Security Information and Event Management (SIEM)

Quick Navigation:
- Security Information and Event Management (SIEM) Definition
- Security Information and Event Management (SIEM) Explained Easy
- Security Information and Event Management (SIEM) Origin
- Security Information and Event Management (SIEM) Etymology
- Security Information and Event Management (SIEM) Usage Trends
- Security Information and Event Management (SIEM) Usage
- Security Information and Event Management (SIEM) Examples in Context
- Security Information and Event Management (SIEM) FAQ
- Security Information and Event Management (SIEM) Related Words
Security Information and Event Management (SIEM) Definition
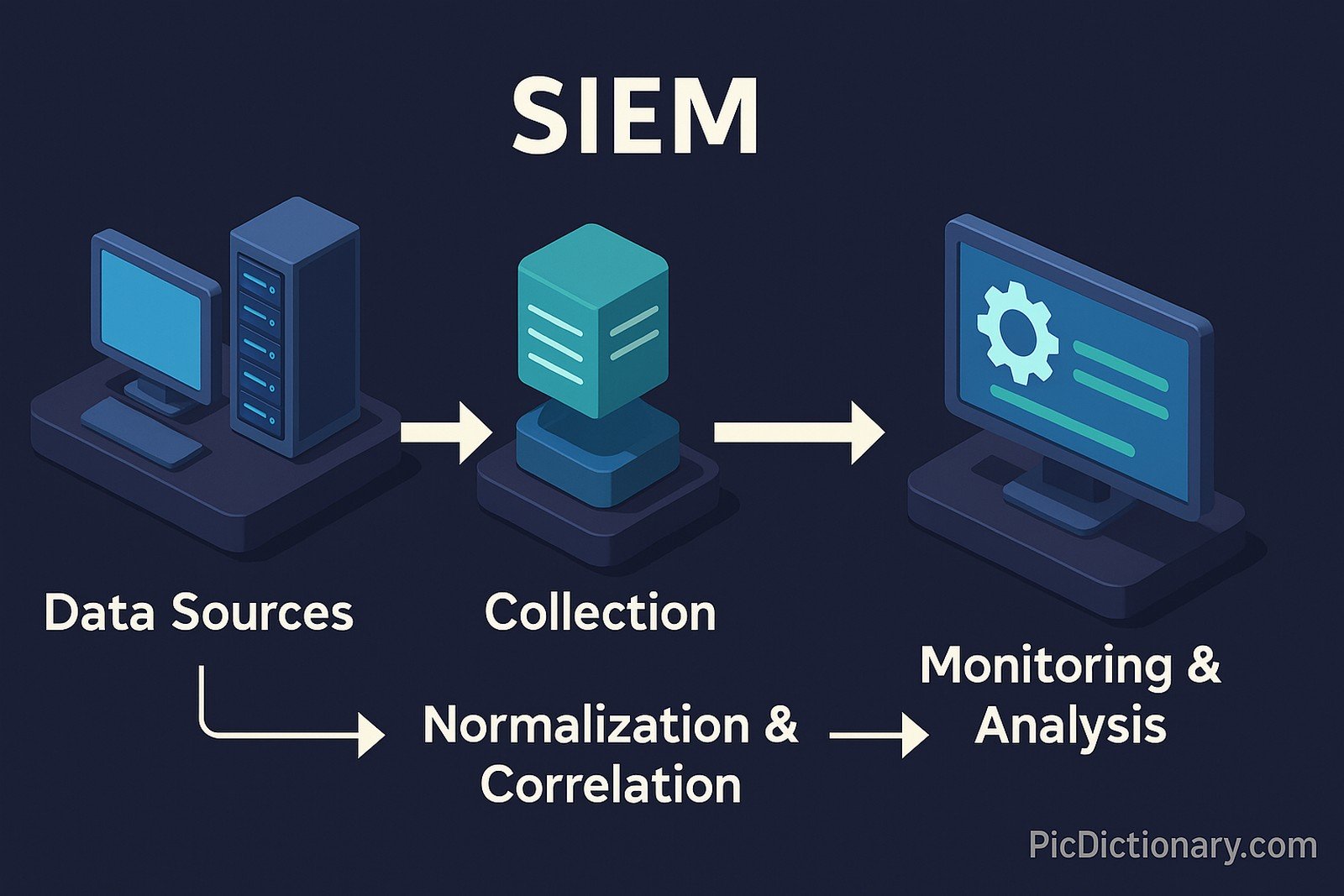
Security Information and Event Management (SIEM) is a cybersecurity solution that aggregates and analyzes security data from various sources across an IT environment. It collects logs and event data, normalizes and correlates this information, and provides real-time monitoring, threat detection, and incident response. SIEM systems help security teams identify unusual activity and potential breaches quickly, supporting compliance reporting and forensic analysis.
Security Information and Event Management (SIEM) Explained Easy
Imagine you have a big house with many doors and windows, and you install alarms on each one. Instead of checking every alarm separately, you have one screen that shows alerts from every door and window in real time. SIEM is like that screen for a company’s computer systems — it shows all security alerts in one place, helping experts act quickly when something suspicious happens.
Security Information and Event Management (SIEM) Origin
The concept of SIEM was introduced in the early 2000s when organizations began combining Security Information Management (SIM) and Security Event Management (SEM) to create a more comprehensive security monitoring solution. Vendors like ArcSight, IBM, and Splunk pioneered the development of SIEM platforms.
Security Information and Event Management (SIEM) Etymology
The term SIEM was coined by combining the concepts of security information and event management to represent a unified approach to security monitoring and incident response.
Security Information and Event Management (SIEM) Usage Trends
Over the past decade, SIEM usage has grown substantially with the rise of cyber threats and data privacy regulations like GDPR and HIPAA. Modern SIEM systems now incorporate AI and machine learning to enhance threat detection and are moving towards cloud-based solutions to accommodate hybrid IT environments.
Security Information and Event Management (SIEM) Usage
- Formal/Technical Tagging:
- Cybersecurity
- Threat Intelligence
- IT Compliance - Typical Collocations:
- "SIEM platform"
- "real-time monitoring"
- "threat detection with SIEM"
- "SIEM log management"
Security Information and Event Management (SIEM) Examples in Context
- Financial institutions use SIEM systems to detect suspicious transactions and insider threats.
- Healthcare providers deploy SIEM to comply with HIPAA regulations and secure patient data.
- Large enterprises rely on SIEM for real-time alerts on unauthorized access attempts.
Security Information and Event Management (SIEM) FAQ
- What is SIEM?
SIEM is a cybersecurity solution that monitors and analyzes security events across IT environments. - How does SIEM work?
It collects, normalizes, and correlates data from multiple sources to detect anomalies and alert security teams. - What are the key features of SIEM?
Key features include log management, real-time alerting, incident response, and compliance reporting. - Who uses SIEM?
Organizations of all sizes, especially in finance, healthcare, and government sectors, use SIEM solutions. - Why is SIEM important?
SIEM helps in early threat detection, minimizing the impact of cyberattacks, and fulfilling compliance requirements. - Can SIEM prevent cyberattacks?
SIEM does not prevent attacks directly but detects and alerts on potential threats to mitigate damage. - Is SIEM only for large companies?
No, cloud-based and managed SIEM solutions are now accessible for small and mid-sized businesses. - What are common SIEM tools?
Common tools include Splunk, IBM QRadar, ArcSight, and Microsoft Sentinel. - How is SIEM evolving?
Modern SIEM integrates AI, machine learning, and cloud-based services for faster and smarter detection. - Does SIEM require constant monitoring?
Yes, effective use of SIEM involves continuous monitoring and analysis by security experts.
Security Information and Event Management (SIEM) Related Words
- Categories/Topics:
- Cybersecurity
- Network Security
- IT Governance
Did you know?
The first documented use of SIEM tools in a government agency was by the US Department of Defense, which leveraged early SIEM platforms to detect state-sponsored cyberattacks and insider threats, setting a precedent for national security cybersecurity monitoring.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment