Browser Isolation

Quick Navigation:
- Browser Isolation Definition
- Browser Isolation Explained Easy
- Browser Isolation Origin
- Browser Isolation Etymology
- Browser Isolation Usage Trends
- Browser Isolation Usage
- Browser Isolation Examples in Context
- Browser Isolation FAQ
- Browser Isolation Related Words
Browser Isolation Definition
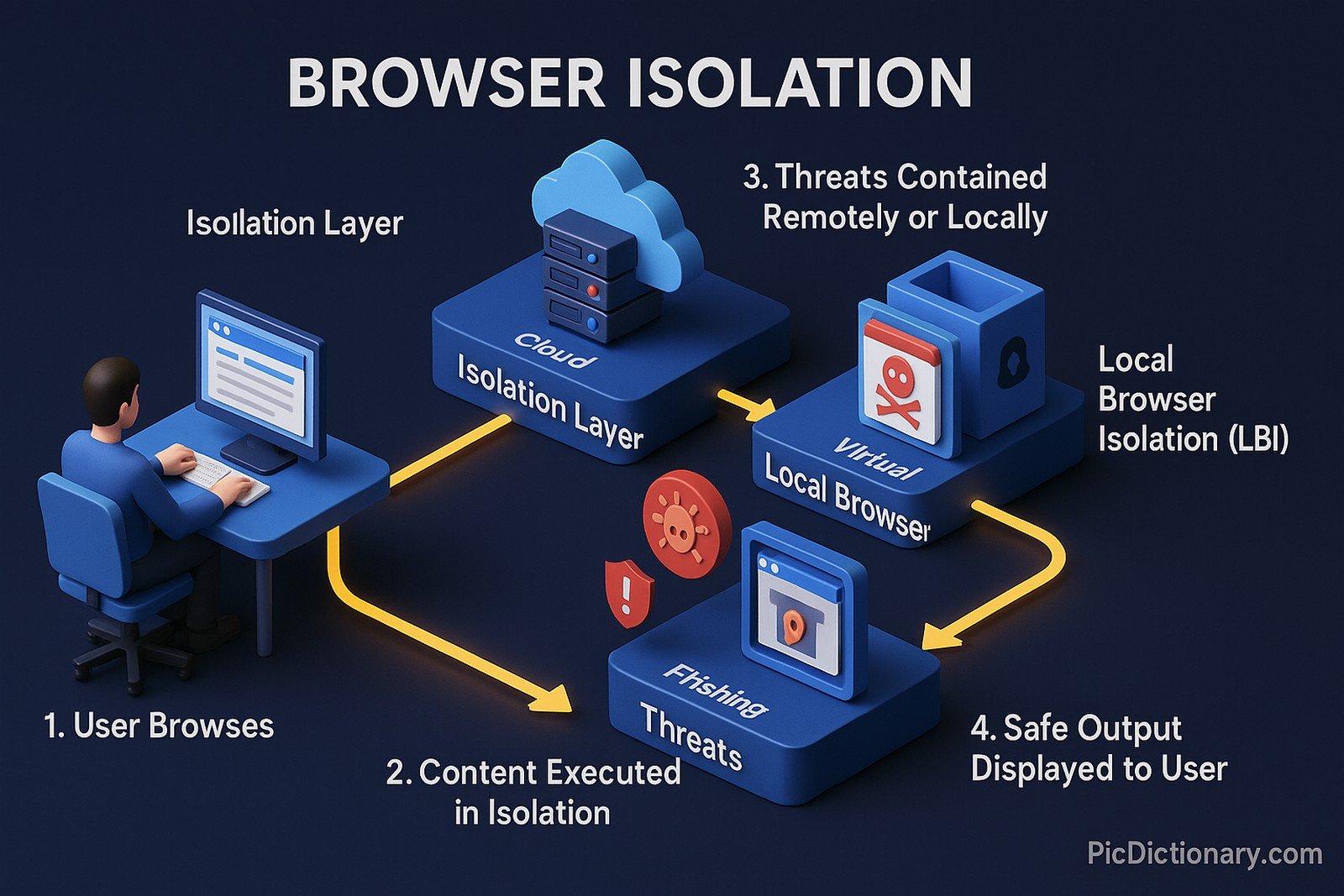
Browser Isolation is a cybersecurity technique that separates web browsing activity from the user’s local network and endpoints. It achieves this by executing web content in a remote or virtualized environment, ensuring that malicious code, malware, or phishing attacks cannot reach the user's device. The two primary types of browser isolation are remote browser isolation (RBI), which runs the browsing session in a cloud-based server, and local browser isolation (LBI), which uses virtualization to contain threats on the device itself. Browser isolation is widely adopted in enterprises to protect sensitive data and mitigate cyber threats.
Browser Isolation Explained Easy
Imagine you’re wearing a thick safety suit while exploring a jungle full of dangerous animals. Even if something jumps at you, it won’t hurt you because you’re protected. Browser isolation works the same way—it opens web pages in a secure place away from your computer, so viruses and bad websites can’t cause any harm.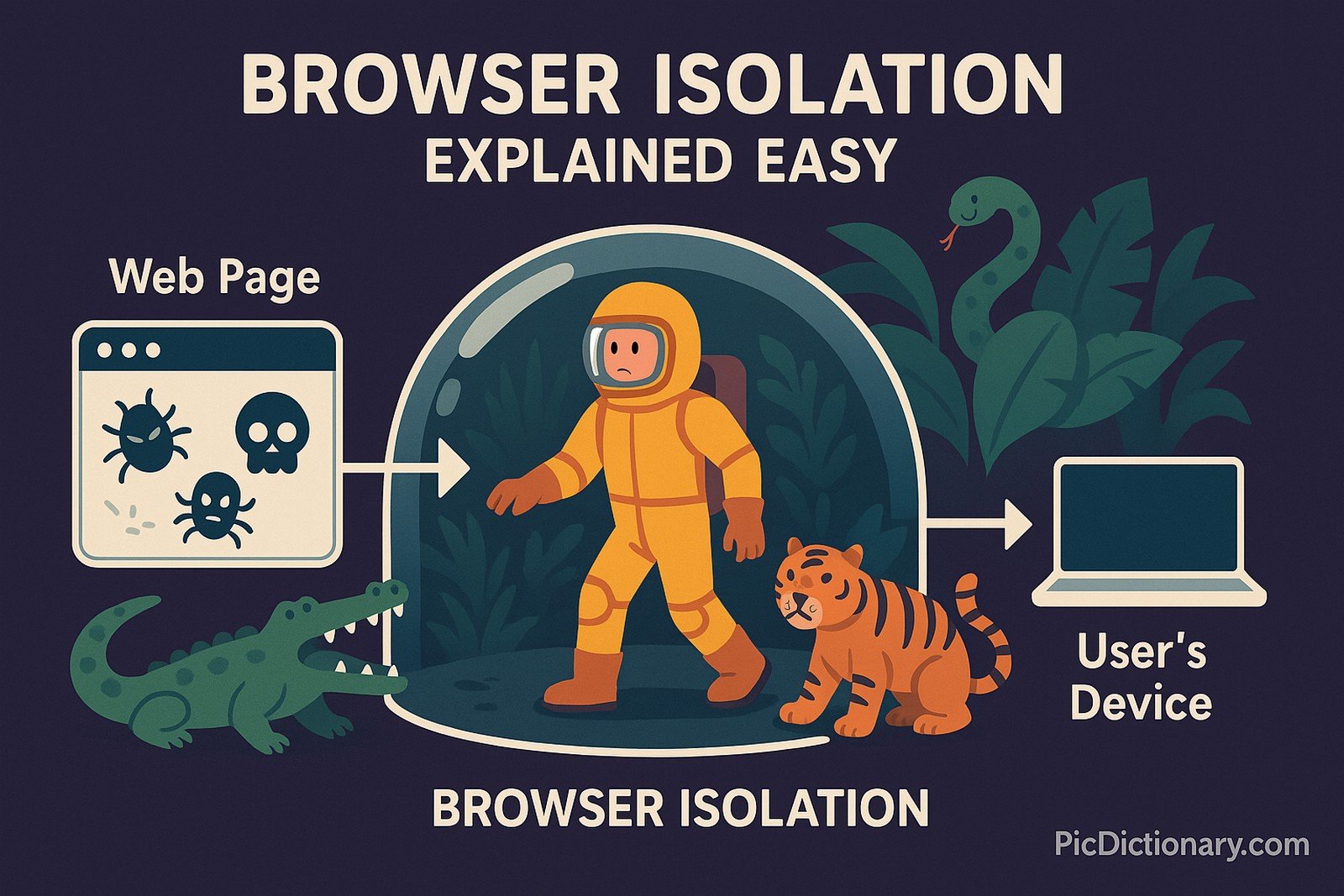
Browser Isolation Origin
The concept of isolating browsing activity dates back to early virtualization and sandboxing techniques in cybersecurity. With the rise of web-based threats in the late 2000s, security experts sought ways to prevent browser-based malware from infecting corporate networks. By 2015, browser isolation became a mainstream solution, particularly in industries handling sensitive data.
Browser Isolation Etymology
The term "browser isolation" is derived from the words “browser,” meaning the software used to access the web, and “isolation,” referring to the act of separating something to ensure security.
Browser Isolation Usage Trends
In recent years, browser isolation has gained traction due to the increasing sophistication of cyber threats such as phishing, ransomware, and zero-day exploits. Organizations in finance, healthcare, and government have prioritized its adoption to protect confidential data and ensure compliance with cybersecurity regulations. As remote work continues to rise, businesses are integrating browser isolation with Zero Trust frameworks to enhance endpoint security.
Browser Isolation Usage
- Formal/Technical Tagging:
- Cybersecurity
- Network Security
- Endpoint Protection - Typical Collocations:
- "remote browser isolation solution"
- "secure web browsing with isolation"
- "browser isolation technology"
- "enterprise-grade browser isolation"
Browser Isolation Examples in Context
- A financial institution implements browser isolation to prevent phishing attacks from compromising employees' credentials.
- An employee working remotely accesses a company’s web applications through an isolated browser session to prevent data leakage.
- A security-conscious organization enforces browser isolation to ensure that web downloads do not directly interact with internal systems.
Browser Isolation FAQ
- What is browser isolation?
Browser isolation is a security approach that prevents web threats by running browser sessions in a remote or virtualized environment. - How does browser isolation protect against cyber threats?
It ensures that malicious scripts, phishing sites, and drive-by downloads are contained within a secure, isolated session away from the local device. - What are the types of browser isolation?
The main types are remote browser isolation (RBI), which runs sessions on a cloud server, and local browser isolation (LBI), which uses virtualization on the user's device. - Who uses browser isolation?
It is widely used by enterprises, financial institutions, healthcare organizations, and government agencies to safeguard sensitive data. - Does browser isolation affect browsing speed?
It can introduce slight latency, but modern solutions optimize performance to provide a seamless browsing experience. - Can browser isolation prevent phishing attacks?
Yes, it prevents users from interacting with malicious sites by rendering web pages in a safe, non-interactive mode. - Is browser isolation necessary for personal use?
While enterprises benefit the most, individuals concerned about security can also use browser isolation solutions to enhance protection. - How does browser isolation integrate with Zero Trust security?
It aligns with Zero Trust principles by ensuring that all web activity is verified and contained before reaching the internal network. - What are the limitations of browser isolation?
It may require additional infrastructure, and some interactive web applications might not function as smoothly as in a traditional browser. - Is browser isolation better than antivirus software?
It complements antivirus protection by preventing threats before they reach the endpoint, offering an extra layer of security.
Browser Isolation Related Words
- Categories/Topics:
- Cybersecurity
- Cloud Security
- Secure Web Browsing
Did you know?
In 2017, Google introduced a concept similar to browser isolation called “Site Isolation” in Chrome, which prevents malicious websites from accessing data from other tabs. This feature became a crucial security measure, particularly against Spectre and Meltdown vulnerabilities affecting modern processors.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment