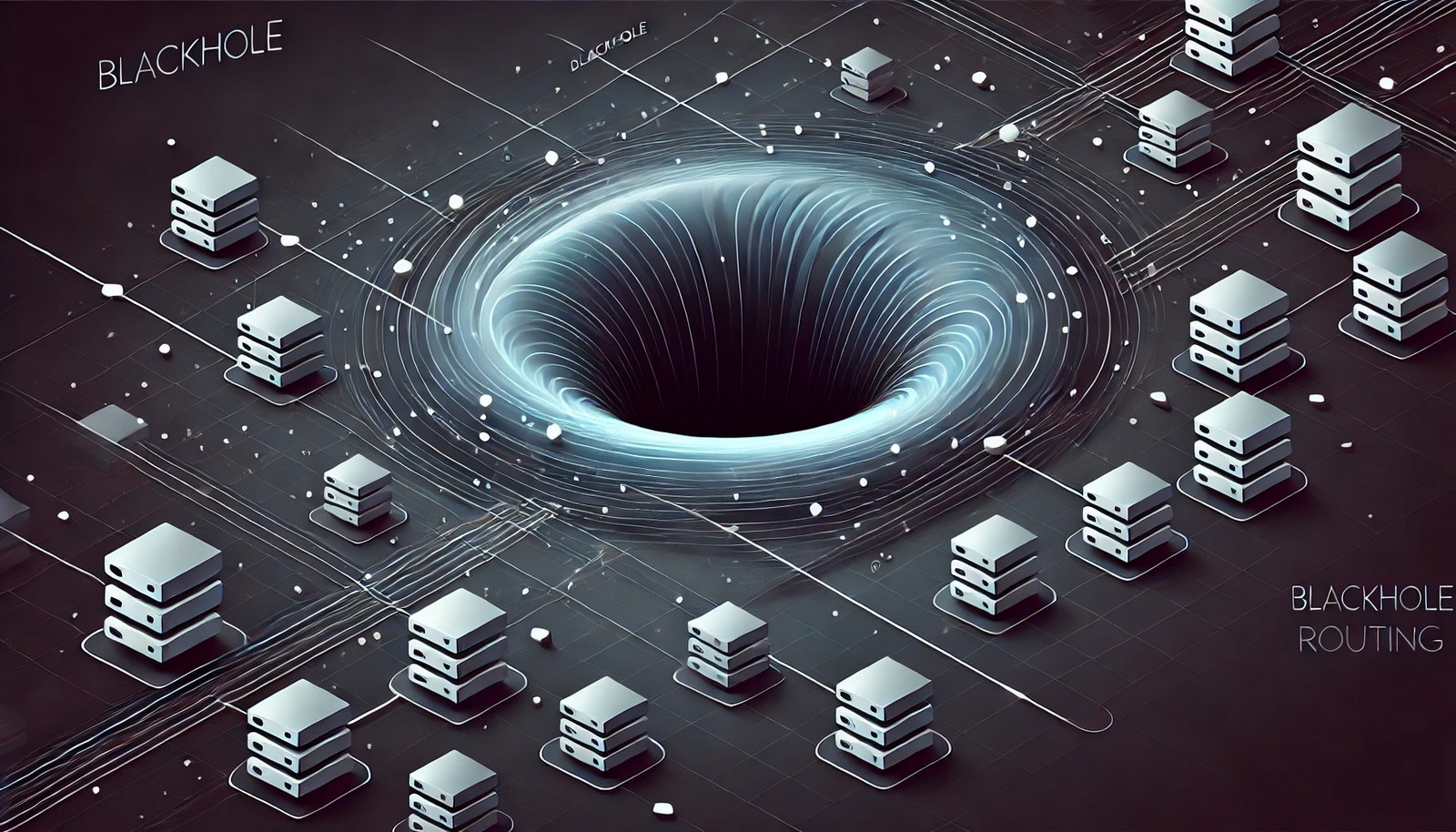
Blackhole Routing
 (Representational Image | Source: Dall-E)
(Representational Image | Source: Dall-E)
Quick Navigation:
- Blackhole Routing Definition
- Blackhole Routing Explained Easy
- Blackhole Routing Origin
- Blackhole Routing Etymology
- Blackhole Routing Usage Trends
- Blackhole Routing Usage
- Blackhole Routing Examples in Context
- Blackhole Routing FAQ
- Blackhole Routing Related Words
Blackhole Routing Definition
Blackhole routing is a network security technique designed to discard unwanted or malicious traffic by directing it to a non-existent destination. This method helps prevent cyber threats such as Distributed Denial-of-Service (DDoS) attacks by nullifying malicious traffic before it reaches its target.
Blackhole Routing Explained Easy
Imagine a mailbox that instantly vaporizes junk mail before it reaches your home. Blackhole routing works the same way—when harmful data tries to reach a server, the network redirects it into a digital void, preventing any damage.
Blackhole Routing Origin
The concept of blackhole routing was developed as a defensive network security strategy to combat cyberattacks, especially DDoS attacks. As digital threats increased, network administrators sought methods to eliminate malicious traffic before it could impact infrastructure.
Blackhole Routing Etymology
The term "blackhole routing" is derived from the idea of black holes in space, where matter disappears beyond the event horizon. Similarly, blackhole routing ensures that unwanted data is dropped without response.
Blackhole Routing Usage Trends
With the rise in cyber threats, blackhole routing has become an essential tool for internet service providers (ISPs) and enterprises to safeguard networks. Automated blackhole routing solutions integrated with real-time threat intelligence have made this technique more effective.
Blackhole Routing Usage
- Formal/Technical Tagging:
- Network Security
- Cyber Defense
- DDoS Mitigation - Typical Collocations:
- "Blackhole routing strategy"
- "BGP blackhole routing"
- "Traffic nullification using blackhole routing"
Blackhole Routing Examples in Context
- A company facing a DDoS attack implements blackhole routing to filter out harmful traffic before it reaches its servers.
- ISPs use automated blackhole routing to prevent large-scale network congestion caused by malicious traffic.
- Cybersecurity teams deploy blackhole routing policies to isolate infected devices and prevent the spread of malware.
Blackhole Routing FAQ
- What is blackhole routing?
Blackhole routing is a cybersecurity technique used to drop malicious traffic before it reaches a target system. - How does blackhole routing prevent DDoS attacks?
By directing excessive traffic into a digital void, blackhole routing prevents attackers from overwhelming a network. - Is blackhole routing permanent?
No, it is typically implemented dynamically and removed once the threat subsides. - Can blackhole routing impact legitimate traffic?
Yes, misconfigurations can cause unintended disruptions, highlighting the need for precise implementation. - What role does BGP play in blackhole routing?
Border Gateway Protocol (BGP) enables ISPs and enterprises to implement blackhole routing efficiently.
Blackhole Routing Related Words
- Categories/Topics:
- Network Security
- Cybersecurity
- Internet Infrastructure
Did you know?
During massive cyberattacks, ISPs sometimes implement blackhole routing on entire IP ranges to protect infrastructure, though this can occasionally block legitimate users.
Authors | Arjun Vishnu | @ArjunAndVishnu

PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.
I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.













Comments (0)
Comments powered by CComment