SELinux (Security-Enhanced Linux)

Quick Navigation:
- SELinux Definition
- SELinux Explained Easy
- SELinux Origin
- SELinux Etymology
- SELinux Usage Trends
- SELinux Usage
- SELinux Examples in Context
- SELinux FAQ
- SELinux Related Words
SELinux Definition
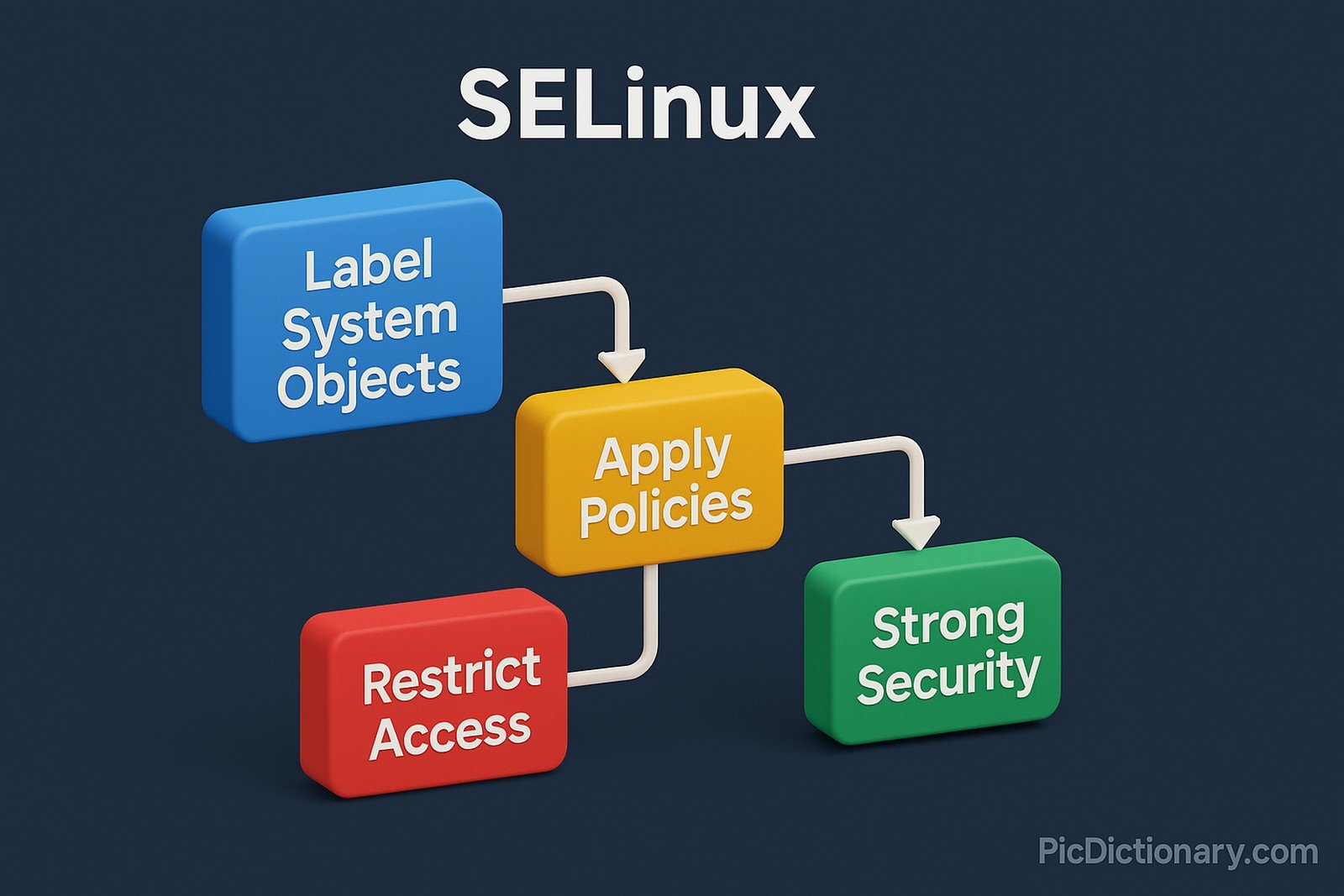
SELinux (Security-Enhanced Linux) is a security architecture integrated into the Linux kernel that provides mandatory access control (MAC). It restricts programs, users, and system services from accessing files or processes beyond what is explicitly permitted. SELinux uses policies to define what is allowed, adding a strong layer of security against potential exploits, privilege escalations, and malicious activities. Its core mechanism involves labeling system objects and enforcing rules.
SELinux Explained Easy
Imagine you have a toy box, and your parents only allow you to play with certain toys at certain times. They put labels on each toy and rules on when and how to play. SELinux works like that: it labels every part of the computer and applies strict rules so programs and users only do exactly what they are supposed to, nothing more.
SELinux Origin
SELinux was developed by the United States National Security Agency (NSA) in collaboration with the open-source community. First released in 2000, it was designed to strengthen the security posture of Linux systems, responding to growing concerns about system vulnerabilities and unauthorized access.
SELinux Etymology
The name “SELinux” comes from the merging of "Security-Enhanced" and "Linux," symbolizing an improvement in Linux’s security framework.
SELinux Usage Trends
SELinux has become widely adopted in enterprise environments, especially in security-focused infrastructures. From Red Hat Enterprise Linux (RHEL) to Fedora and CentOS, it is an integral component. System administrators and developers are increasingly using it to secure servers, containers, and cloud environments, with usage growing alongside cybersecurity threats.
SELinux Usage
- Formal/Technical Tagging:
- Linux Kernel Security
- Access Control
- Mandatory Access Control (MAC) - Typical Collocations:
- "SELinux policy"
- "SELinux enforcement mode"
- "disable SELinux temporarily"
- "audit logs for SELinux"
SELinux Examples in Context
- SELinux prevented a web server from accessing user files it wasn’t authorized to read.
- System administrators use SELinux policies to control application behavior in production servers.
- Docker containers on certain Linux distributions benefit from SELinux enforcement for added isolation.
SELinux FAQ
- What is SELinux?
SELinux is a Linux kernel security module providing mandatory access control to prevent unauthorized access. - Is SELinux only for enterprise use?
No, it can also be used on personal systems, although most home users disable it due to complexity. - How do you check if SELinux is enabled?
Run the commandsestatusin the terminal. - What happens if SELinux blocks something?
It logs the action and prevents the unauthorized behavior, but may sometimes require policy adjustment. - Can I disable SELinux?
Yes, but it is not recommended on production systems; instead, switch to permissive mode if troubleshooting. - What are SELinux modes?
The three modes are Enforcing, Permissive, and Disabled. - Is SELinux the same as AppArmor?
No, both provide similar functionalities but differ in implementation and policy structures. - Where are SELinux policies stored?
Policies are typically stored in/etc/selinux/. - How does SELinux protect containers?
It restricts containers' file and process access through labeling and predefined policies. - Can SELinux affect system performance?
Minimal impact on modern systems, though slight overhead can occur with complex policies.
SELinux Related Words
- Categories/Topics:
- Linux Security
- Kernel Modules
- Access Control
- Cybersecurity
Did you know?
SELinux once famously blocked a major government server misconfiguration that could have allowed unauthorized root access, demonstrating how preventive security layers can save systems from human error.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment