Data Execution Prevention (DEP)

Quick Navigation:
- Data Execution Prevention (DEP) Definition
- Data Execution Prevention (DEP) Explained Easy
- Data Execution Prevention (DEP) Origin
- Data Execution Prevention (DEP) Etymology
- Data Execution Prevention (DEP) Usage Trends
- Data Execution Prevention (DEP) Usage
- Data Execution Prevention (DEP) Examples in Context
- Data Execution Prevention (DEP) FAQ
- Data Execution Prevention (DEP) Related Words
Data Execution Prevention (DEP) Definition
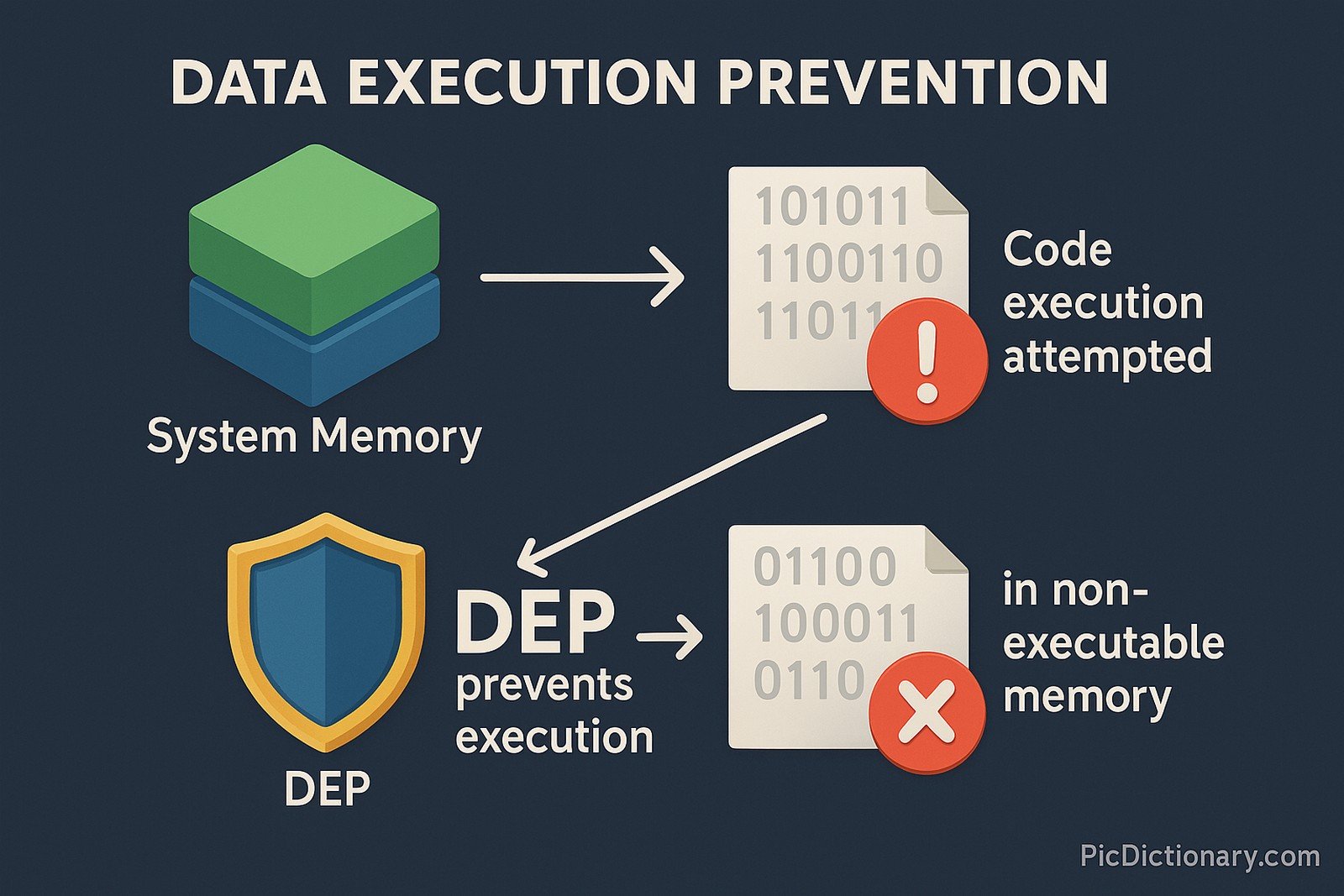
Data Execution Prevention (DEP) is a security feature included in modern operating systems that prevents code from being executed in certain regions of memory marked as non-executable. This protection helps block malicious attacks such as buffer overflow exploits by stopping harmful code from running in protected areas. DEP operates in two forms: hardware-enforced and software-enforced, each working to safeguard system memory. Hardware-based DEP uses CPU features to prevent code execution, while software-based DEP can mark specific memory locations as non-executable.
Data Execution Prevention (DEP) Explained Easy
Imagine your computer has special "Do Not Enter" zones where no programs are allowed to run. These areas are like safe rooms. DEP makes sure bad programs can't sneak into those safe rooms and cause trouble. It watches over these areas and if anything tries to run there, it stops it right away, keeping your computer safe.
Data Execution Prevention (DEP) Origin
DEP was introduced by Microsoft in Windows XP Service Pack 2 as part of its enhanced security strategy to reduce vulnerabilities exploited by malicious attacks. It was developed in collaboration with hardware vendors who supported CPU-level enforcement. Over time, DEP has become a standard security feature across various operating systems.
Data Execution Prevention (DEP) Etymology
The phrase “data execution prevention” describes the practice of stopping the execution of instructions in memory areas designated for storing data only.
Data Execution Prevention (DEP) Usage Trends
Since its introduction, DEP has gained widespread adoption in both consumer and enterprise systems. Security professionals consider it a key defense mechanism in preventing common exploits. With evolving cybersecurity threats, DEP has been integrated alongside other protective technologies like Address Space Layout Randomization (ASLR) and Control Flow Guard (CFG) for layered defense.
Data Execution Prevention (DEP) Usage
- Formal/Technical Tagging:
- Computer Security
- Operating Systems
- Memory Protection - Typical Collocations:
- "enable Data Execution Prevention"
- "hardware-based DEP"
- "DEP protection settings"
- "buffer overflow prevention with DEP"
Data Execution Prevention (DEP) Examples in Context
- DEP helped stop a malicious script from running in the memory space reserved for documents.
- System administrators often configure DEP to protect both essential system services and custom applications.
- DEP combined with ASLR adds a strong security layer against common memory-based attacks.
Data Execution Prevention (DEP) FAQ
- What is Data Execution Prevention (DEP)?
DEP is a security feature that stops code from running in protected memory regions to prevent exploits. - How does DEP protect a system?
It monitors specific areas of memory and blocks code execution where only data storage is allowed. - Is DEP hardware-based or software-based?
DEP can be hardware-enforced by the CPU or software-enforced by the operating system. - Can DEP cause application compatibility issues?
Yes, some older applications may not function correctly if they try to execute code in non-executable memory. - How can I check if DEP is enabled on Windows?
You can check DEP settings via the System Properties under Performance options. - Is DEP available in Linux and macOS?
Yes, both Linux and macOS implement similar memory protection mechanisms, although naming conventions may differ. - Does DEP protect against all security threats?
No, DEP is one layer of defense and should be used with other security measures. - Can DEP be disabled?
While possible, disabling DEP is not recommended as it weakens system security. - What attacks does DEP help prevent?
DEP helps block buffer overflow attacks and similar memory-based exploits. - Is DEP enabled by default?
Yes, modern operating systems have DEP enabled by default for critical processes.
Data Execution Prevention (DEP) Related Words
- Categories/Topics:
- Cybersecurity
- Buffer Overflow Protection
- Memory Management
Did you know?
In 2004, DEP’s introduction in Windows XP Service Pack 2 played a pivotal role in stopping the spread of the Sasser worm, which exploited a buffer overflow vulnerability. This event highlighted how memory protection features could significantly reduce the impact of large-scale malware outbreaks.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment