Secure Enclave
 (Representational Image | Source: Dall-E)
(Representational Image | Source: Dall-E)
Quick Navigation:
- Secure Enclave Definition
- Secure Enclave Explained Easy
- Secure Enclave Origin
- Secure Enclave Etymology
- Secure Enclave Usage Trends
- Secure Enclave Usage
- Secure Enclave Examples in Context
- Secure Enclave FAQ
- Secure Enclave Related Words
Secure Enclave Definition
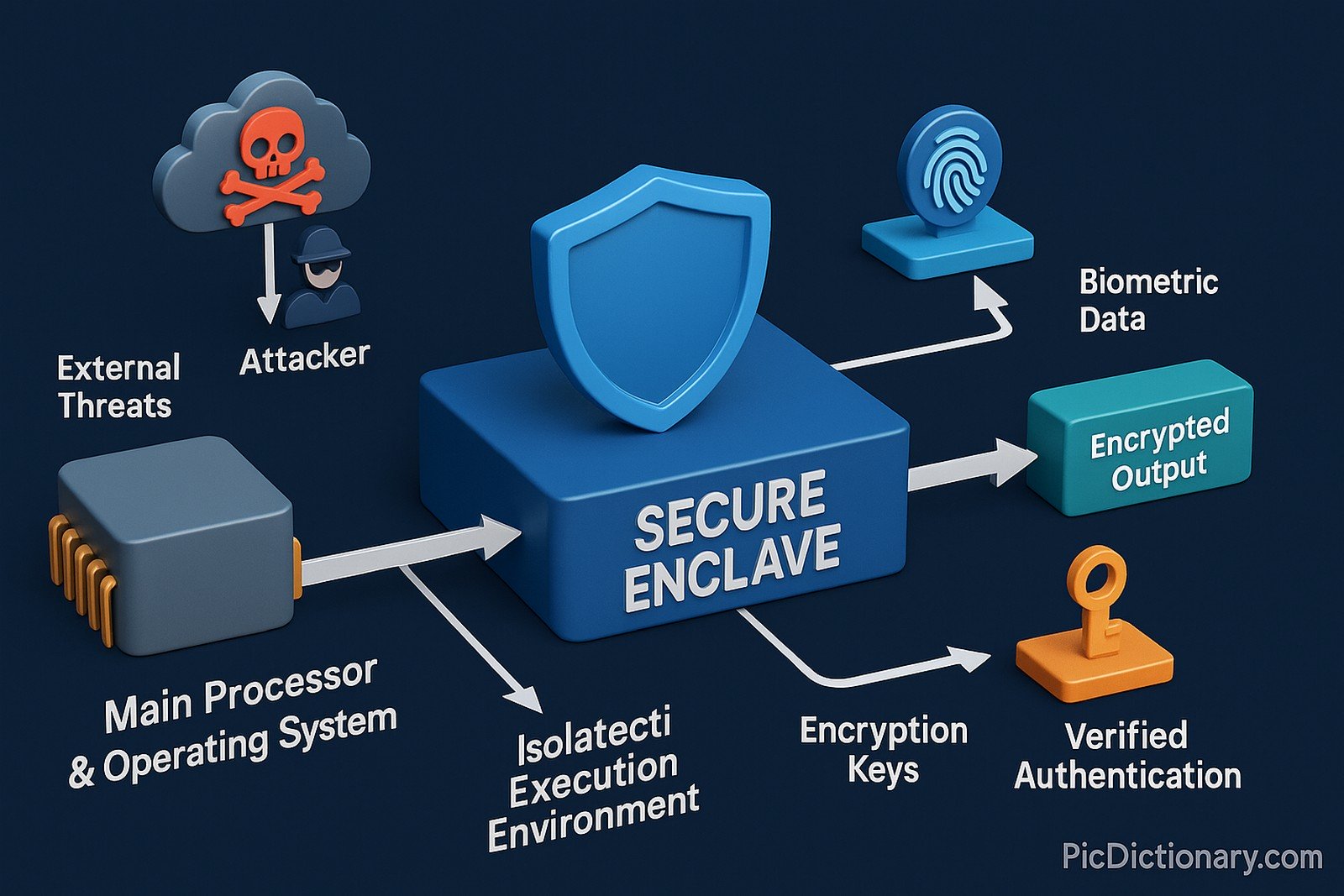
A Secure Enclave is a dedicated, isolated hardware component designed to protect sensitive data and cryptographic operations. It operates independently from the main processor and OS, ensuring a secure execution environment resistant to attacks, even if the primary system is compromised. Secure Enclaves are widely used in modern computing for protecting biometric authentication, encryption keys, and confidential computing tasks.
Secure Enclave Explained Easy
Imagine you have a secret diary, and you keep it in a locked, fireproof safe inside your room. Even if someone breaks into your room, they can’t access the diary without the key. A Secure Enclave is like that safe—it keeps important information locked away and protected, even if the rest of your computer gets hacked.
Secure Enclave Origin
The concept of hardware-based secure execution environments dates back to early security modules used in banking and military applications. Modern Secure Enclaves gained prominence with Apple's introduction of the Secure Enclave Processor (SEP) in 2013 for Touch ID security.
Secure Enclave Etymology
The term "Secure Enclave" combines "secure," meaning protected from harm, with "enclave," a term referring to a safeguarded or isolated space.
Secure Enclave Usage Trends
Secure Enclaves have become a crucial part of cybersecurity, especially with the rise of biometric authentication, confidential computing, and digital wallets. Apple, Intel, and AMD have integrated Secure Enclaves into their hardware for enhanced privacy and protection against data breaches.
Secure Enclave Usage
- Formal/Technical Tagging:
- Cryptographic Security
- Hardware Security
- Trusted Execution Environment - Typical Collocations:
- "secure enclave technology"
- "hardware-based encryption"
- "protected execution environment"
- "secure enclave in mobile devices"
Secure Enclave Examples in Context
- A Secure Enclave ensures that Face ID data on iPhones remains encrypted and inaccessible to apps or the OS.
- Modern banking apps use Secure Enclaves to protect biometric authentication data.
- Intel’s SGX (Software Guard Extensions) technology employs Secure Enclaves to safeguard sensitive computations in cloud environments.
Secure Enclave FAQ
- What is a Secure Enclave?
A Secure Enclave is a hardware-based security feature that isolates sensitive data from the main system. - How does a Secure Enclave work?
It creates a separate, encrypted execution environment that only authorized software can access. - Where are Secure Enclaves used?
They are used in smartphones, cloud computing, and enterprise security systems. - What makes a Secure Enclave secure?
It operates independently from the OS, uses encryption, and restricts unauthorized access. - Does every device have a Secure Enclave?
No, only devices with specialized hardware, like Apple and Intel chips, support Secure Enclaves. - How does Apple’s Secure Enclave differ from Intel’s?
Apple’s Secure Enclave is designed for biometric authentication, while Intel SGX focuses on secure cloud computing. - Can Secure Enclaves be hacked?
While highly secure, vulnerabilities have been discovered and patched over time. - Do Secure Enclaves slow down performance?
No, they operate independently and do not impact system performance significantly. - Is Secure Enclave necessary for encryption?
It enhances encryption security but is not strictly necessary for all encryption tasks. - How do Secure Enclaves protect digital wallets?
They store private keys in an isolated, tamper-proof environment, preventing theft.
Secure Enclave Related Words
- Categories/Topics:
- Cybersecurity
- Biometric Security
- Cryptographic Computing
Did you know?
In 2017, a vulnerability called Meltdown targeted CPU security, but Secure Enclaves remained unaffected, proving their value in protecting sensitive data even in advanced cyberattacks.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment