IPsec (Internet Protocol Security)

Quick Navigation:
- IPsec Definition
- IPsec Explained Easy
- IPsec Origin
- IPsec Etymology
- IPsec Usage Trends
- IPsec Usage
- IPsec Examples in Context
- IPsec FAQ
- IPsec Related Words
IPsec Definition
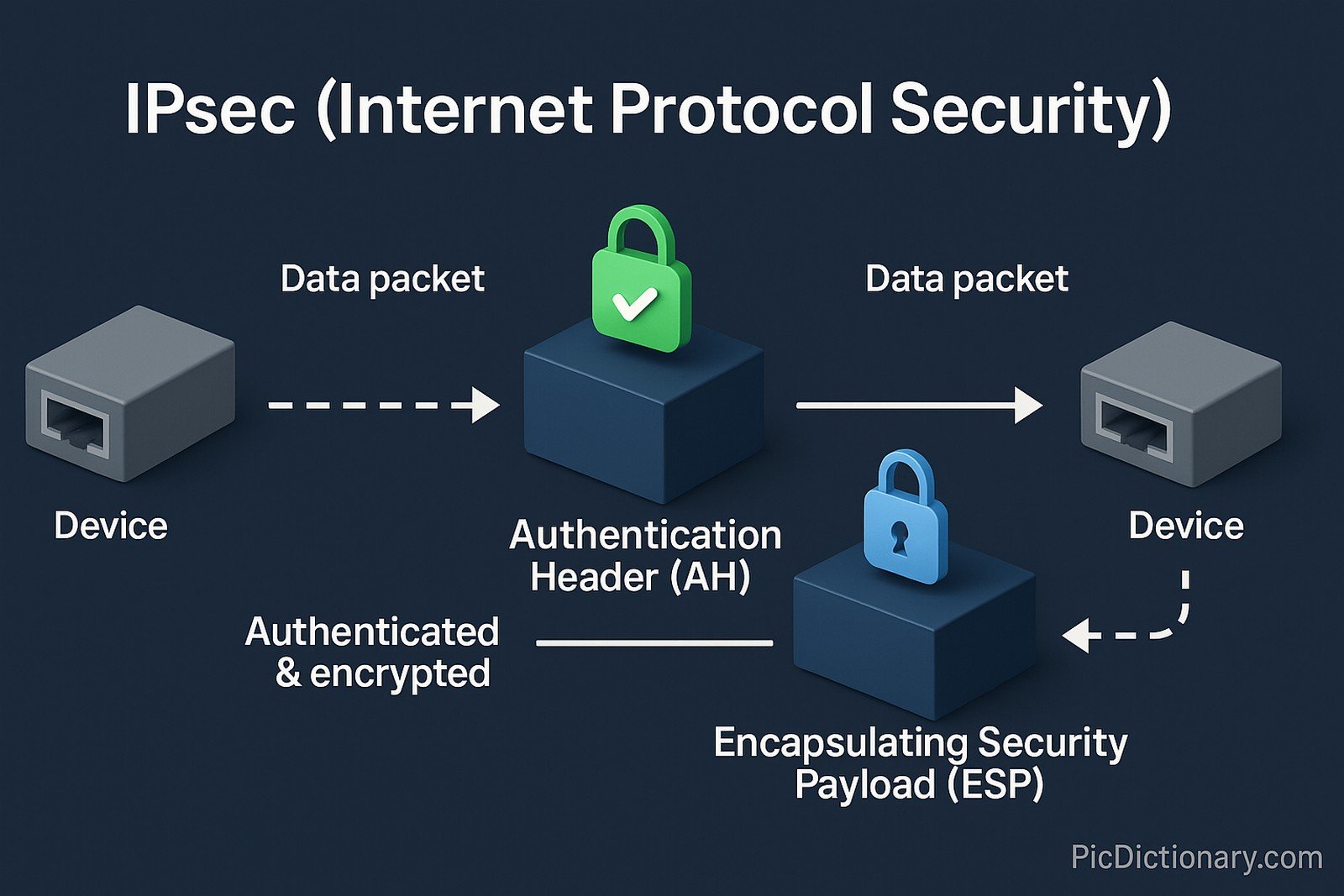
IPsec (Internet Protocol Security) is a comprehensive suite of protocols used to secure communications over Internet Protocol (IP) networks. It authenticates and encrypts each IP packet in a communication session. IPsec operates at the network layer, offering end-to-end security between devices or networks. It utilizes protocols like Authentication Header (AH) for data integrity and Encapsulating Security Payload (ESP) for encryption and authentication. IPsec is commonly used for virtual private networks (VPNs), ensuring confidentiality, integrity, and authentication of transmitted data.
IPsec Explained Easy
Imagine sending a letter to your friend. You put the letter in an envelope, lock it with a special key, and sign the outside so they know it’s really from you and hasn’t been changed. IPsec works like that for information traveling between computers: it locks (encrypts) the message and adds a signature (authenticates) to ensure the message is safe and from the right sender.
IPsec Origin
IPsec was developed in the mid-1990s by the Internet Engineering Task Force (IETF). It was introduced to address the growing need for security in IP communications, especially with the rise of the internet and corporate networking. The protocols were standardized in RFCs, laying the groundwork for secure data transfer over public networks.
IPsec Etymology
The name IPsec is derived from its focus on securing the Internet Protocol itself, providing protection and trust for IP communications.
IPsec Usage Trends
The usage of IPsec has significantly grown since the early 2000s. It remains a backbone for enterprise VPN solutions and secure site-to-site connections. With the surge in remote work and cloud adoption, IPsec continues to be relevant for securing corporate data transmission. However, modern alternatives like SSL VPNs and newer security models also share this space, influencing how IPsec is deployed today.
IPsec Usage
- Formal/Technical Tagging:
- Network Security
- Data Encryption
- VPN Technology - Typical Collocations:
- "IPsec tunnel"
- "IPsec protocol suite"
- "secure communication with IPsec"
- "IPsec VPN connection"
IPsec Examples in Context
- A company uses IPsec to secure remote employee access to internal servers over the internet.
- Banks deploy IPsec to protect sensitive transactions between branches.
- IPsec tunnels connect branch offices to a corporate data center securely.
IPsec FAQ
- What is IPsec?
IPsec is a set of protocols designed to secure data transmission over IP networks through encryption and authentication. - How does IPsec work?
It secures data by authenticating and encrypting IP packets between devices or networks. - What protocols are part of IPsec?
Authentication Header (AH) and Encapsulating Security Payload (ESP) are key protocols. - Where is IPsec commonly used?
It’s widely used in VPNs, secure site-to-site connections, and network security frameworks. - Is IPsec used in home networks?
Yes, particularly in routers that support VPN functionalities. - Does IPsec slow down connections?
It can add some overhead due to encryption, but modern devices handle this efficiently. - What are IPsec modes?
IPsec has two modes: transport mode (for end-to-end communication) and tunnel mode (commonly used in VPNs). - Is IPsec secure today?
Yes, when configured correctly with up-to-date algorithms, it remains highly secure. - What are IPsec alternatives?
Alternatives include SSL VPNs, WireGuard, and OpenVPN. - Can IPsec be used with IPv6?
Yes, IPsec is integrated into IPv6 specifications by default.
IPsec Related Words
- Categories/Topics:
- Network Security
- Data Encryption
- Virtual Private Networks (VPNs)
- Internet Protocol
Did you know?
The original IPsec protocols were so influential that they became mandatory components in IPv6 specifications, ensuring security was built directly into the next-generation internet protocol standard.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment