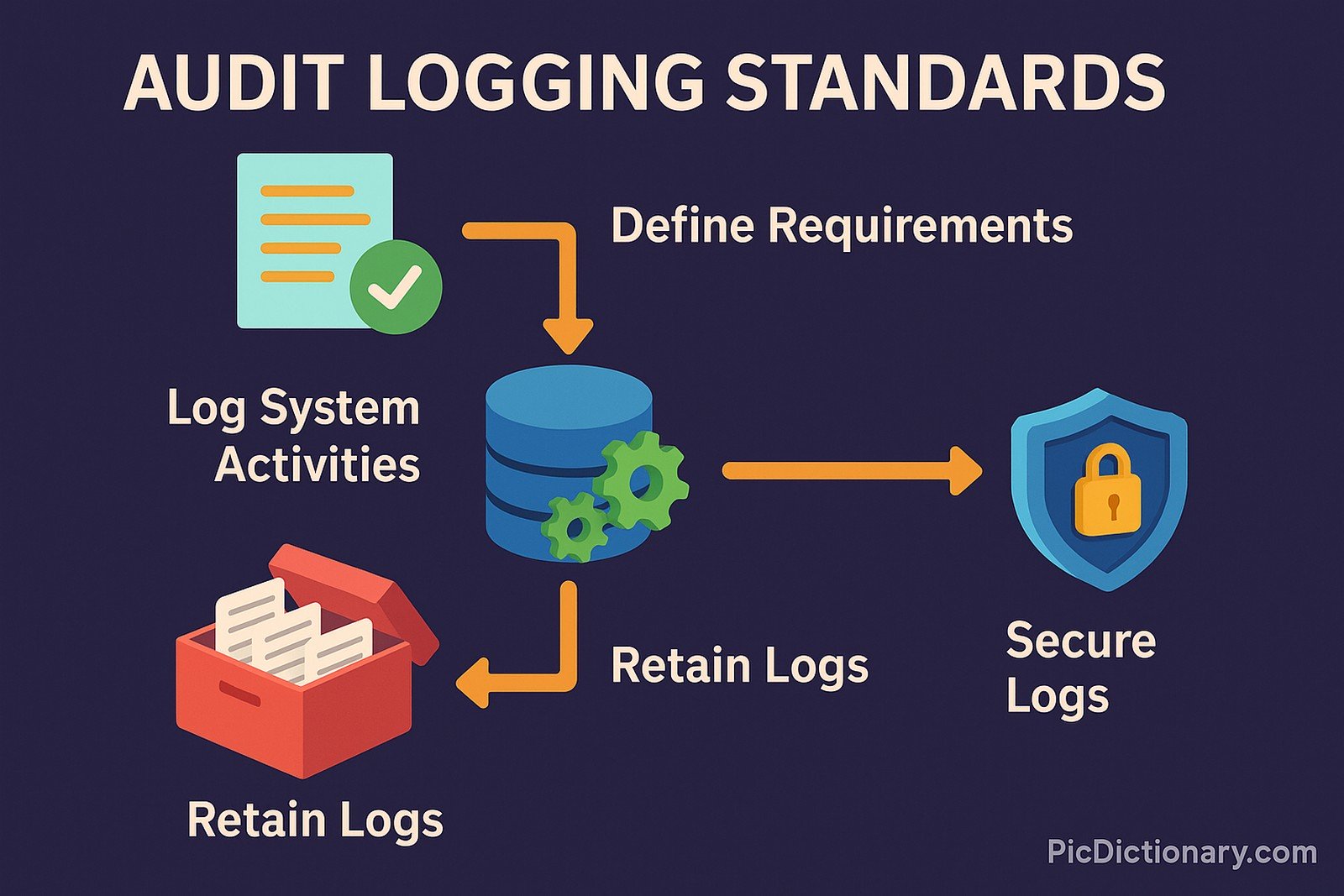
Audit logging standards define the guidelines and best practices for recording system activities to ensure security, compliance, and operational integrity. These standards specify what data should be logged, how long logs should be retained, and the mechanisms used to secure them. Common frameworks, such as ISO 27001, NIST 800-92, and PCI DSS, outline principles for maintaining logs to detect anomalies, support forensic investigations, and facilitate compliance with legal requirements.
Audit Logging Standards Explained Easy
Imagine you have a notebook where you write down every time someone enters or leaves your house. You include the time, who it was, and what they did. If something goes missing, you can check your notes to see what happened. Audit logging standards work the same way but for computer systems. They ensure that activities like logins, data access, and changes are recorded so that security teams can track and investigate issues when needed.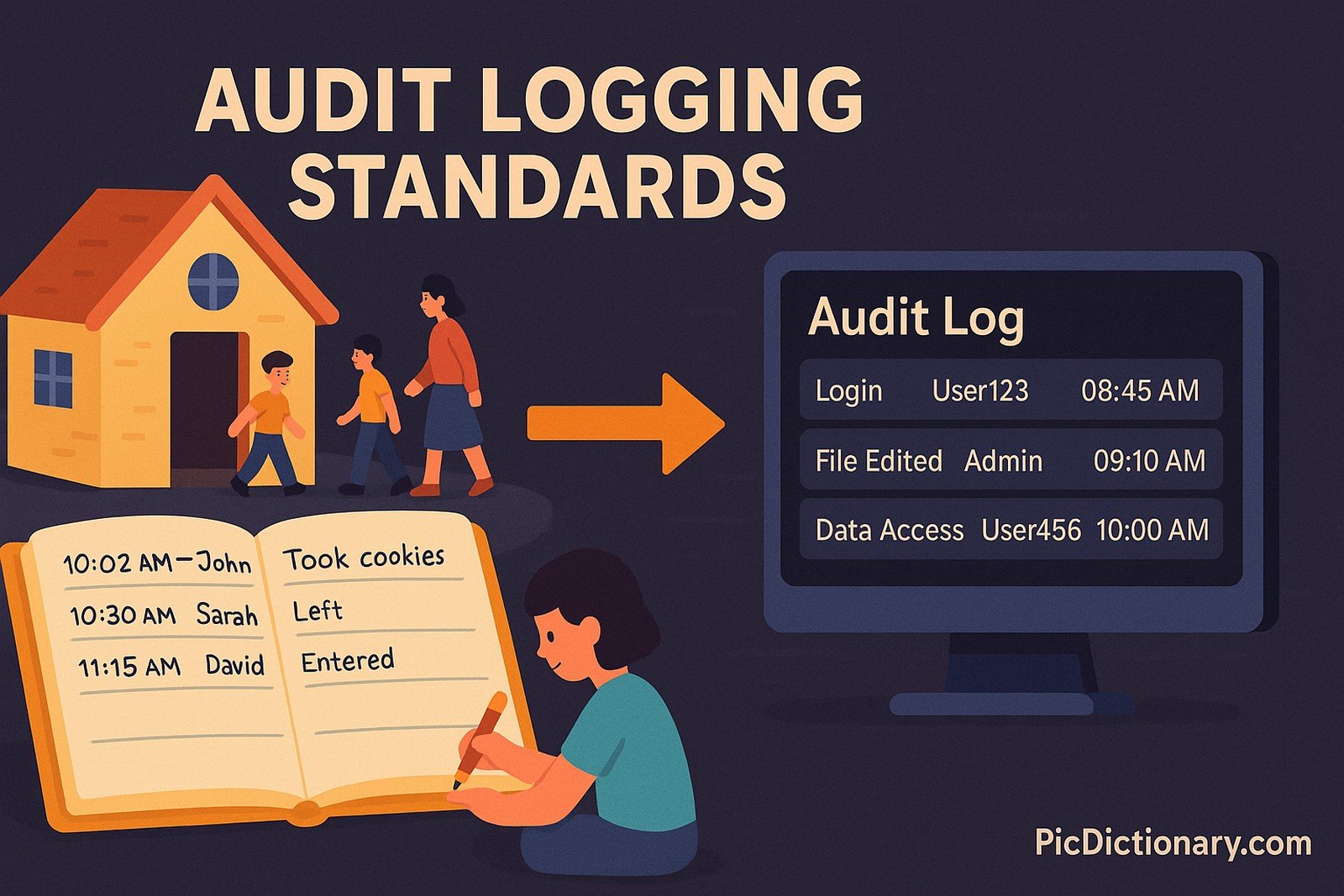
Audit Logging Standards Origin
The concept of audit logging originated in the early days of computing when organizations needed a way to track changes in their systems for accountability. As cybersecurity threats evolved, logging standards became essential for detecting and mitigating risks. The rise of regulatory compliance requirements in the late 20th century, such as HIPAA for healthcare and SOX for financial reporting, solidified the necessity of standardized logging practices.
Audit Logging Standards Etymology
The term “audit” originates from the Latin word audire, meaning “to hear,” as early audits involved listening to financial records being read aloud. “Logging” comes from the practice of recording events sequentially, similar to a captain’s log on a ship. Together, “audit logging” signifies the process of recording system activities for review and analysis.
Audit Logging Standards Usage Trends
With increasing cyber threats and data privacy regulations, audit logging standards have gained prominence across industries. Cloud computing, artificial intelligence, and remote work have further driven demand for robust logging mechanisms. Security frameworks now emphasize real-time log monitoring and automated analysis using machine learning to detect threats before they escalate.
Audit Logging Standards Usage
- Formal/Technical Tagging:
- Information Security
- Compliance & Governance
- Cybersecurity - Typical Collocations:
- "audit log retention policy"
- "real-time audit logging"
- "secure log storage"
- "log integrity verification"
Audit Logging Standards Examples in Context
- A financial institution must follow audit logging standards to track every transaction and detect fraud.
- Hospitals use audit logs to monitor who accesses patient records, ensuring compliance with HIPAA.
- IT teams in large corporations analyze audit logs to identify unauthorized access attempts and potential cyber threats.
Audit Logging Standards FAQ
- What are audit logging standards?
Audit logging standards define best practices for recording and maintaining system logs to ensure security and compliance. - Why are audit logs important?
They help detect security breaches, support forensic investigations, and ensure compliance with regulations. - What regulations require audit logging?
Regulations like GDPR, HIPAA, SOX, and PCI DSS mandate audit logging for security and compliance. - What should be included in an audit log?
An audit log should include timestamps, user actions, system events, and error messages. - How long should audit logs be retained?
Retention policies vary by industry, but logs are typically kept for 1-7 years based on compliance requirements. - How can audit logs be secured?
Logs should be encrypted, stored in tamper-proof systems, and regularly monitored for anomalies. - What tools are used for audit logging?
Common tools include Splunk, ELK Stack, and AWS CloudTrail. - Can audit logs be automated?
Yes, modern solutions use automated logging and AI-driven analysis to detect suspicious activities in real time. - What is real-time audit logging?
It’s a logging approach where system activities are recorded and analyzed instantly to detect threats faster. - How do businesses use audit logs for cybersecurity?
Businesses analyze audit logs to identify potential threats, prevent data breaches, and ensure compliance.
Audit Logging Standards Related Words
- Categories/Topics:
- Information Security
- Regulatory Compliance
- Digital Forensics
Did you know?
In 2013, a major data breach at a global retailer exposed over 40 million credit card records. A forensic investigation revealed that the attack could have been prevented if audit logs had been actively monitored. This event highlighted the importance of real-time audit logging in cybersecurity.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment