Public Key Infrastructure (PKI)

Quick Navigation:
- Public Key Infrastructure (PKI) Definition
- Public Key Infrastructure (PKI) Explained Easy
- Public Key Infrastructure (PKI) Origin
- Public Key Infrastructure (PKI) Etymology
- Public Key Infrastructure (PKI) Usage Trends
- Public Key Infrastructure (PKI) Usage
- Public Key Infrastructure (PKI) Examples in Context
- Public Key Infrastructure (PKI) FAQ
- Public Key Infrastructure (PKI) Related Words
Public Key Infrastructure (PKI) Definition
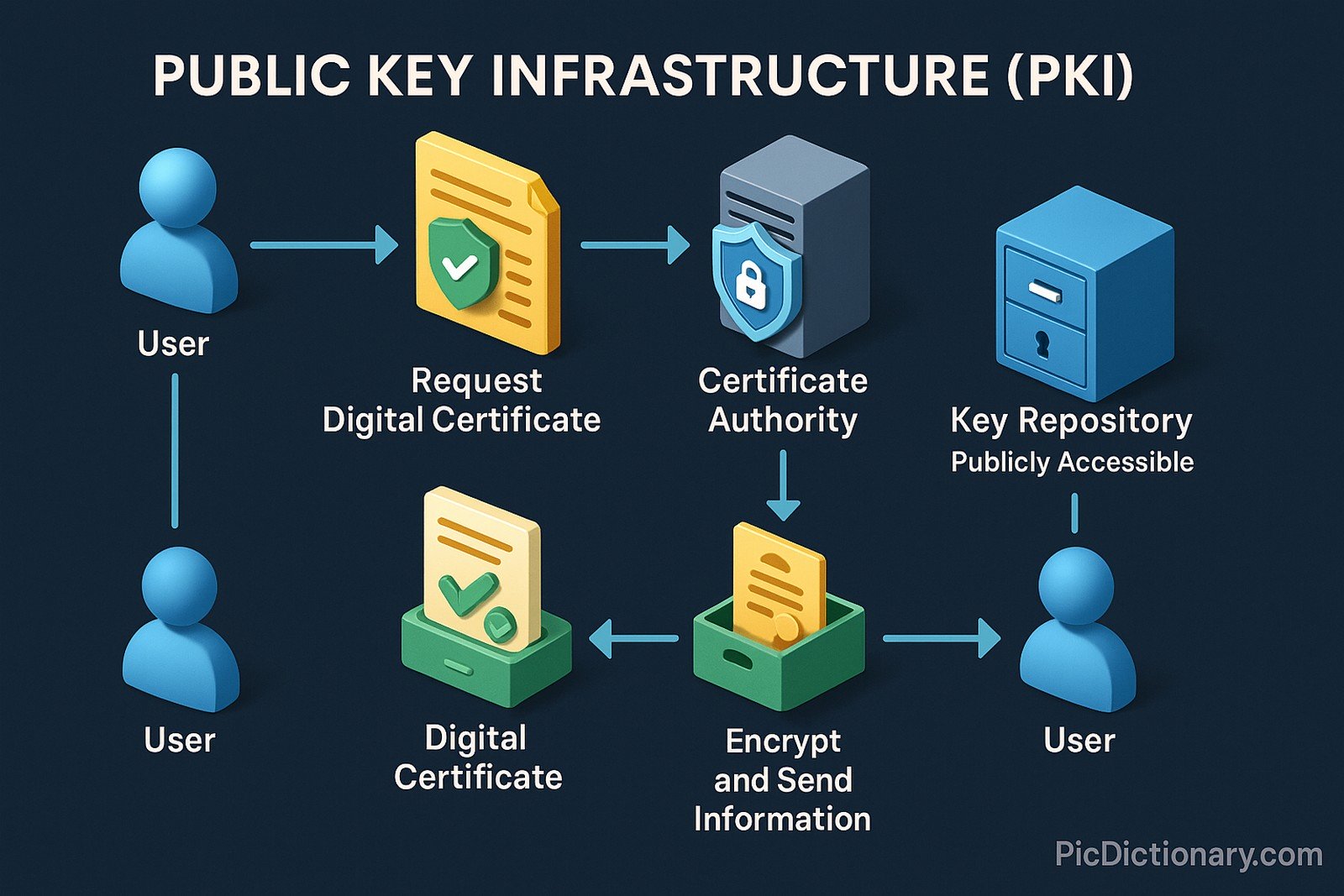
Public Key Infrastructure (PKI) is a framework of policies, hardware, software, and standards used to create, manage, distribute, and revoke digital certificates and public-private key pairs. PKI ensures secure communication over the internet through encryption and authentication. It is the foundation of secure web browsing, email encryption, and digital signatures, using technologies like SSL/TLS, cryptographic hashing, and asymmetric cryptography. PKI consists of Certificate Authorities (CAs), Registration Authorities (RAs), and key repositories, which work together to verify identities and manage trust in digital transactions.
Public Key Infrastructure (PKI) Explained Easy
Imagine you have a secret diary that you want to share with your best friend, but you don’t want anyone else to read it. You create a special lock and give your friend a key that only fits that lock. That way, only they can open it! PKI works the same way—it creates secure locks (encryption) and gives trusted people the right keys (digital certificates) to access information safely online.
Public Key Infrastructure (PKI) Origin
PKI originated from early cryptographic research in the 1970s, with public-key cryptography being pioneered by Whitfield Diffie and Martin Hellman. Their work laid the foundation for asymmetric encryption, later adopted into modern security frameworks. The first commercial PKI implementations emerged in the 1990s, driven by the need for secure online communications and transactions.
Public Key Infrastructure (PKI) Etymology
The term "infrastructure" refers to an underlying system that supports operations, while "public key" refers to the cryptographic system using paired public and private keys for encryption and authentication.
Public Key Infrastructure (PKI) Usage Trends
PKI adoption has increased with the rise of cybersecurity threats and regulatory requirements. It is widely used in securing websites via SSL/TLS, encrypting emails, authenticating devices in IoT networks, and protecting digital identities in cloud computing. The expansion of zero-trust security models and remote work has further accelerated PKI deployment.
Public Key Infrastructure (PKI) Usage
- Formal/Technical Tagging:
- Cybersecurity
- Cryptography
- Digital Authentication - Typical Collocations:
- "PKI certificate authority"
- "public key encryption"
- "PKI authentication mechanism"
- "digital certificate management"
Public Key Infrastructure (PKI) Examples in Context
- Banks use PKI to secure online banking transactions, ensuring that only authorized users can access their accounts.
- Websites use SSL/TLS certificates, which rely on PKI, to encrypt data between users and web servers.
- Email encryption services use PKI to prevent unauthorized access to sensitive messages.
Public Key Infrastructure (PKI) FAQ
- What is Public Key Infrastructure (PKI)?
PKI is a system for managing digital certificates and encryption keys to secure online communication. - How does PKI work?
PKI works by using a Certificate Authority (CA) to issue digital certificates that verify identities, enabling secure encryption and authentication. - Why is PKI important?
PKI is essential for securing sensitive data, preventing cyberattacks, and enabling trust in digital transactions. - What are the key components of PKI?
PKI consists of Certificate Authorities (CAs), Registration Authorities (RAs), digital certificates, and key management systems. - How does PKI help secure websites?
PKI enables SSL/TLS encryption, ensuring secure data transfer between websites and users. - What industries use PKI?
PKI is used in finance, healthcare, government, and cloud computing for secure authentication and encryption. - Can PKI be hacked?
While PKI is highly secure, attacks like certificate fraud and private key theft can compromise its integrity. Proper management and security policies mitigate these risks. - What is a digital certificate?
A digital certificate is an electronic document issued by a CA that verifies an entity’s identity and enables encrypted communication. - What is the difference between a public and private key?
A public key is shared openly for encryption, while a private key is kept secret and used for decryption. - How do I obtain a PKI certificate?
You can get a PKI certificate from a trusted Certificate Authority (CA) by submitting identity verification documents.
Public Key Infrastructure (PKI) Related Words
- Categories/Topics:
- Cybersecurity
- Digital Certificates
- Encryption
Did you know?
In 2008, researchers discovered a major flaw in MD5 hashing, allowing attackers to create a rogue Certificate Authority (CA) using PKI. This demonstrated the importance of stronger cryptographic standards and led to the widespread adoption of SHA-2 hashing for digital certificates.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment