Cross-Site Scripting (XSS)

Quick Navigation:
- Cross-Site Scripting (XSS) Definition
- Cross-Site Scripting (XSS) Explained Easy
- Cross-Site Scripting (XSS) Origin
- Cross-Site Scripting (XSS) Etymology
- Cross-Site Scripting (XSS) Usage Trends
- Cross-Site Scripting (XSS) Usage
- Cross-Site Scripting (XSS) Examples in Context
- Cross-Site Scripting (XSS) FAQ
- Cross-Site Scripting (XSS) Related Words
Cross-Site Scripting (XSS) Definition
Cross-Site Scripting (XSS) is a type of security vulnerability in web applications that allows attackers to inject malicious scripts into web pages viewed by other users. These scripts can steal session cookies, deface websites, or redirect users to malicious sites. XSS typically exploits weaknesses in input validation and improper handling of user-generated content. It is classified into three main types: Stored XSS, Reflected XSS, and DOM-based XSS.
Cross-Site Scripting (XSS) Explained Easy
Imagine you're playing a multiplayer online game where players can send each other messages. Normally, you'd expect a message to just contain text, but what if someone sent a hidden command that could steal your game account? That’s how XSS works—hackers inject harmful code into websites, making them do things they weren’t supposed to.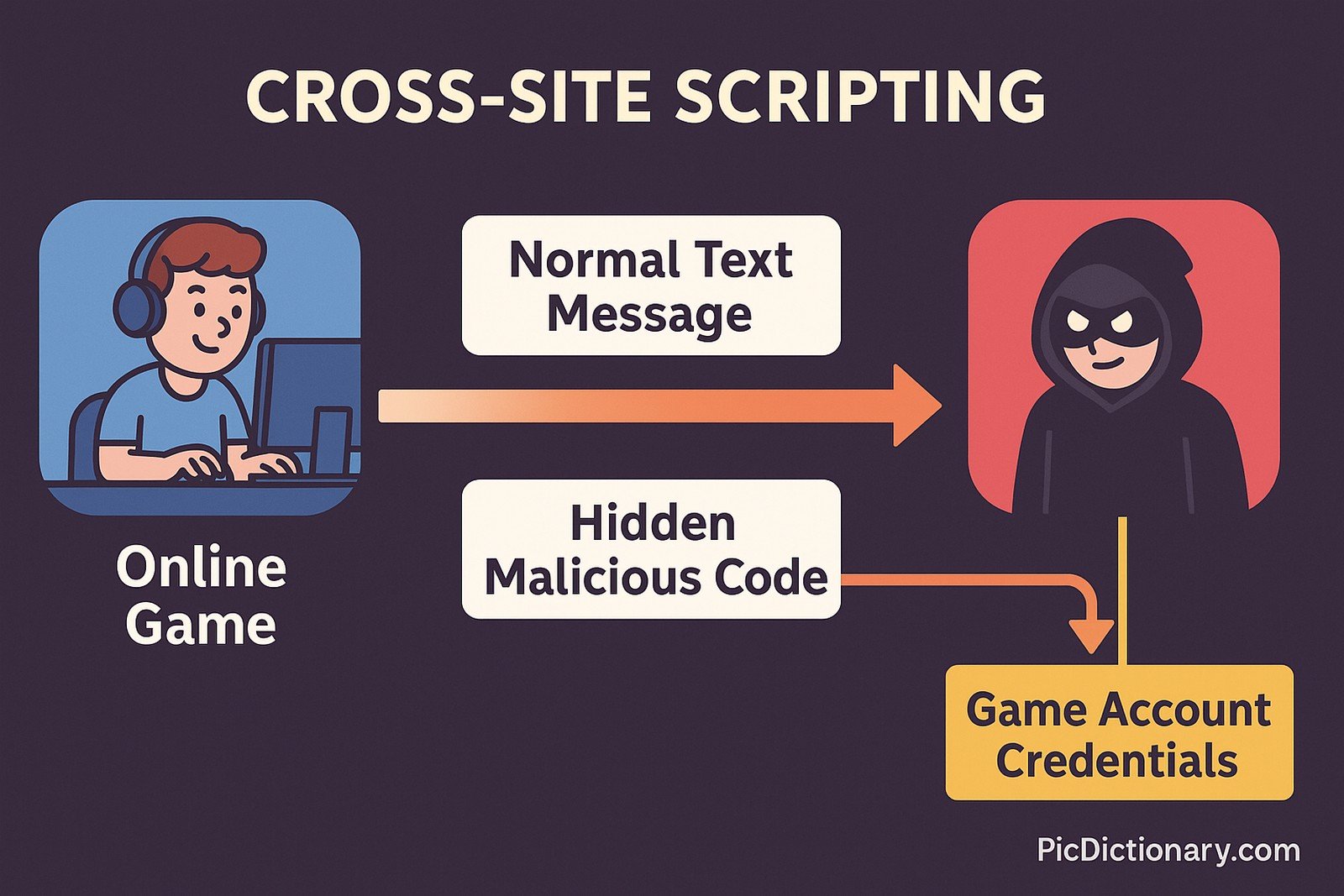
Cross-Site Scripting (XSS) Origin
The concept of injecting code into web applications dates back to the early days of the internet. XSS vulnerabilities became widespread in the late 1990s and early 2000s as dynamic websites began relying heavily on user-generated content without proper security measures.
Cross-Site Scripting (XSS) Etymology
The term "Cross-Site Scripting" originates from the vulnerability's ability to execute scripts across different web pages. While logically it should be "CSS" (Cross-Site Scripting), it was abbreviated as "XSS" to avoid confusion with Cascading Style Sheets (CSS).
Cross-Site Scripting (XSS) Usage Trends
With the rise of modern web applications, XSS has remained one of the most reported web vulnerabilities. Web frameworks and browsers now implement security features like Content Security Policy (CSP) and HTTP-only cookies to mitigate XSS risks. However, improper input sanitization still makes many applications vulnerable.
Cross-Site Scripting (XSS) Usage
- Formal/Technical Tagging:
- Web Security
- Cybersecurity
- Web Application Vulnerability - Typical Collocations:
- "XSS attack vector"
- "Mitigating XSS vulnerabilities"
- "XSS in JavaScript applications"
- "Cross-Site Scripting prevention techniques"
Cross-Site Scripting (XSS) Examples in Context
- A hacker injects an XSS payload into a website’s comment section, causing all visitors to execute the malicious script unknowingly.
- An online form fails to sanitize user input, allowing an attacker to steal session cookies through an XSS exploit.
- A social media post containing a malicious script leads to mass exploitation when users unknowingly click on it.
Cross-Site Scripting (XSS) FAQ
- What is Cross-Site Scripting (XSS)?
XSS is a security vulnerability that allows attackers to inject malicious scripts into web applications, affecting users. - What are the different types of XSS?
The three main types are Stored XSS, Reflected XSS, and DOM-based XSS. - How does XSS work?
XSS exploits weaknesses in input validation to inject malicious scripts, which are then executed by users’ browsers. - What are the dangers of XSS?
XSS can lead to session hijacking, website defacement, phishing attacks, and unauthorized data theft. - How can XSS be prevented?
Developers can prevent XSS by validating and sanitizing user input, using Content Security Policy (CSP), and employing frameworks that escape user input. - Is XSS still a threat in 2025?
Yes, despite security improvements, XSS remains a prevalent vulnerability in poorly secured applications. - How does CSP help in mitigating XSS?
CSP restricts which scripts can run on a webpage, blocking unauthorized execution of injected scripts. - Can XSS affect mobile applications?
Yes, web-based mobile apps using browsers or embedded web views can be vulnerable to XSS. - What’s the difference between XSS and SQL Injection?
XSS exploits user browsers, while SQL Injection targets database queries. - Are browsers equipped to block XSS?
Modern browsers have built-in security mechanisms like XSS filters, but these are not foolproof.
Cross-Site Scripting (XSS) Related Words
- Categories/Topics:
- Cybersecurity
- Web Development Security
- Online Threats
Did you know?
In 2005, a MySpace worm called "Samy" exploited an XSS vulnerability, adding over a million friends to a hacker's account in just one day. The attack demonstrated the power of XSS and led to major security reforms in social media platforms.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment