Audit Trail

Quick Navigation:
- Audit Trail Definition
- Audit Trail Explained Easy
- Audit Trail Origin
- Audit Trail Etymology
- Audit Trail Usage Trends
- Audit Trail Usage
- Audit Trail Examples in Context
- Audit Trail FAQ
- Audit Trail Related Words
Audit Trail Definition
An audit trail is a chronological record of changes made to a system, process, or document, providing evidence of activities for security, compliance, and troubleshooting. In computer software, an audit trail logs user actions, system modifications, and transaction histories to ensure accountability and traceability. These logs are crucial in industries like finance, healthcare, and cybersecurity, where maintaining an accurate history of data access and alterations is vital for compliance with regulatory standards such as GDPR, HIPAA, and SOX.
Audit Trail Explained Easy
Imagine you have a diary where you record everything you do in a day. If someone asks what you did at 3 PM, you can check your diary and tell them exactly. An audit trail works the same way for computers and systems—it keeps a record of who did what and when, so if something goes wrong, people can find out what happened and fix it.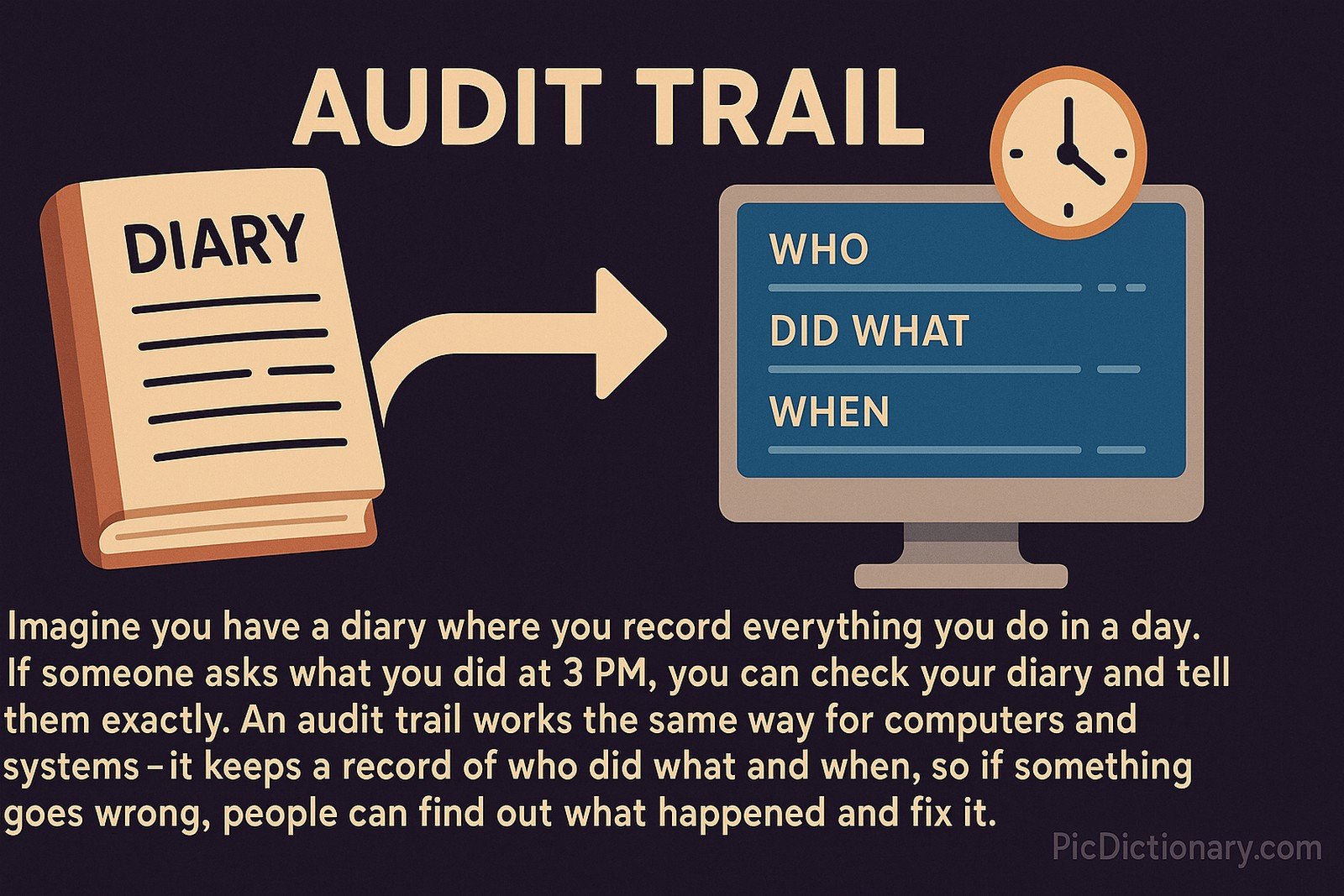
Audit Trail Origin
The concept of audit trails has existed since the early days of record-keeping in business and government. With the rise of computing in the 20th century, digital audit trails became a critical component of security and compliance efforts. They were first widely adopted in financial systems to ensure the integrity of transactions and later expanded to IT systems, databases, and enterprise applications.
Audit Trail Etymology
The term "audit" originates from the Latin audire, meaning "to hear," as early financial audits involved listening to oral accounts of transactions. "Trail" refers to the sequential path left by recorded events, signifying a traceable history of actions taken.
Audit Trail Usage Trends
With increasing cybersecurity threats and regulatory scrutiny, audit trails have become more important than ever. Organizations leverage them for forensic analysis, fraud detection, and risk management. Modern implementations include blockchain-based audit trails, AI-driven anomaly detection, and cloud-based logging solutions, ensuring more robust security and data integrity across industries.
Audit Trail Usage
- Formal/Technical Tagging:
- Cybersecurity
- Data Integrity
- Compliance & Governance - Typical Collocations:
- "Maintain an audit trail"
- "Secure audit logs"
- "Regulatory audit trail compliance"
- "Digital audit trail for transactions"
Audit Trail Examples in Context
- A hospital maintains an audit trail of patient record accesses to ensure compliance with HIPAA regulations.
- Financial institutions use audit trails to track every transaction and detect fraudulent activity.
- An IT administrator reviews the system's audit trail after a security breach to determine the source of unauthorized access.
Audit Trail FAQ
- What is an audit trail used for?
An audit trail provides a historical record of system changes, user actions, and transactions for security, compliance, and accountability. - Why is an audit trail important?
It helps organizations detect security breaches, comply with regulations, and track unauthorized changes. - How is an audit trail maintained?
Organizations use automated logging systems to track and securely store audit records in databases or log management platforms. - What industries require audit trails?
Finance, healthcare, government, IT, and legal sectors rely on audit trails for security and compliance. - What is the difference between an audit log and an audit trail?
An audit log is a single record of an event, while an audit trail is a chronological sequence of multiple records forming a complete history. - How does an audit trail enhance cybersecurity?
It helps detect unauthorized access, identify security breaches, and provide forensic evidence for investigations. - Can an audit trail be tampered with?
If not properly secured, audit trails can be altered, which is why encryption and access controls are critical. - What role does an audit trail play in financial transactions?
It ensures transaction transparency, detects fraud, and helps in compliance with financial regulations. - Are audit trails required by law?
Many regulations, including GDPR, HIPAA, and SOX, mandate audit trails for compliance. - What technologies support audit trails?
Blockchain, artificial intelligence, cloud logging services, and security information and event management (SIEM) systems enhance audit trail capabilities.
Audit Trail Related Words
- Categories/Topics:
- Compliance & Governance
- Cybersecurity
- Financial Auditing
Did you know?
In 2016, the Democratic National Committee (DNC) suffered a cyberattack that led to the leak of sensitive emails. Investigators relied on audit trail logs to trace the origin of the breach, highlighting the crucial role audit trails play in forensic cybersecurity investigations.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment