Man-in-the-Middle Attack
 (Representational Image | Source: Dall-E)
(Representational Image | Source: Dall-E)
Quick Navigation:
- Man-in-the-Middle Attack Definition
- Man-in-the-Middle Attack Explained Easy
- Man-in-the-Middle Attack Origin
- Man-in-the-Middle Attack Etymology
- Man-in-the-Middle Attack Usage Trends
- Man-in-the-Middle Attack Usage
- Man-in-the-Middle Attack Examples in Context
- Man-in-the-Middle Attack FAQ
- Man-in-the-Middle Attack Related Words
Man-in-the-Middle Attack Definition
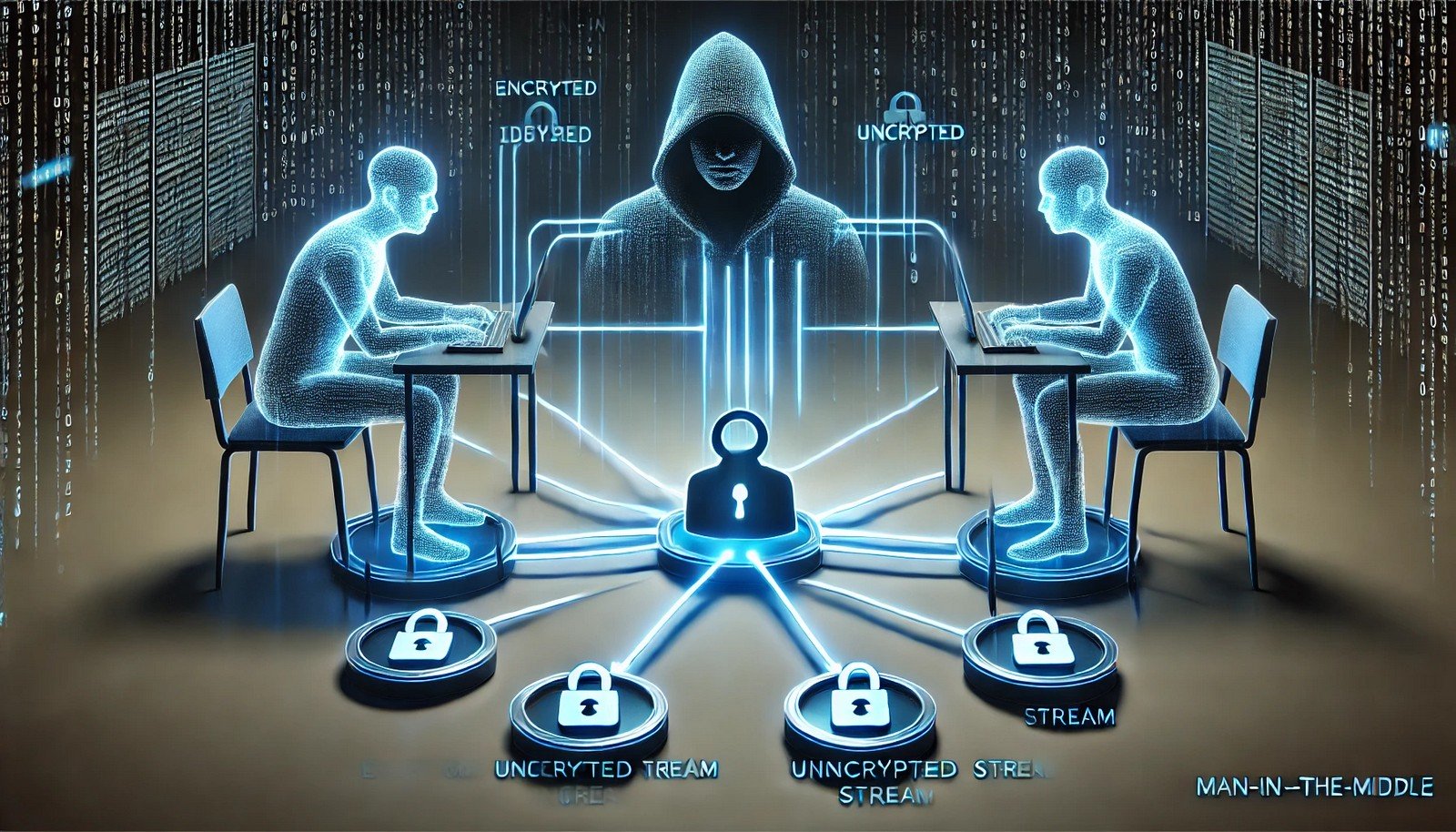
A Man-in-the-Middle (MitM) attack is a cyber threat where an attacker intercepts and potentially alters communications between two parties without their knowledge. This allows the attacker to eavesdrop, steal sensitive data, or inject malicious content. Common attack vectors include unsecured Wi-Fi networks, compromised routers, and session hijacking. MitM attacks are particularly dangerous in financial transactions, login credentials, and confidential communications.
Man-in-the-Middle Attack Explained Easy
Imagine you're passing notes with a friend in class. If someone secretly intercepts the note, reads it, and then sends a slightly changed version to your friend, you wouldn't even know. A Man-in-the-Middle attack works like this in the digital world—hackers sneak in between your communication and alter or steal your information without you realizing it.
Man-in-the-Middle Attack Origin
The concept of intercepting and altering communication traces back to military strategies where adversaries would disrupt enemy signals. With the rise of digital communication, this tactic evolved into cybercrime, especially targeting online banking, encrypted messaging, and secure logins.
Man-in-the-Middle Attack Etymology
The phrase "Man-in-the-Middle" describes the attacker's position—sitting undetected between two communicating entities to manipulate their conversation.
Man-in-the-Middle Attack Usage Trends
With the expansion of online services, MitM attacks have become more prevalent. Hackers exploit weak encryption, public Wi-Fi vulnerabilities, and compromised SSL/TLS certificates. Businesses and individuals now prioritize encrypted communication channels, VPNs, and two-factor authentication to counteract these attacks.
Man-in-the-Middle Attack Usage
- Formal/Technical Tagging:
- Cybersecurity
- Network Security
- Cryptography - Typical Collocations:
- "MitM attack on public Wi-Fi"
- "Session hijacking vulnerability"
- "SSL stripping in a Man-in-the-Middle attack"
Man-in-the-Middle Attack Examples in Context
- A hacker sets up a rogue Wi-Fi hotspot in a coffee shop, capturing login credentials from unsuspecting users.
- Attackers intercept and alter financial transactions between a user and a bank by exploiting a vulnerable network.
- Cybercriminals manipulate DNS requests, redirecting users to fake websites that steal their credentials.
Man-in-the-Middle Attack FAQ
- What is a Man-in-the-Middle attack?
A cybersecurity attack where an attacker secretly intercepts and manipulates communication between two parties. - How do hackers perform a Man-in-the-Middle attack?
Common methods include spoofing Wi-Fi networks, DNS hijacking, and SSL stripping. - Can a VPN protect against MitM attacks?
Yes, VPNs encrypt traffic, making it difficult for attackers to intercept data. - Are public Wi-Fi networks vulnerable to MitM attacks?
Yes, unsecured networks are prime targets for these attacks. - What is SSL stripping in a MitM attack?
It’s a technique where attackers downgrade HTTPS connections to HTTP, making data transmissions unencrypted. - How can I detect a Man-in-the-Middle attack?
Warning signs include unexpected SSL/TLS certificate errors and frequent connection drops. - Are Man-in-the-Middle attacks common in mobile devices?
Yes, especially when users connect to unsecured networks without encryption. - How can organizations prevent MitM attacks?
By enforcing HTTPS, using strong encryption, and implementing endpoint security measures. - What are some real-world examples of MitM attacks?
Notable cases include banking credential theft via fake Wi-Fi hotspots and email interception for financial fraud. - Is end-to-end encryption effective against MitM attacks?
Yes, because only the intended recipients can decrypt the communication.
Man-in-the-Middle Attack Related Words
- Categories/Topics:
- Cybersecurity
- Encryption
- Network Security
Did you know?
In 2013, hackers used a sophisticated Man-in-the-Middle attack to target European diplomats by intercepting their encrypted communications. This incident highlighted the importance of end-to-end encryption and secure authentication protocols in government and corporate cybersecurity.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment