Secure Logging Mechanisms
Quick Navigation:
- Secure Logging Mechanisms Definition
- Secure Logging Mechanisms Explained Easy
- Secure Logging Mechanisms Origin
- Secure Logging Mechanisms Etymology
- Secure Logging Mechanisms Usage Trends
- Secure Logging Mechanisms Usage
- Secure Logging Mechanisms Examples in Context
- Secure Logging Mechanisms FAQ
- Secure Logging Mechanisms Related Words
Secure Logging Mechanisms Definition
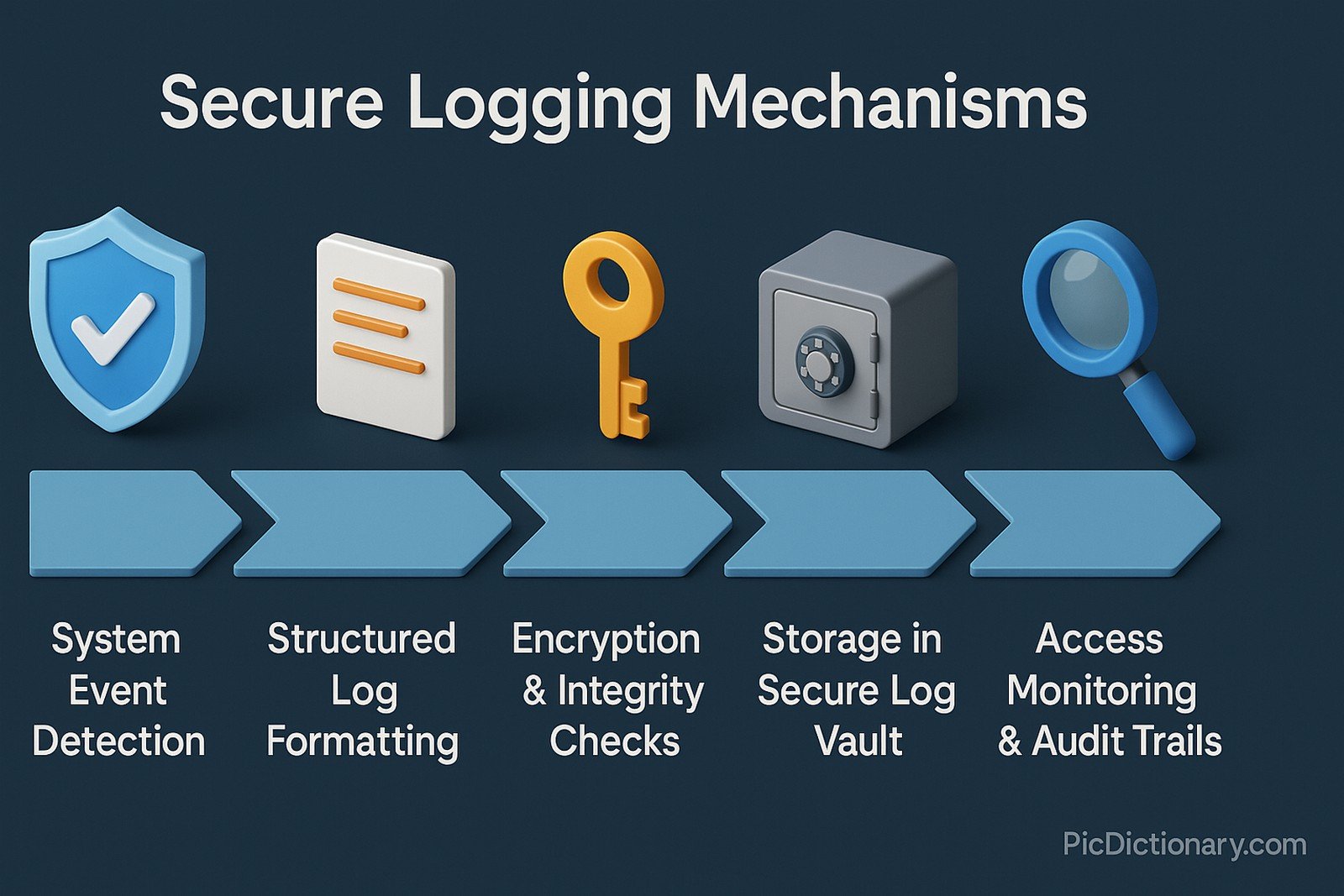
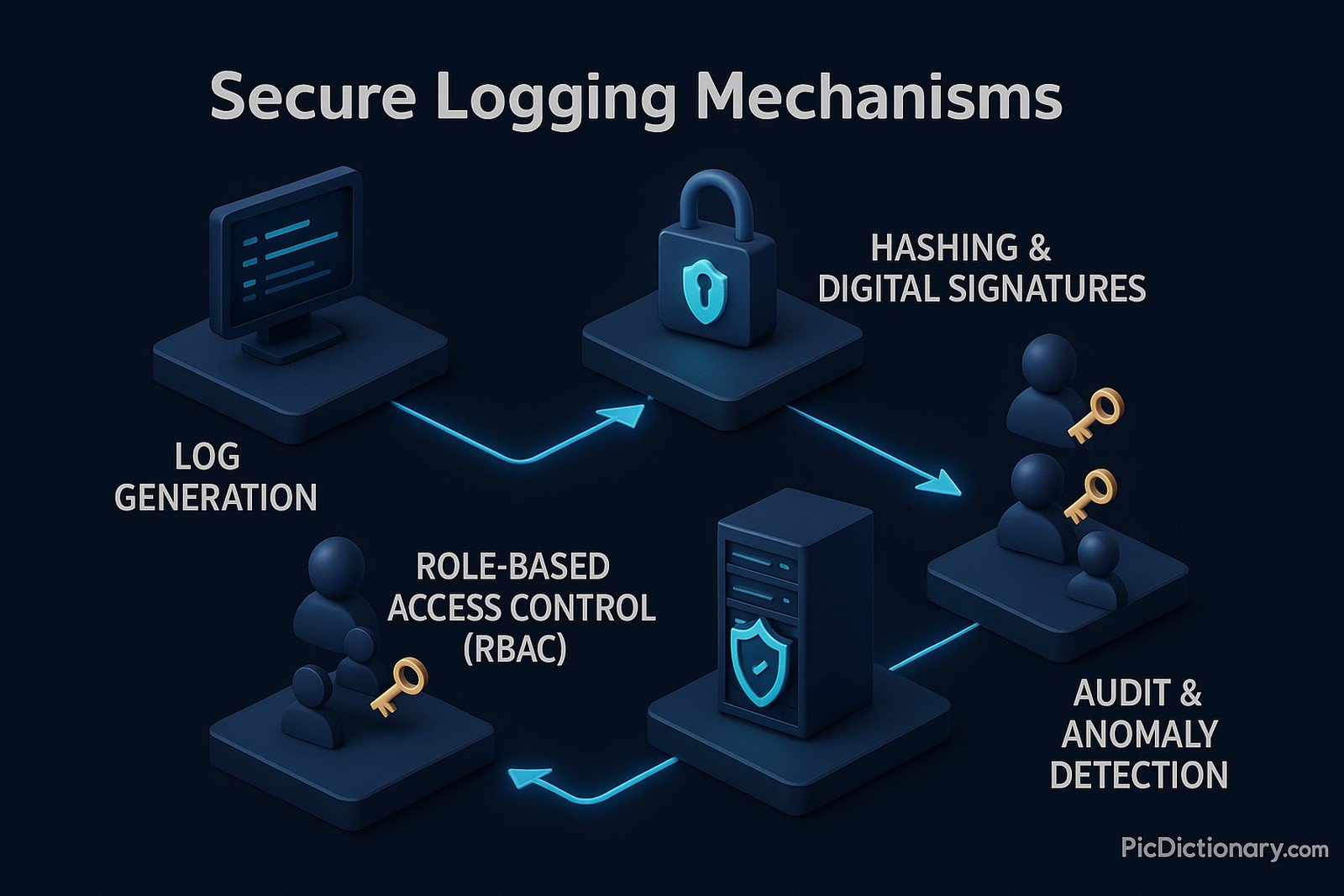
Secure logging mechanisms refer to the structured processes and technologies used to securely record, store, and manage logs while ensuring their integrity, confidentiality, and availability. These mechanisms are crucial in cybersecurity, helping organizations track system activities, detect anomalies, and comply with regulatory requirements. Techniques such as cryptographic hashing, digital signatures, and role-based access control (RBAC) ensure that logs are tamper-resistant and accessible only to authorized users.
Secure Logging Mechanisms Explained Easy
Imagine writing in a diary that no one else should read or change. To keep it safe, you use a special lock and sign every page so that if someone tries to change anything, you’ll know. Secure logging mechanisms work similarly by keeping records safe, making sure only the right people can read them, and preventing tampering.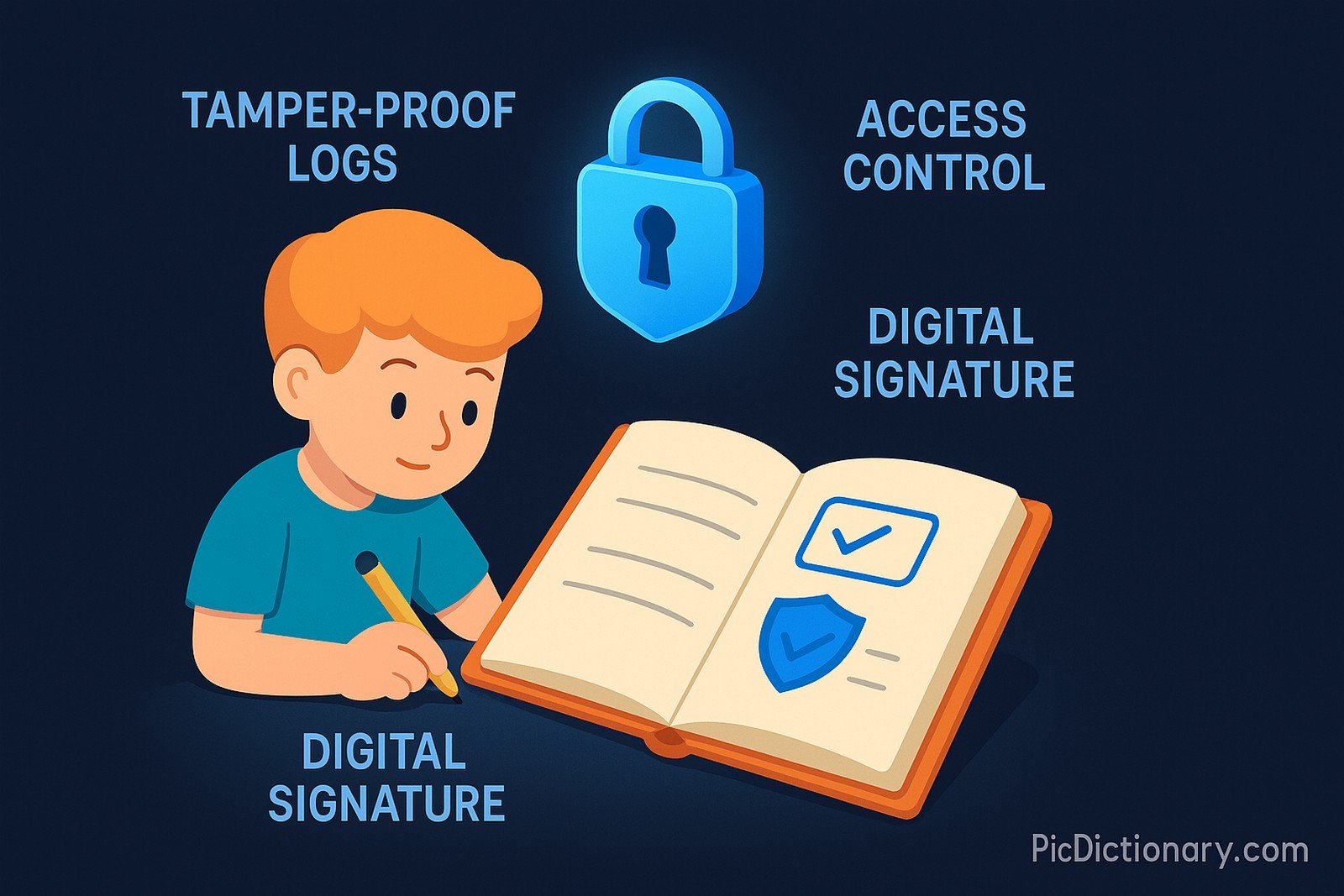
Secure Logging Mechanisms Origin
The need for secure logging arose with the rise of computer systems and networks, particularly as cybersecurity threats increased. Early computer systems had simple logging mechanisms, but as hacking and data breaches became more sophisticated, the necessity for advanced security features in logging evolved.
Secure Logging Mechanisms Etymology
The term “secure logging” combines “secure,” meaning protected from unauthorized access, and “logging,” which refers to systematically recording events or transactions in a system.
Secure Logging Mechanisms Usage Trends
With increasing cyber threats, secure logging has become a critical component of cybersecurity frameworks. Modern security regulations, such as GDPR, HIPAA, and PCI-DSS, emphasize robust logging practices. Industries like banking, healthcare, and cloud computing rely on advanced logging solutions to detect cyberattacks, maintain compliance, and enhance forensic investigations.
Secure Logging Mechanisms Usage
- Formal/Technical Tagging: Cybersecurity, System Monitoring, Compliance
- Typical Collocations:
- “secure logging infrastructure”
- “cryptographically signed logs”
- “audit log integrity”
- “tamper-proof logging system”
Secure Logging Mechanisms Examples in Context
- Banking Systems: Secure logging helps detect unauthorized transactions by recording every financial operation with timestamps and cryptographic validation.
- Cloud Computing: Cloud providers use secure logging to track user activity and detect breaches.
- Healthcare: Hospitals employ secure logs to protect patient data, ensuring compliance with health regulations.
Secure Logging Mechanisms FAQ
- Why are secure logging mechanisms important?
Secure logs help detect security breaches, maintain compliance, and prevent unauthorized access to system records. - How do cryptographic signatures enhance logging security?
They ensure that logs cannot be altered without detection, maintaining integrity. - What is the role of encryption in secure logging?
Encryption protects sensitive log data from unauthorized access. - How do secure logs aid in forensic investigations?
They provide an unalterable record of system events, helping analysts trace security incidents. - What industries require secure logging?
Finance, healthcare, government, and cloud services heavily depend on secure logs. - Can secure logging prevent insider threats?
While it can’t prevent insider threats entirely, it helps detect suspicious activity. - What are audit logs in secure logging?
Audit logs track user actions, helping in regulatory compliance and security monitoring. - How does role-based access control (RBAC) improve secure logging?
It ensures only authorized personnel can access or manage logs. - What’s the difference between centralized and decentralized logging?
Centralized logging stores logs in one location, while decentralized logging distributes them for redundancy and security. - Are secure logs useful in real-time monitoring?
Yes, they enable real-time threat detection and response.
Secure Logging Mechanisms Related Words
- Categories/Topics: Cybersecurity, Information Security, System Administration
Did you know?
In 2020, a major cyberattack targeted a cloud service provider, exposing millions of records. However, secure logging mechanisms helped investigators trace the attack and identify vulnerabilities, showcasing the importance of robust log security.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment