Encryption Key Rotation
 (Representational Image | Source: Dall-E)
(Representational Image | Source: Dall-E)
Quick Navigation:
- Encryption Key Rotation Definition
- Encryption Key Rotation Explained Easy
- Encryption Key Rotation Origin
- Encryption Key Rotation Etymology
- Encryption Key Rotation Usage Trends
- Encryption Key Rotation Usage
- Encryption Key Rotation Examples in Context
- Encryption Key Rotation FAQ
- Encryption Key Rotation Related Words
Encryption Key Rotation Definition
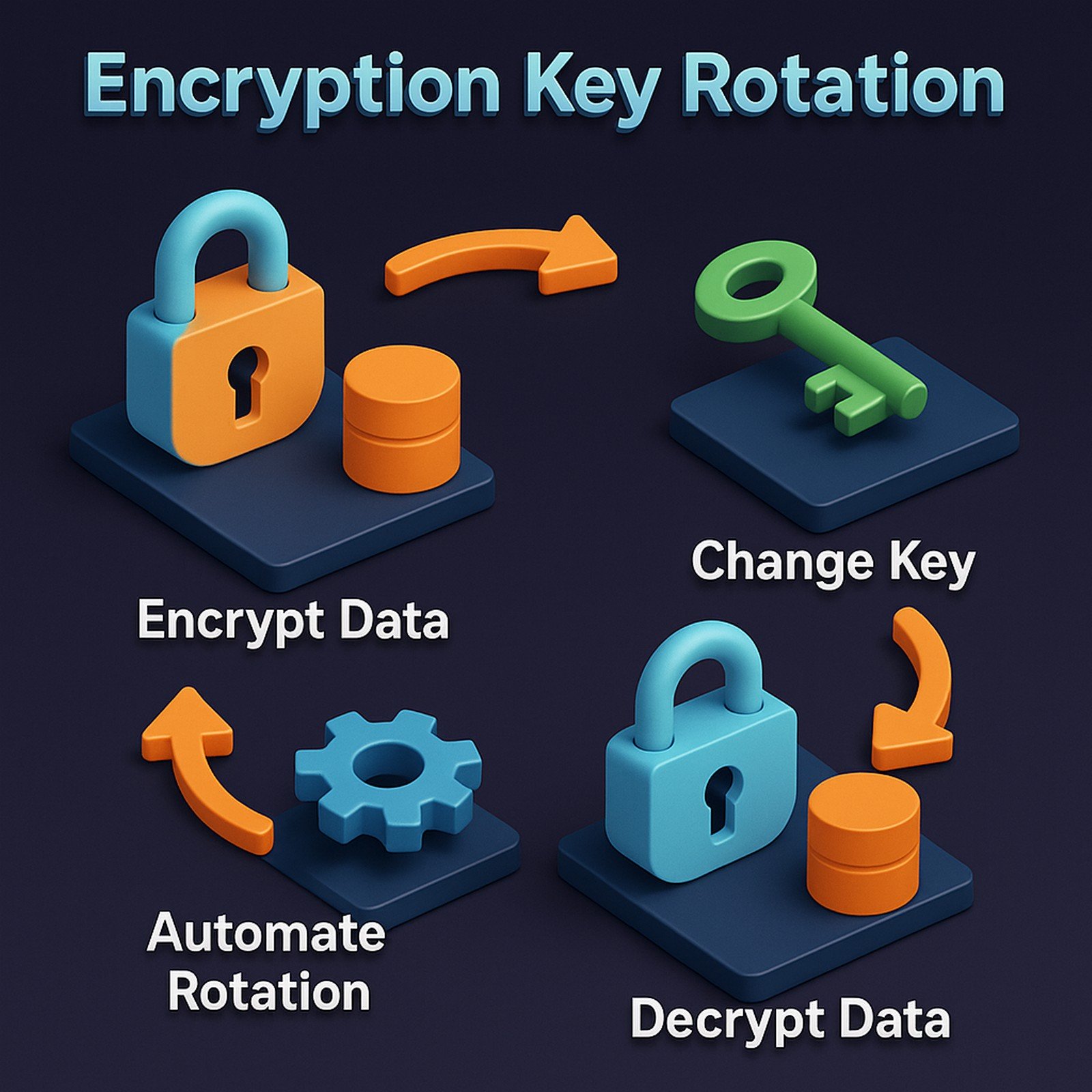
Encryption key rotation is a security practice that involves periodically changing cryptographic keys used to encrypt and decrypt data. This helps minimize the risk of compromised keys, ensuring continued data protection. Organizations automate key rotation to maintain security policies and compliance standards.
Encryption Key Rotation Explained Easy
Imagine you have a secret diary that you lock with a key. If someone gets that key, they can read your secrets. Instead of keeping the same key forever, you change it often so no one can use an old key to open your diary. Encryption key rotation works the same way—it regularly changes digital locks to keep information safe.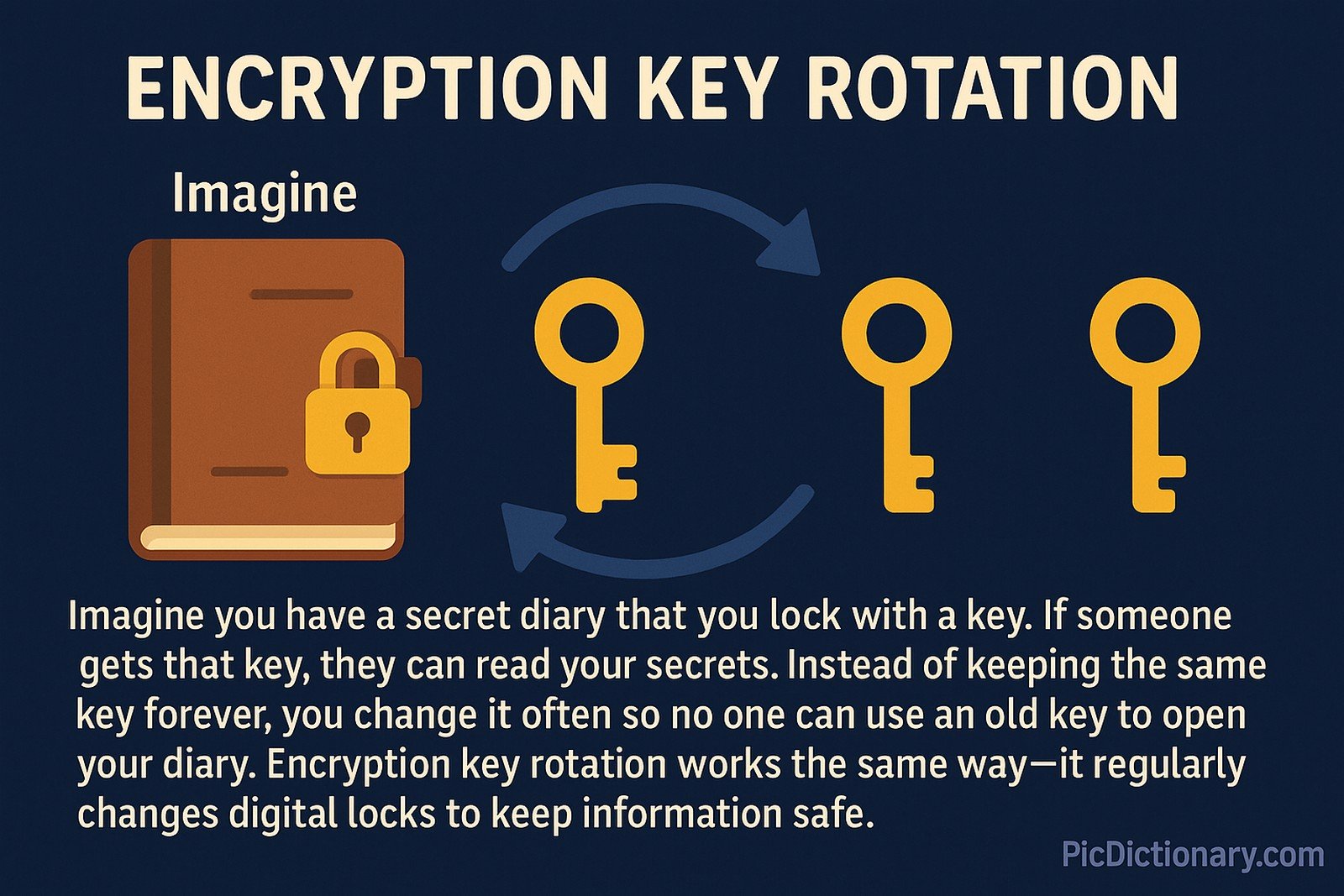
Encryption Key Rotation Origin
The concept of rotating encryption keys emerged alongside modern cryptography and cybersecurity needs. Early computer security practices in the 1970s and 1980s introduced key management to protect sensitive data.
Encryption Key Rotation Etymology
The phrase "encryption key rotation" combines three terms:
- Encryption - from Greek "kryptós" (hidden), refers to securing data.
- Key - a metaphor from physical locks, represents the digital code used to encrypt and decrypt data.
- Rotation - signifies the periodic replacement of the key.
Encryption Key Rotation Usage Trends
With increasing cyber threats, industries like finance, healthcare, and cloud computing have adopted strict encryption key rotation policies. Regulatory standards such as PCI DSS, GDPR, and HIPAA mandate key rotation to prevent data breaches.
Encryption Key Rotation Usage
- Formal/Technical Tagging:
- Cybersecurity
- Cryptography
- Data Protection - Typical Collocations:
- "automated encryption key rotation"
- "key rotation policy compliance"
- "rotating encryption keys for security"
- "time-based key rotation schedule"
Encryption Key Rotation Examples in Context
- A bank uses automated encryption key rotation to protect customer transaction data from cyber threats.
- Cloud service providers enable encryption key rotation to ensure secure data storage and regulatory compliance.
- An enterprise implements key rotation after a security breach to prevent unauthorized access with compromised keys.
Encryption Key Rotation FAQ
- What is encryption key rotation?
Encryption key rotation is the process of periodically changing cryptographic keys to enhance security. - Why is encryption key rotation important?
It prevents unauthorized access by ensuring old or compromised keys are no longer usable. - How often should encryption keys be rotated?
This depends on security policies, but common intervals include every 30, 60, or 90 days. - What are the methods of key rotation?
Key rotation can be time-based, event-based, or manual, depending on organizational needs. - Is key rotation required by law?
Yes, regulations like PCI DSS and GDPR mandate key rotation for data security compliance.
Encryption Key Rotation Related Words
- Categories/Topics:
- Cybersecurity
- Cryptographic Key Management
- Data Encryption
Did you know?
A major financial institution once failed to rotate its encryption keys for over five years. When a breach occurred, attackers used outdated keys to access sensitive data. This security lapse resulted in significant financial losses and regulatory fines. Today, automated key rotation is an industry best practice.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment