Remote Access Management

Quick Navigation:
- Remote Access Management Definition
- Remote Access Management Explained Easy
- Remote Access Management Origin
- Remote Access Management Etymology
- Remote Access Management Usage Trends
- Remote Access Management Usage
- Remote Access Management Examples in Context
- Remote Access Management FAQ
- Remote Access Management Related Words
Remote Access Management Definition
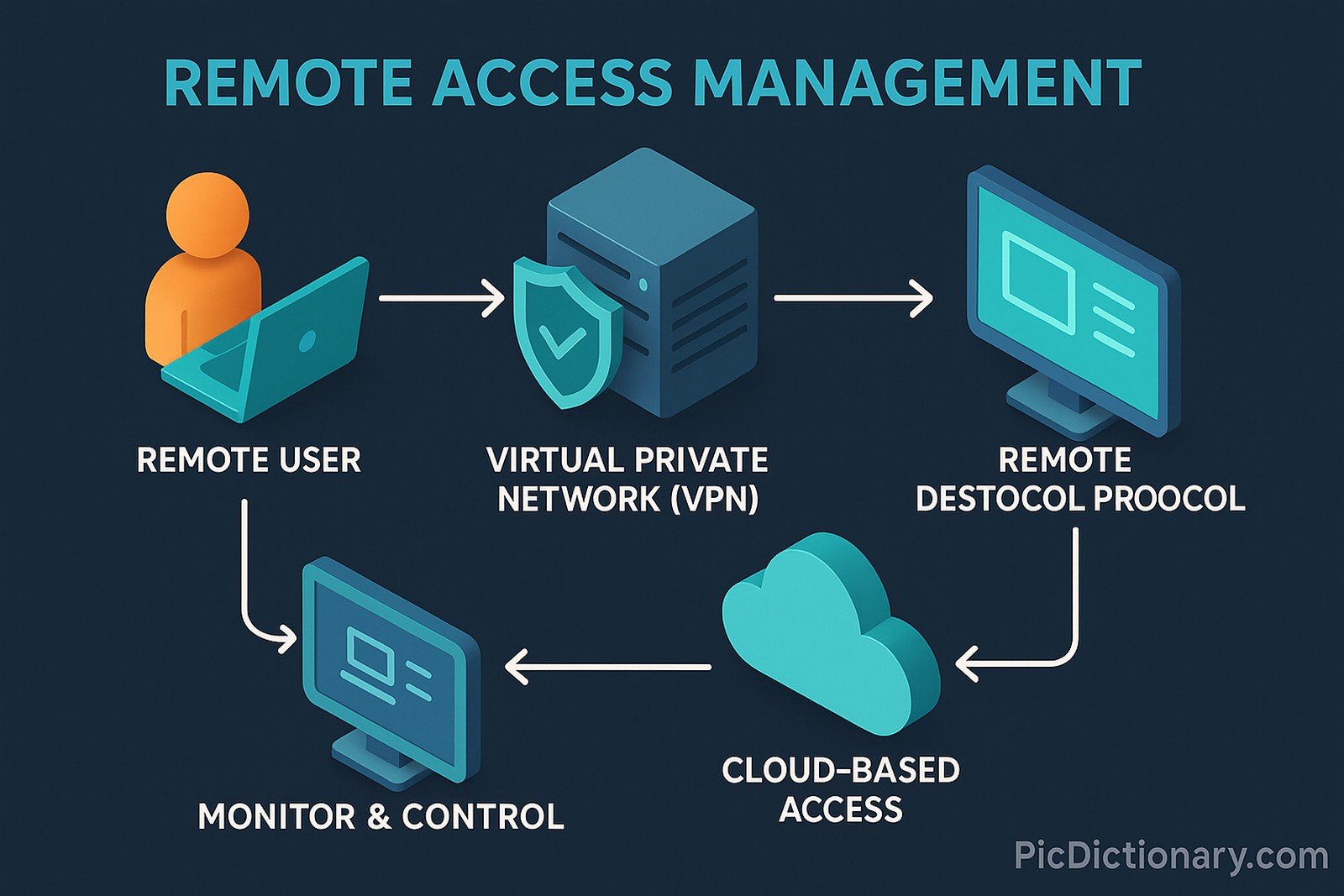
Remote Access Management (RAM) refers to the process of securely controlling and monitoring access to a computer system, network, or data from remote locations. It enables administrators to grant, restrict, and oversee remote user connections while ensuring security protocols are enforced. Common methods include Virtual Private Networks (VPNs), Remote Desktop Protocol (RDP), and cloud-based access controls. Effective RAM minimizes unauthorized access risks and improves operational efficiency for businesses and IT teams.
Remote Access Management Explained Easy
Think of RAM like a magical key that lets you enter your house from anywhere in the world, but only if you're allowed to. It’s like having a special passcode for your computer so you can use it even when you're not home. This ensures that only trusted people can open the door, keeping intruders out!
Remote Access Management Origin
Remote Access Management evolved alongside networking and internet advancements. Initially, remote access was limited to dial-up connections, but with broadband, VPNs, and cloud services, remote management has become an essential part of IT infrastructure. The demand for secure remote access surged with the rise of remote work and cloud computing.
Remote Access Management Etymology
The term “remote access” stems from "remote," meaning distant, and "access," meaning the ability to enter or use something. "Management" refers to the act of controlling or overseeing a process. Together, the term signifies the controlled ability to connect and use resources from afar.
Remote Access Management Usage Trends
The adoption of RAM has increased dramatically, particularly since the COVID-19 pandemic forced a shift to remote work. Businesses now prioritize secure access solutions to protect sensitive data and ensure seamless operations. Cloud-based remote management tools have gained traction, replacing traditional on-premises systems. Industries like healthcare, finance, and IT heavily rely on RAM for security and efficiency.
Remote Access Management Usage
- Formal/Technical Tagging:
- IT Security
- Network Administration
- Cloud Computing - Typical Collocations:
- "Remote access security protocols"
- "Cloud-based remote management"
- "VPN remote access solutions"
- "Secured remote connection"
Remote Access Management Examples in Context
- A company’s IT administrator uses RAM to grant employees secure access to work systems from home.
- A remote healthcare provider uses secure remote access to review patient records.
- A technician troubleshoots a client’s computer remotely via a secured connection.
Remote Access Management FAQ
- What is Remote Access Management?
Remote Access Management is a system that enables secure access and control of computers or networks from remote locations. - How does Remote Access Management work?
It typically uses encrypted connections like VPNs, RDP, or cloud-based authentication to allow remote users to access systems securely. - Why is Remote Access Management important?
It enhances security, enables remote work, and ensures only authorized users can access sensitive systems. - What are common Remote Access Management tools?
Popular tools include VPNs, Microsoft Remote Desktop, AnyDesk, and TeamViewer. - Is Remote Access Management secure?
Yes, when configured with strong authentication, encryption, and monitoring, it provides a secure remote connection. - How does a VPN enhance Remote Access Management?
A VPN encrypts remote connections, ensuring data is transmitted securely over the internet. - What risks are associated with Remote Access Management?
Potential risks include unauthorized access, data breaches, and malware if security measures are weak. - Can Remote Access Management be used on mobile devices?
Yes, mobile devices can use VPNs and remote desktop apps to securely access systems. - What industries rely on Remote Access Management?
IT, healthcare, finance, and manufacturing industries widely use RAM for secure connectivity. - How can businesses improve Remote Access Management security?
By implementing multi-factor authentication, using encrypted connections, and regularly updating access policies.
Remote Access Management Related Words
- Categories/Topics:
- Cybersecurity
- Network Access Control
- Cloud Security
Did you know?
In 2020, a surge in remote work led to a 300% increase in cyberattacks targeting remote access systems. Companies had to rapidly enhance security measures to prevent breaches, making RAM a top IT priority.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment