Cross-Site Request Forgery (CSRF)

Quick Navigation:
- Cross-Site Request Forgery (CSRF) Definition
- Cross-Site Request Forgery (CSRF) Explained Easy
- Cross-Site Request Forgery (CSRF) Origin
- Cross-Site Request Forgery (CSRF) Etymology
- Cross-Site Request Forgery (CSRF) Usage Trends
- Cross-Site Request Forgery (CSRF) Usage
- Cross-Site Request Forgery (CSRF) Examples in Context
- Cross-Site Request Forgery (CSRF) FAQ
- Cross-Site Request Forgery (CSRF) Related Words
Cross-Site Request Forgery (CSRF) Definition
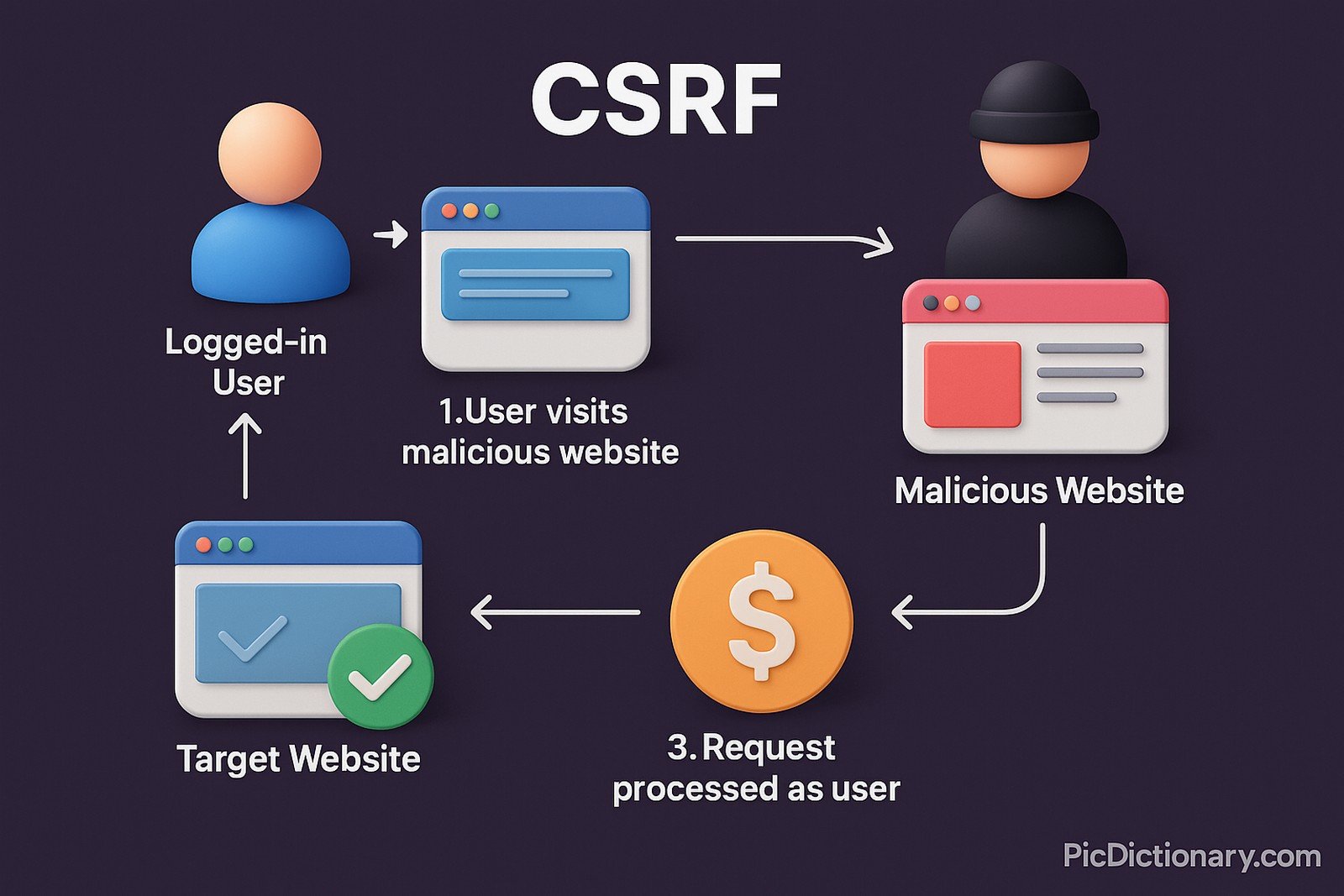
Cross-Site Request Forgery (CSRF) is a type of web security vulnerability where an attacker tricks a user into making unintended requests to a web application. This happens when a malicious actor forces an authenticated user to perform actions they did not intend, such as changing account settings, transferring funds, or submitting forms. CSRF exploits the trust that a website has in the user’s browser, typically through unauthorized requests sent via cookies or authentication tokens.
Cross-Site Request Forgery (CSRF) Explained Easy
Imagine you give your friend a signed blank check. If they decide to withdraw money without asking you, they are misusing your trust. CSRF works the same way—hackers trick websites into thinking that a user wants to take an action when they actually don’t, just because they are already logged in.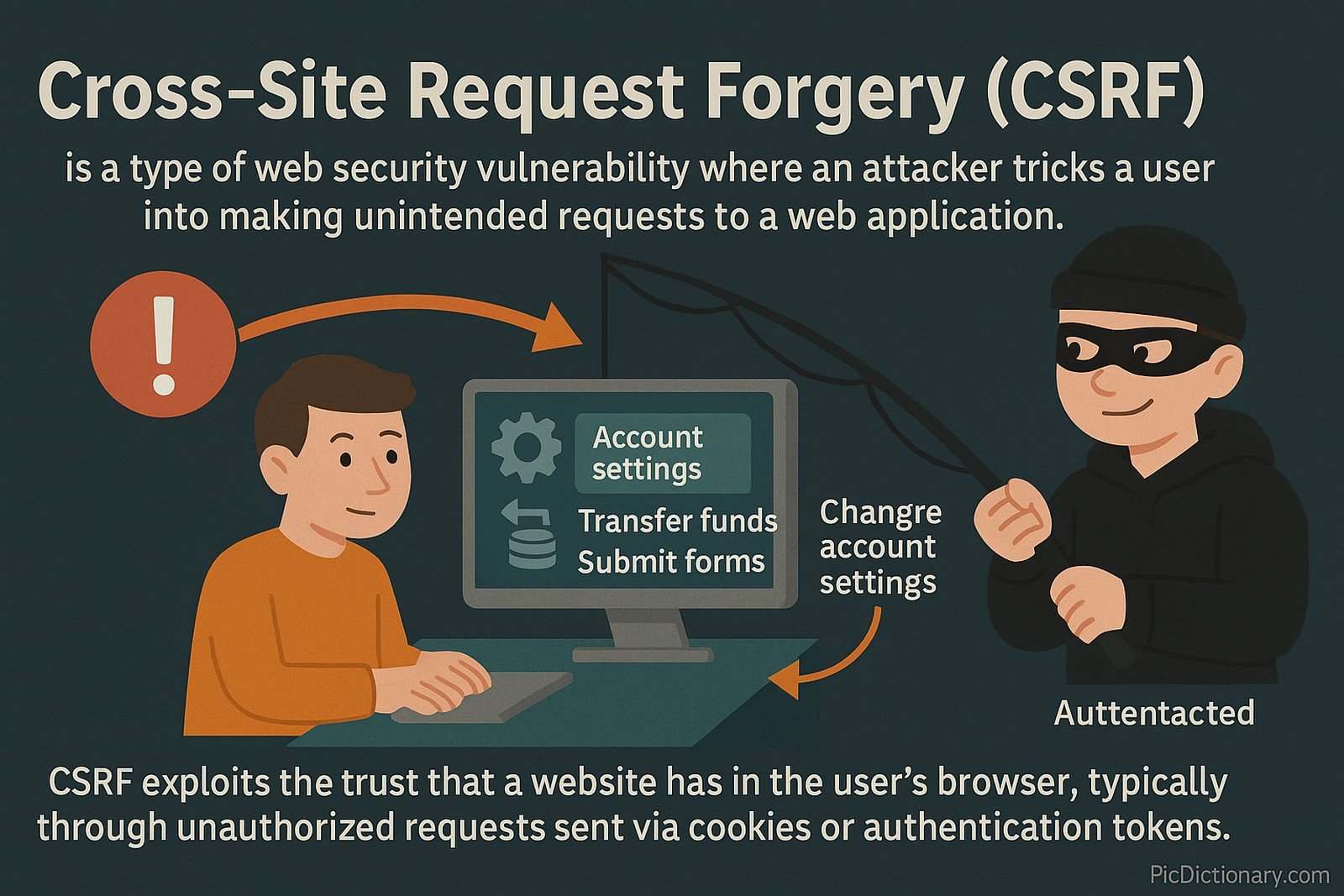
Cross-Site Request Forgery (CSRF) Origin
CSRF attacks have existed since the early days of web applications, with major security discussions emerging in the 2000s. As websites began using authentication cookies to maintain user sessions, attackers realized they could exploit these cookies to execute unauthorized commands on behalf of users.
Cross-Site Request Forgery (CSRF) Etymology
The term "Cross-Site Request Forgery" comes from the nature of the attack—it involves making unauthorized requests across different sites while impersonating a user.
Cross-Site Request Forgery (CSRF) Usage Trends
With the rise of complex web applications and cloud services, CSRF attacks have remained a security concern. However, modern frameworks and security measures like CSRF tokens, SameSite cookies, and improved browser security policies have significantly reduced the risk.
Cross-Site Request Forgery (CSRF) Usage
- Formal/Technical Tagging:
- Web Security
- Cybersecurity
- Authentication Vulnerabilities - Typical Collocations:
- "CSRF attack vector"
- "CSRF token protection"
- "CSRF exploit"
- "mitigating CSRF risks"
Cross-Site Request Forgery (CSRF) Examples in Context
- A banking website without CSRF protection allows attackers to create a hidden form that transfers money from a logged-in user’s account.
- A social media platform with poor security implementation lets attackers post messages on behalf of users without their consent.
- A vulnerable website allows attackers to change a user’s email or password by tricking them into clicking on a malicious link.
Cross-Site Request Forgery (CSRF) FAQ
- What is Cross-Site Request Forgery (CSRF)?
CSRF is an attack where unauthorized commands are executed on behalf of an authenticated user. - How does CSRF work?
Attackers craft malicious requests that trick a user’s browser into executing unintended actions on trusted websites. - What are common examples of CSRF attacks?
Changing account settings, transferring funds, or submitting forms without user consent. - How can CSRF be prevented?
Using CSRF tokens, enforcing SameSite cookies, and implementing strong user authentication. - Why is CSRF dangerous?
It allows attackers to manipulate a user's session, potentially leading to financial loss or data breaches. - Is CSRF still a problem today?
While less common due to modern security measures, poorly secured applications remain vulnerable. - What’s the difference between CSRF and XSS?
CSRF tricks a user into performing unintended actions, while XSS injects malicious scripts into a website. - Do all websites need CSRF protection?
Any web application that relies on authentication should implement CSRF mitigation techniques. - What is a CSRF token?
A unique, random value included in requests to verify they are intentional and not forged. - Can CSRF attacks be detected?
Security audits and web application firewalls can help identify and prevent CSRF vulnerabilities.
Cross-Site Request Forgery (CSRF) Related Words
- Categories/Topics:
- Cybersecurity
- Web Security
- Authentication
- Web Application Security
Did you know?
One of the most infamous CSRF attacks occurred in 2008 when Samy Kamkar exploited a vulnerability in MySpace to create a self-replicating worm that added over one million friends to his account. This attack demonstrated how CSRF could be used for large-scale exploitation in social media and beyond.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment