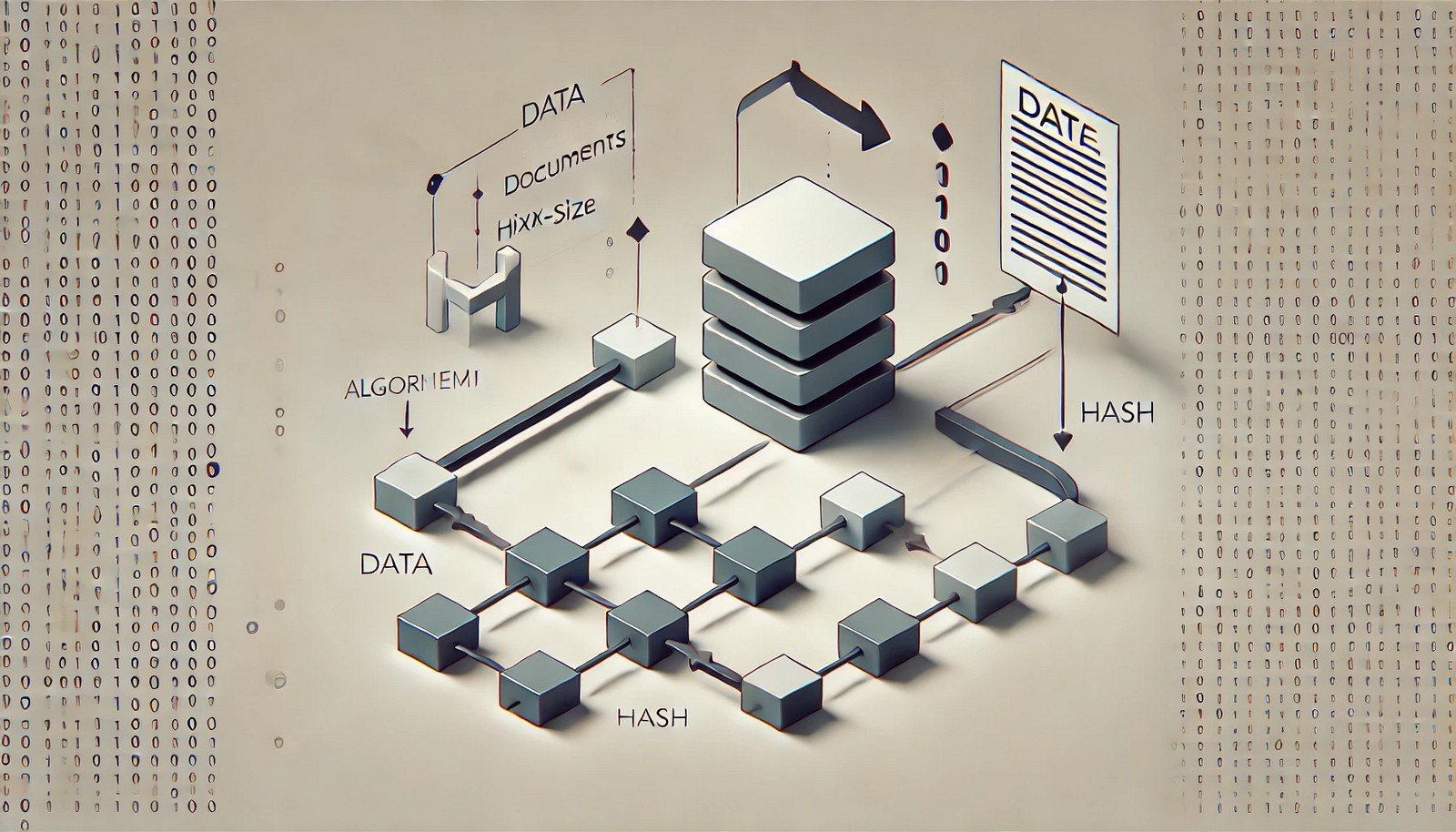
Hashing Algorithm
Quick Navigation:
- Hashing Algorithm Definition
- Hashing Algorithm Explained Easy
- Hashing Algorithm Origin
- Hashing Algorithm Etymology
- Hashing Algorithm Usage Trends
- Hashing Algorithm Usage
- Hashing Algorithm Examples in Context
- Hashing Algorithm FAQ
- Hashing Algorithm Related Words
Hashing Algorithm Definition
A hashing algorithm is a mathematical function that converts an input of arbitrary size into a fixed-size string of characters, typically a hash value or digest. It is a one-way function, meaning it is computationally infeasible to reverse-engineer the original input from the hash. Hashing algorithms are crucial in cryptographic applications, data integrity verification, and efficient data retrieval. Examples include SHA-256, MD5, and bcrypt.
Hashing Algorithm Explained Easy
Imagine you have a big jar of candy, and you give each type of candy a unique code. No matter how much candy you have, you can always quickly find or verify one by just looking at its code. A hashing algorithm does the same thing for data—it gives each piece of information a unique "code."
Hashing Algorithm Origin
The concept of hashing originated in the mid-20th century as a method for efficient data storage and retrieval in computing systems. Its use expanded with the advent of cryptography in the 1970s, becoming a cornerstone in securing digital communication.
Hashing Algorithm Etymology
The term "hashing" derives from the notion of "hashing out" data, akin to chopping or scrambling, reflecting the transformation of input data into a scrambled output.
Hashing Algorithm Usage Trends
Hashing algorithms have seen widespread adoption in cybersecurity, blockchain technology, and database indexing. Over the years, their sophistication has grown to counteract vulnerabilities such as collisions and pre-image attacks, ensuring data integrity and secure transactions.
Hashing Algorithm Usage
- Formal/Technical Tagging:
- Cryptography
- Data Integrity
- Blockchain Technology - Typical Collocations:
- "secure hashing algorithm"
- "hash function in blockchain"
- "password hashing techniques"
- "cryptographic hash validation"
Hashing Algorithm Examples in Context
- SHA-256 is used in blockchain networks to secure and verify transactions.
- MD5 hashes can verify the integrity of downloaded files by comparing hash values.
- Bcrypt adds salt to hashed passwords, making them more secure against brute-force attacks.
Hashing Algorithm FAQ
- What is a hashing algorithm?
A hashing algorithm converts input data into a fixed-size hash value, ensuring secure and efficient data handling. - What are hashing algorithms used for?
They are used for securing passwords, ensuring data integrity, and verifying transactions in blockchain. - How does a hashing algorithm differ from encryption?
Hashing is one-way and irreversible, while encryption is reversible with a key. - Why is SHA-256 widely used?
SHA-256 offers strong security and resistance to collisions, making it ideal for blockchain and cryptography. - What is a hash collision?
A collision occurs when two different inputs produce the same hash value. - How are passwords secured with hashing?
Passwords are hashed and often salted to prevent easy decoding by attackers. - Can a hash be decrypted?
No, hashes are designed to be irreversible. - What is salting in hashing?
Salting adds random data to a password before hashing to increase security. - Why are hashing algorithms important in blockchain?
They ensure the integrity of blocks and prevent tampering. - Are MD5 and SHA-1 still secure?
They are considered outdated due to vulnerability to collisions.
Hashing Algorithm Related Words
- Categories/Topics:
- Cryptography
- Data Security
- Blockchain
Did you know?
The Bitcoin blockchain uses SHA-256 hashing, which underpins the security and immutability of its transactions. Despite being computationally intense, this hashing algorithm ensures that every block added to the chain remains tamper-proof.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment