Endpoint Detection and Response (EDR)

Quick Navigation:
- Endpoint Detection and Response (EDR) Definition
- Endpoint Detection and Response (EDR) Explained Easy
- Endpoint Detection and Response (EDR) Origin
- Endpoint Detection and Response (EDR) Etymology
- Endpoint Detection and Response (EDR) Usage Trends
- Endpoint Detection and Response (EDR) Usage
- Endpoint Detection and Response (EDR) Examples in Context
- Endpoint Detection and Response (EDR) FAQ
- Endpoint Detection and Response (EDR) Related Words
Endpoint Detection and Response (EDR) Definition
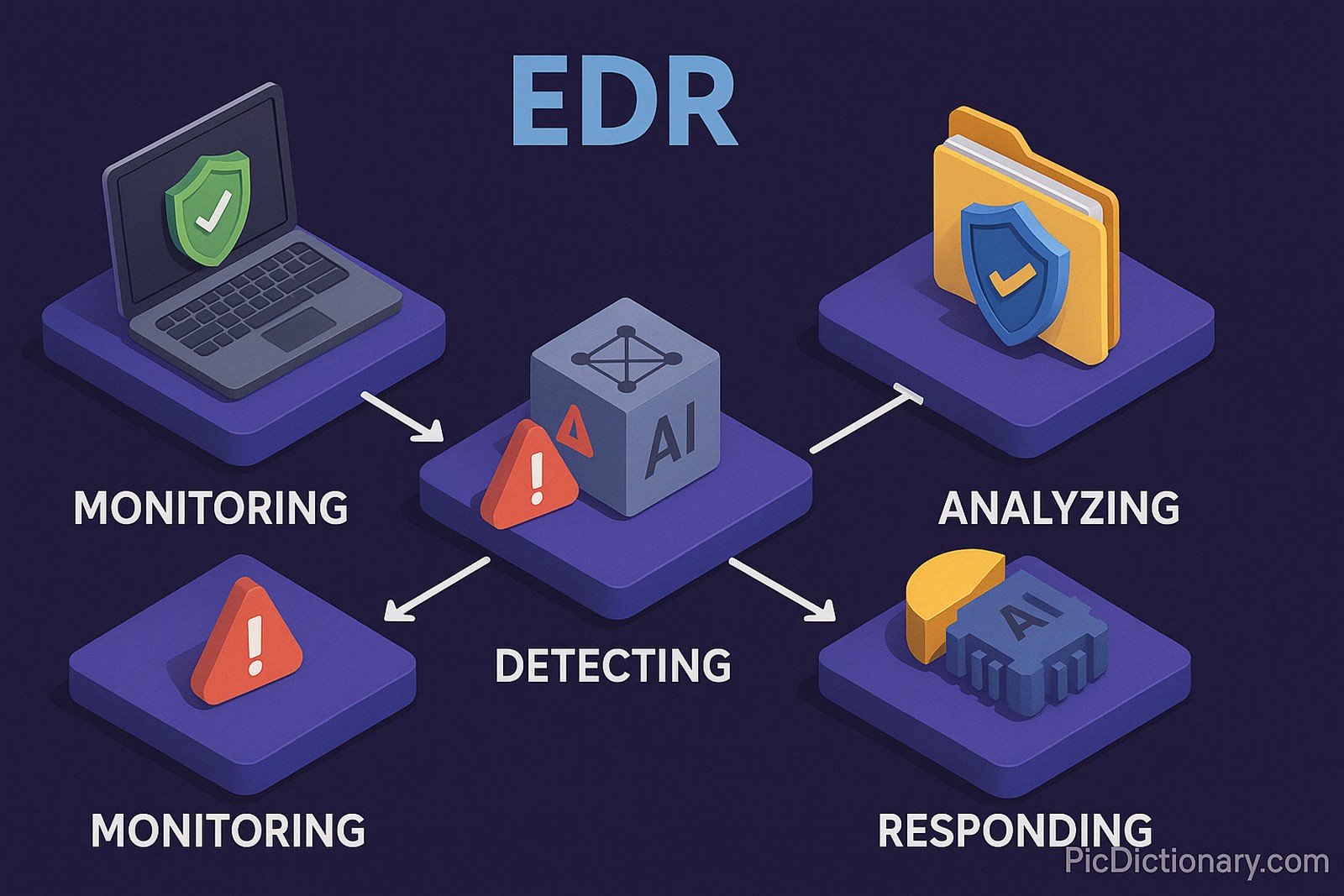
Endpoint Detection and Response (EDR) is a cybersecurity technology that continuously monitors and collects activity data from endpoints, detecting and responding to security threats in real-time. EDR solutions help organizations identify malicious behavior, mitigate attacks, and provide forensic analysis capabilities. These tools typically employ artificial intelligence (AI), behavior analytics, and automated threat intelligence to enhance security defenses.
Endpoint Detection and Response (EDR) Explained Easy
Think of EDR like a security guard for computers. Just like a guard watches over a building, EDR watches over computers and laptops to spot any bad activity. If something suspicious happens, it quickly investigates and stops any potential harm, making sure everything stays safe.
Endpoint Detection and Response (EDR) Origin
The concept of EDR emerged in the early 2010s as cyber threats became more sophisticated, requiring more advanced monitoring solutions. Traditional antivirus programs were insufficient in detecting evolving malware and cyberattacks, leading to the development of EDR systems that focus on endpoint security and continuous threat detection.
Endpoint Detection and Response (EDR) Etymology
The term "Endpoint Detection and Response" comes from "endpoint," referring to devices like computers and servers, and "detection and response," which describes the process of identifying and reacting to cyber threats.
Endpoint Detection and Response (EDR) Usage Trends
With the rise of remote work, cloud computing, and increasingly complex cyber threats, EDR has become a crucial part of enterprise security. Many companies are integrating EDR with Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) solutions to enhance overall security visibility. The demand for EDR solutions has surged, particularly in industries like finance, healthcare, and government, where data protection is critical.
Endpoint Detection and Response (EDR) Usage
- Formal/Technical Tagging:
- Cybersecurity
- Threat Detection
- Incident Response - Typical Collocations:
- "EDR solution implementation"
- "real-time EDR monitoring"
- "EDR and SIEM integration"
- "automated threat detection with EDR"
Endpoint Detection and Response (EDR) Examples in Context
- A company's IT team uses an EDR system to detect and respond to ransomware attempts before they cause damage.
- EDR helps financial institutions monitor their network endpoints for unusual login attempts and suspicious file modifications.
- By using an EDR solution, a hospital secures patient data from unauthorized access and cyber threats.
Endpoint Detection and Response (EDR) FAQ
- What is Endpoint Detection and Response (EDR)?
EDR is a cybersecurity technology that monitors, detects, and responds to threats on endpoint devices like computers and servers. - How does EDR differ from antivirus software?
Unlike traditional antivirus software, EDR provides real-time monitoring, behavioral analysis, and advanced threat response capabilities. - What are the key features of an EDR solution?
Features include real-time threat detection, automated response, forensic investigation tools, and integration with security platforms. - Why is EDR important for businesses?
EDR enhances security by detecting advanced threats, reducing response time, and improving overall cybersecurity resilience. - Can EDR prevent ransomware attacks?
Yes, EDR can detect and block ransomware activity before it spreads, minimizing damage. - How does EDR use AI in cybersecurity?
AI-driven EDR solutions analyze behavioral patterns to detect anomalies and predict potential security threats. - Is EDR suitable for small businesses?
Yes, many EDR solutions cater to small businesses by providing cost-effective and scalable security options. - How does EDR integrate with other security systems?
EDR can work alongside SIEM, XDR, and threat intelligence platforms for comprehensive cybersecurity protection. - What industries benefit the most from EDR?
Industries like finance, healthcare, government, and e-commerce benefit significantly from EDR’s real-time threat detection. - What is the future of EDR?
Future EDR solutions will leverage AI, machine learning, and cloud-native architectures to enhance automated security capabilities.
Endpoint Detection and Response (EDR) Related Words
- Categories/Topics:
- Cybersecurity
- Threat Intelligence
- Incident Response
Did you know?
EDR solutions played a critical role in mitigating large-scale cyberattacks like SolarWinds and WannaCry. By leveraging real-time monitoring and automated threat response, organizations using EDR were able to detect malicious activity before widespread damage occurred.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment