Spectre Vulnerability

Quick Navigation:
- Spectre Vulnerability Definition
- Spectre Vulnerability Explained Easy
- Spectre Vulnerability Origin
- Spectre Vulnerability Etymology
- Spectre Vulnerability Usage Trends
- Spectre Vulnerability Usage
- Spectre Vulnerability Examples in Context
- Spectre Vulnerability FAQ
- Spectre Vulnerability Related Words
Spectre Vulnerability Definition
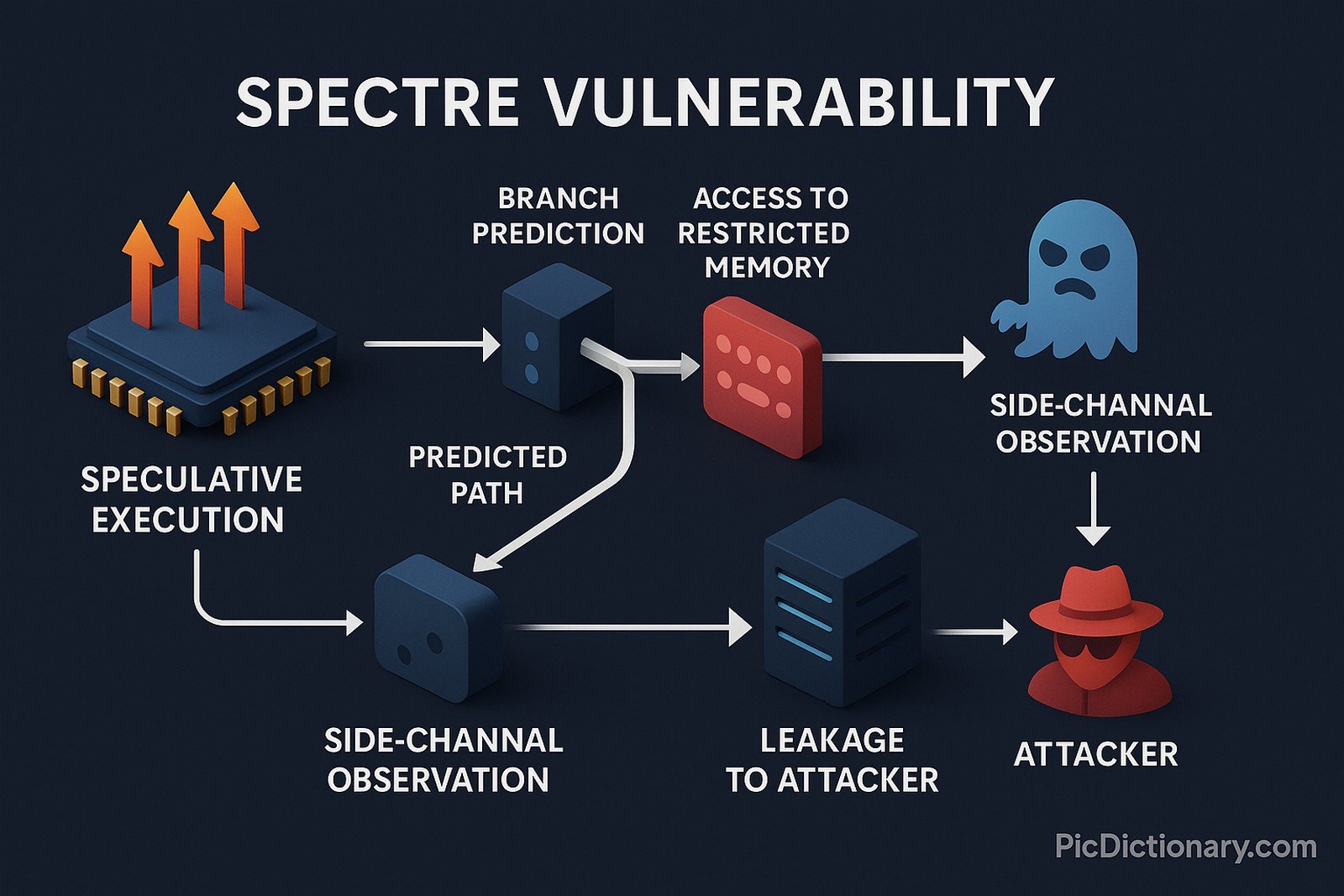
Spectre is a security vulnerability affecting modern processors that implement speculative execution. It exploits branch prediction and speculative execution techniques to trick a CPU into leaking sensitive information from memory. Unlike traditional attacks, Spectre does not exploit software bugs but rather a fundamental design feature of high-performance processors. It affects various architectures, including Intel, AMD, and ARM, making it a widespread concern in cybersecurity.
Spectre Vulnerability Explained Easy
Imagine you're trying to guess the answers to a test before your teacher gives them to you. You make some guesses and write them down, but suddenly your teacher changes the question, making your guesses incorrect. However, someone sneaky watched your guesses and learned some of the answers from your mistakes. This is how Spectre works—it tricks a computer into revealing secrets by making it guess things it shouldn't.
Spectre Vulnerability Origin
The Spectre vulnerability was discovered in 2017 by independent researchers from Google Project Zero and various academic institutions. It was publicly disclosed in January 2018 alongside another similar attack, Meltdown. These vulnerabilities shocked the cybersecurity world because they showed that fundamental CPU performance optimizations could be exploited for security breaches.
Spectre Vulnerability Etymology
The name “Spectre” is derived from the word “speculative,” referring to the speculative execution process that the attack manipulates. It also hints at the difficulty in fully eliminating it, as it "haunts" modern processors.
Spectre Vulnerability Usage Trends
Since its discovery, Spectre has influenced security practices globally. It has led to major redesigns in CPU architectures, security patches in operating systems, and ongoing research into mitigating speculative execution attacks. The challenge remains that Spectre-based exploits are difficult to detect and mitigate without significant performance overhead, making it a persistent cybersecurity concern.
Spectre Vulnerability Usage
- Formal/Technical Tagging:
- Cybersecurity
- Processor Architecture
- Speculative Execution - Typical Collocations:
- "Spectre attack mitigation"
- "Speculative execution vulnerability"
- "Spectre exploit in CPUs"
- "Spectre patch performance impact"
Spectre Vulnerability Examples in Context
- Security researchers demonstrated that Spectre could allow attackers to read private data from a victim’s browser, bypassing security boundaries.
- Cloud computing services have implemented Spectre mitigations to prevent cross-tenant data leakage.
- Modern CPUs now include hardware-based protections against Spectre, but software patches remain necessary.
Spectre Vulnerability FAQ
- What is Spectre?
Spectre is a security vulnerability that exploits speculative execution in modern CPUs to leak sensitive data. - How does Spectre work?
It tricks a CPU into executing incorrect instructions speculatively, allowing an attacker to infer private data through side channels. - Is Spectre different from Meltdown?
Yes. While both exploit speculative execution, Meltdown allows access to restricted memory, whereas Spectre tricks applications into leaking their own data. - Which processors are affected by Spectre?
Spectre affects a wide range of Intel, AMD, and ARM processors. - Can Spectre be patched?
There are mitigations, but no perfect fix. Patches reduce risk, but hardware redesigns are the most effective long-term solution. - Does Spectre impact system performance?
Yes. Mitigations, such as disabling speculative execution, can lead to performance slowdowns. - How can I protect my system from Spectre?
Keep your operating system, browser, and firmware updated with the latest security patches. - Is Spectre still a threat in 2024?
Yes. New Spectre variants continue to be discovered, requiring ongoing mitigations. - Can Spectre be exploited remotely?
Yes. Web browsers, particularly JavaScript engines, are a common attack vector for Spectre-based exploits. - Are newer CPUs immune to Spectre?
While newer processors include hardware mitigations, Spectre-like vulnerabilities still require ongoing security measures.
Spectre Vulnerability Related Words
- Categories/Topics:
- Cybersecurity
- Processor Security
- Side-Channel Attacks
Did you know?
The Spectre vulnerability was so severe that it led to emergency patches across major operating systems, including Windows, macOS, and Linux. Some cloud computing companies even had to reboot entire data centers to apply fixes, affecting millions of users worldwide.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment