Malware Reversal

Quick Navigation:
- Malware Reversal Definition
- Malware Reversal Explained Easy
- Malware Reversal Origin
- Malware Reversal Etymology
- Malware Reversal Usage Trends
- Malware Reversal Usage
- Malware Reversal Examples in Context
- Malware Reversal FAQ
- Malware Reversal Related Words
Malware Reversal Definition
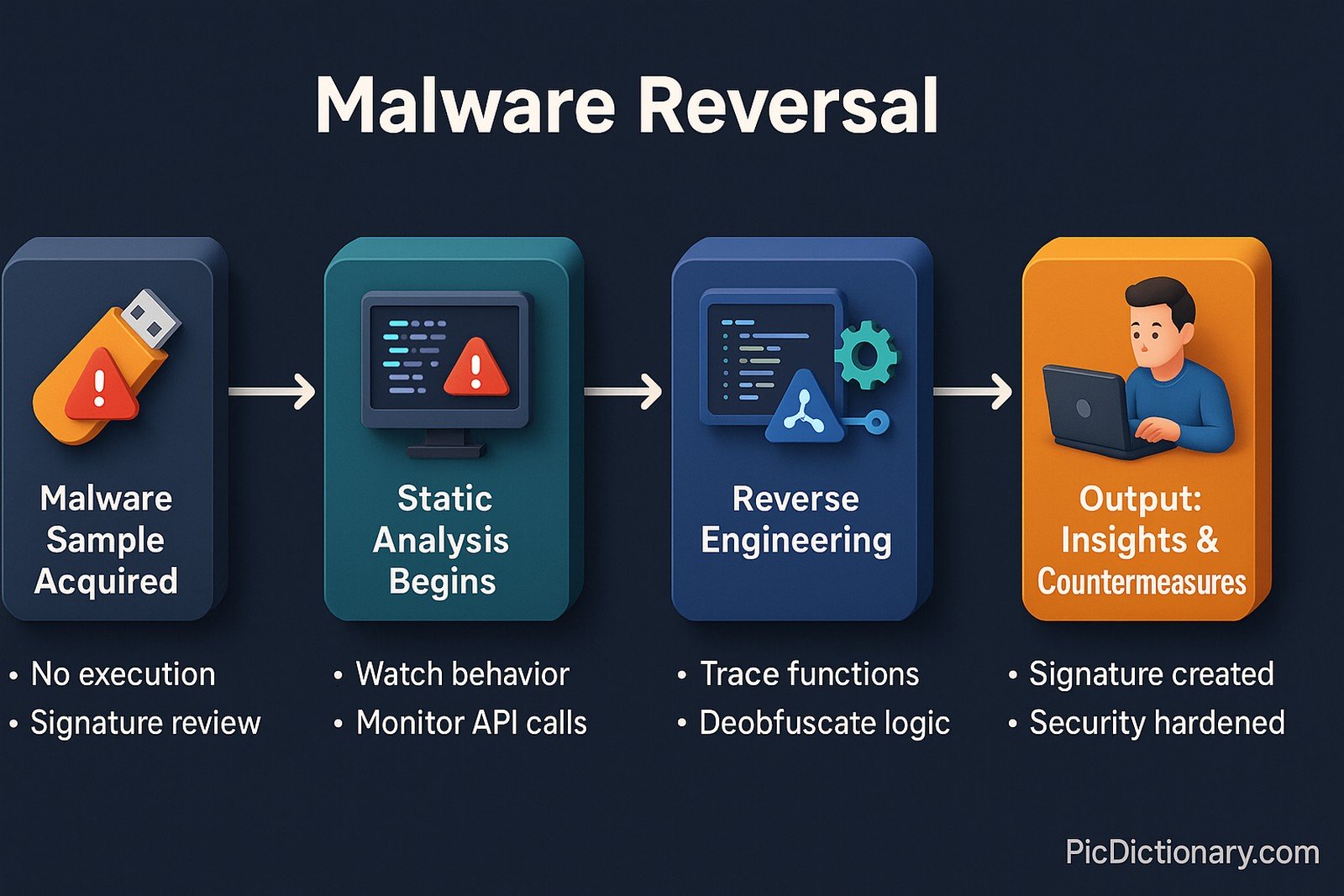
Malware reversal is the process of analyzing malicious software (malware) to understand its functionality, origin, and potential impact. It involves reverse engineering techniques, such as disassembling and debugging, to dissect the malware’s behavior, uncover hidden payloads, and develop effective countermeasures. Cybersecurity experts use malware reversal to detect vulnerabilities, create antivirus signatures, and strengthen security defenses against cyber threats.
Malware Reversal Explained Easy
Imagine you find a locked treasure chest, but you don’t have the key. To open it, you carefully take it apart, studying how the lock works so you can open it without the key. Malware reversal is similar—security experts take apart a virus or malicious program to see how it works and find ways to stop it.
Malware Reversal Origin
The origins of malware reversal trace back to the early days of computer viruses in the 1980s, when cybersecurity researchers began dissecting malicious programs to understand their effects. With the rise of advanced malware in the 2000s, malware reversal became an essential tool for cybersecurity defense.
Malware Reversal Etymology
The term “malware reversal” is derived from two words: “malware,” a combination of “malicious” and “software,” and “reversal,” indicating the process of reversing the malware’s code execution to analyze its behavior.
Malware Reversal Usage Trends
As cyber threats evolve, malware reversal has become more sophisticated. The demand for malware analysis has increased due to rising ransomware attacks, financial fraud, and nation-state cyber espionage. Today, security firms, government agencies, and ethical hackers use automated tools and AI-powered techniques for faster malware reversal and threat detection.
Malware Reversal Usage
- Formal/Technical Tagging:
- Cybersecurity
- Digital Forensics
- Reverse Engineering - Typical Collocations:
- "malware reversal analysis"
- "reverse engineering malware"
- "disassembling malicious code"
- "debugging malware behavior"
Malware Reversal Examples in Context
- Cybersecurity researchers use malware reversal to identify new strains of ransomware before they spread.
- Government agencies rely on malware reversal to uncover cyber espionage campaigns.
- Ethical hackers perform malware reversal on compromised systems to analyze the attack methods used by cybercriminals.
Malware Reversal FAQ
- What is malware reversal?
Malware reversal is the process of analyzing and dissecting malicious software to understand its behavior and develop security measures against it. - Why is malware reversal important?
It helps security professionals detect malware threats, develop antivirus solutions, and protect sensitive data from cyberattacks. - What tools are used for malware reversal?
Common tools include IDA Pro, Ghidra, OllyDbg, and Wireshark for analyzing and debugging malware. - Is malware reversal legal?
Yes, as long as it is performed for cybersecurity defense and ethical research. However, unauthorized use of malware reversal can violate laws. - How do experts reverse malware?
They use disassemblers, debuggers, and sandbox environments to analyze the malware’s code, execution patterns, and network behavior. - What types of malware are analyzed in malware reversal?
Trojan horses, ransomware, worms, spyware, and rootkits are commonly analyzed through reversal techniques. - Can malware reversal stop cyberattacks?
While it cannot stop attacks directly, it helps in developing patches, intrusion detection systems, and security tools to prevent future incidents. - What skills are needed for malware reversal?
A deep understanding of assembly language, operating system internals, cryptography, and cybersecurity principles is essential. - How long does malware reversal take?
The process can take hours to weeks, depending on the complexity of the malware and its obfuscation techniques. - Who uses malware reversal?
Cybersecurity researchers, forensic analysts, government agencies, and ethical hackers use malware reversal to analyze cyber threats.
Malware Reversal Related Words
- Categories/Topics:
- Cybersecurity
- Reverse Engineering
- Digital Forensics
Did you know?
The infamous Stuxnet worm, which targeted Iran’s nuclear program, was first analyzed through malware reversal. Experts discovered that it was specifically designed to disrupt industrial control systems, highlighting the power of malware analysis in uncovering cyber-espionage operations.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment