Secure Data Destruction
 (Representational Image | Source: Dall-E)
(Representational Image | Source: Dall-E)
Quick Navigation:
- Secure Data Destruction Definition
- Secure Data Destruction Explained Easy
- Secure Data Destruction Origin
- Secure Data Destruction Etymology
- Secure Data Destruction Usage Trends
- Secure Data Destruction Usage
- Secure Data Destruction Examples in Context
- Secure Data Destruction FAQ
- Secure Data Destruction Related Words
Secure Data Destruction Definition
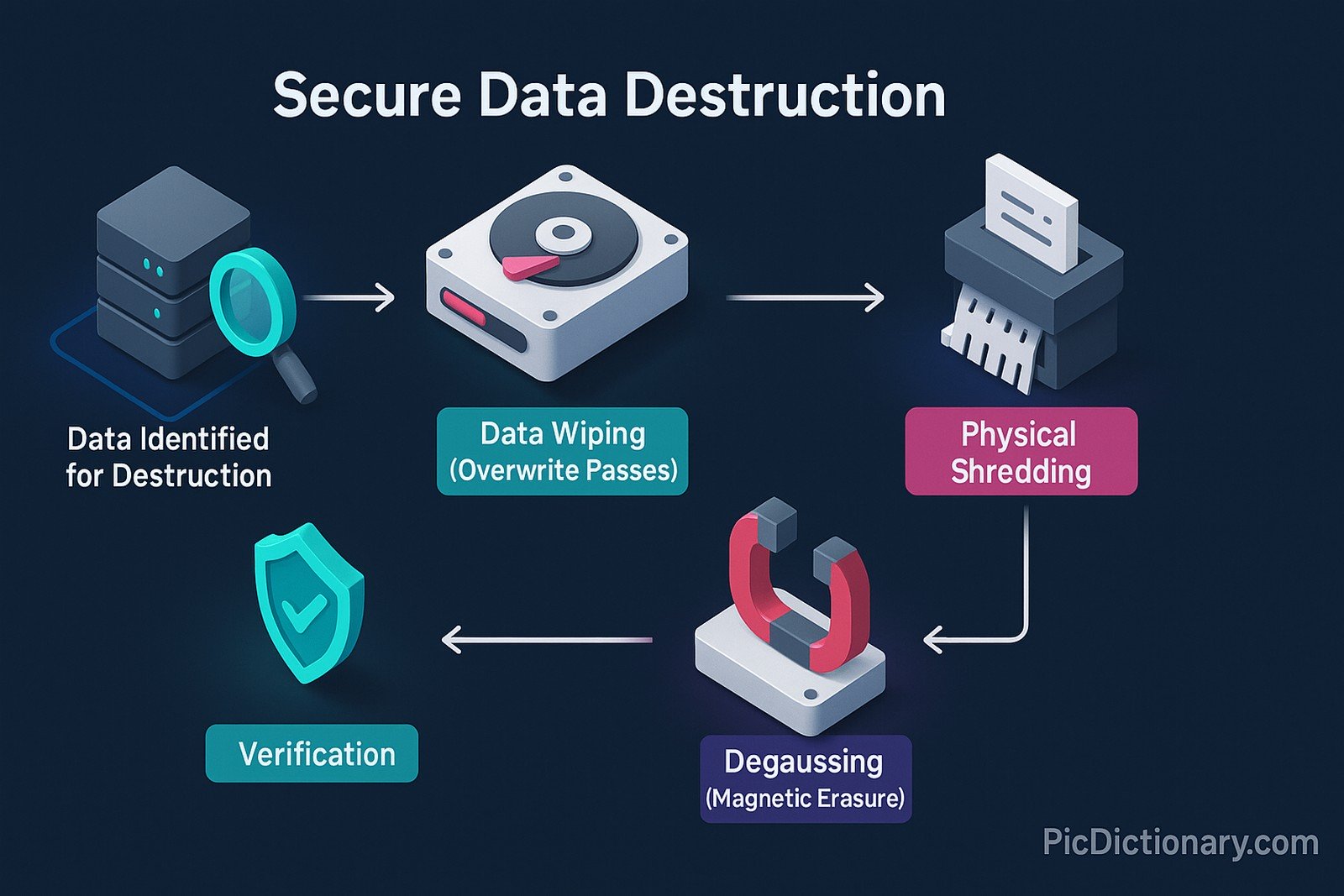
Secure data destruction refers to the process of permanently and irreversibly erasing digital data from storage devices to prevent unauthorized access or recovery. This process ensures that sensitive or confidential information cannot be retrieved, even using advanced forensic techniques. Secure data destruction methods include data wiping, degaussing, and physical destruction, each catering to different security needs and compliance requirements.
Secure Data Destruction Explained Easy
Imagine you wrote a secret note and wanted to make sure no one could ever read it. You could either tear it into tiny pieces, burn it, or shred it into dust. Secure data destruction is like that but for computers. It makes sure that when you delete something important, no one can ever bring it back, no matter what they try.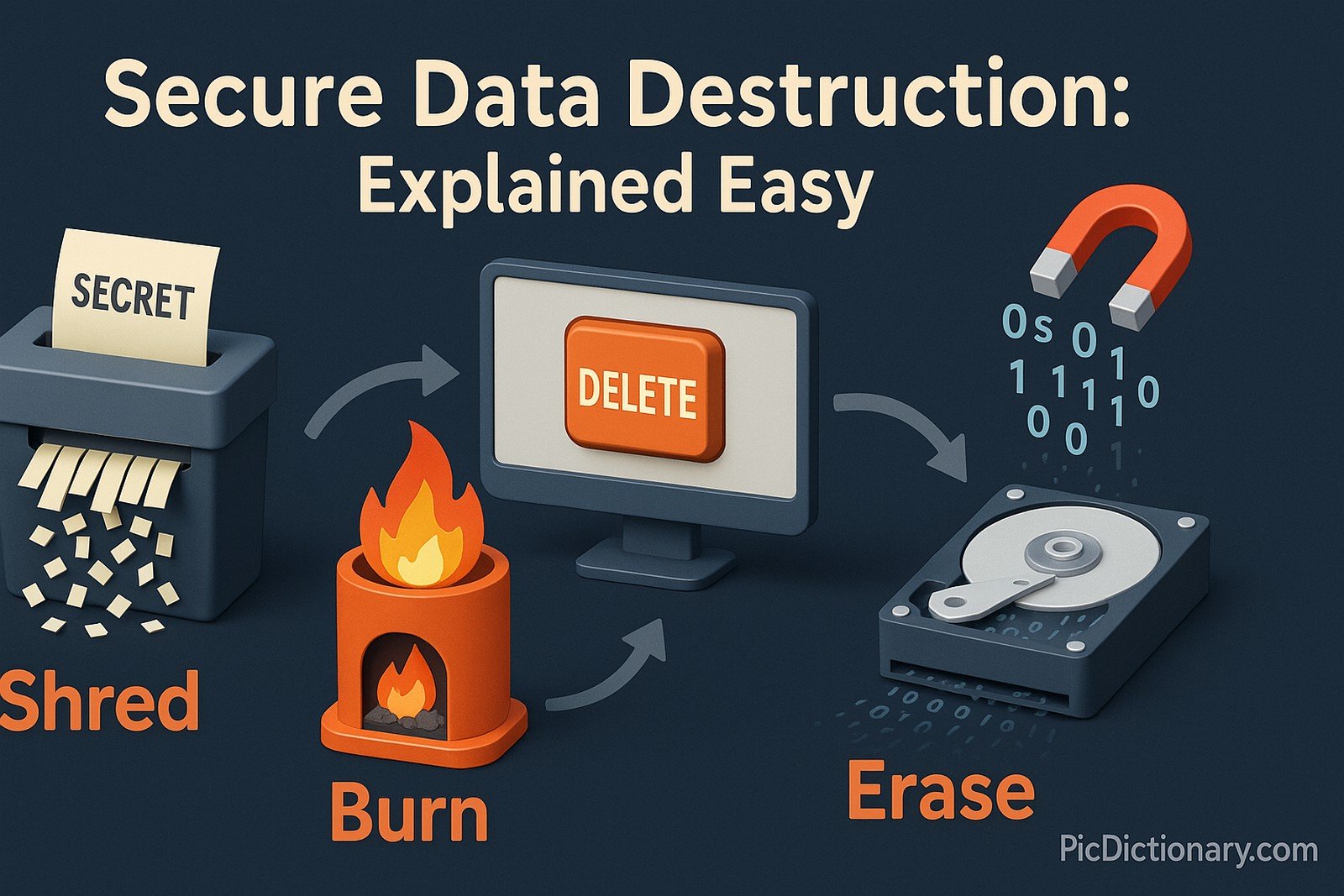
Secure Data Destruction Origin
The concept of secure data destruction emerged with the growth of digital storage media. In the early days of computing, simple file deletion was considered sufficient. However, as cyber threats increased and data recovery techniques advanced, organizations required more robust methods to ensure sensitive data was completely destroyed.
Secure Data Destruction Etymology
The term "secure data destruction" combines three components:
Secure: From the Latin securus, meaning "free from care" or "safe."
Data: From the Latin datum, meaning "something given" or "information."
Destruction: From the Latin destruere, meaning "to tear down" or "demolish."
Secure Data Destruction Usage Trends
With growing cybersecurity concerns, industries such as finance, healthcare, and government agencies have increased their focus on secure data destruction. The rise of global data protection regulations like GDPR, HIPAA, and PCI-DSS has driven demand for certified destruction methods. Companies are now investing in more secure, environmentally friendly data disposal solutions.
Secure Data Destruction Usage
- Formal/Technical Tagging:
- Cybersecurity
- Data Privacy
- Compliance Regulations - Typical Collocations:
- "secure data destruction service"
- "permanent data erasure"
- "hard drive shredding"
- "certified data destruction"
Secure Data Destruction Examples in Context
- A financial institution hires a certified data destruction service to shred old hard drives containing customer records.
- A hospital securely wipes patient records from outdated servers before decommissioning them.
- An organization follows GDPR-compliant data destruction practices when retiring old laptops.
Secure Data Destruction FAQ
- What is secure data destruction?
Secure data destruction is the process of permanently erasing or destroying digital information to prevent unauthorized recovery. - How is secure data destruction different from regular file deletion?
Regular file deletion only removes a file’s reference, allowing it to be recovered. Secure data destruction makes data irretrievable. - What are the most common methods of secure data destruction?
Common methods include data wiping (software-based), degaussing (magnetic erasure), and physical destruction (shredding or incineration). - Why is secure data destruction important?
It protects sensitive information from unauthorized access, ensuring compliance with data privacy laws and preventing data breaches. - Can deleted files be recovered?
Yes, unless they have been securely destroyed using methods that overwrite or physically damage the storage medium. - Is secure data destruction required by law?
Many regulations, such as GDPR and HIPAA, mandate secure data destruction for organizations handling sensitive data. - How do businesses securely destroy electronic waste?
They use certified e-waste recyclers that perform data wiping, degaussing, or physical destruction before recycling hardware. - What is the safest way to destroy a hard drive?
Shredding the hard drive into tiny pieces or using a certified degaussing machine ensures complete destruction. - Are software-based data erasure methods effective?
Yes, if they follow industry standards like DoD 5220.22-M or NIST 800-88 guidelines for secure data wiping. - How often should businesses perform secure data destruction?
Businesses should implement regular data destruction policies, especially when decommissioning old devices or handling sensitive information.
Secure Data Destruction Related Words
- Categories/Topics:
- Cybersecurity
- Data Privacy
- Compliance & Regulations
Did you know?
In 2013, Edward Snowden revealed that the NSA had special protocols for secure data destruction, including pulverizing hard drives into dust-sized particles to ensure no recovery was possible. Some high-security organizations even use acid baths to dissolve storage devices completely.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment