Mobile Device Management (MDM)

Quick Navigation:
- Mobile Device Management (MDM) Definition
- Mobile Device Management (MDM) Explained Easy
- Mobile Device Management (MDM) Origin
- Mobile Device Management (MDM) Etymology
- Mobile Device Management (MDM) Usage Trends
- Mobile Device Management (MDM) Usage
- Mobile Device Management (MDM) Examples in Context
- Mobile Device Management (MDM) FAQ
- Mobile Device Management (MDM) Related Words
Mobile Device Management (MDM) Definition
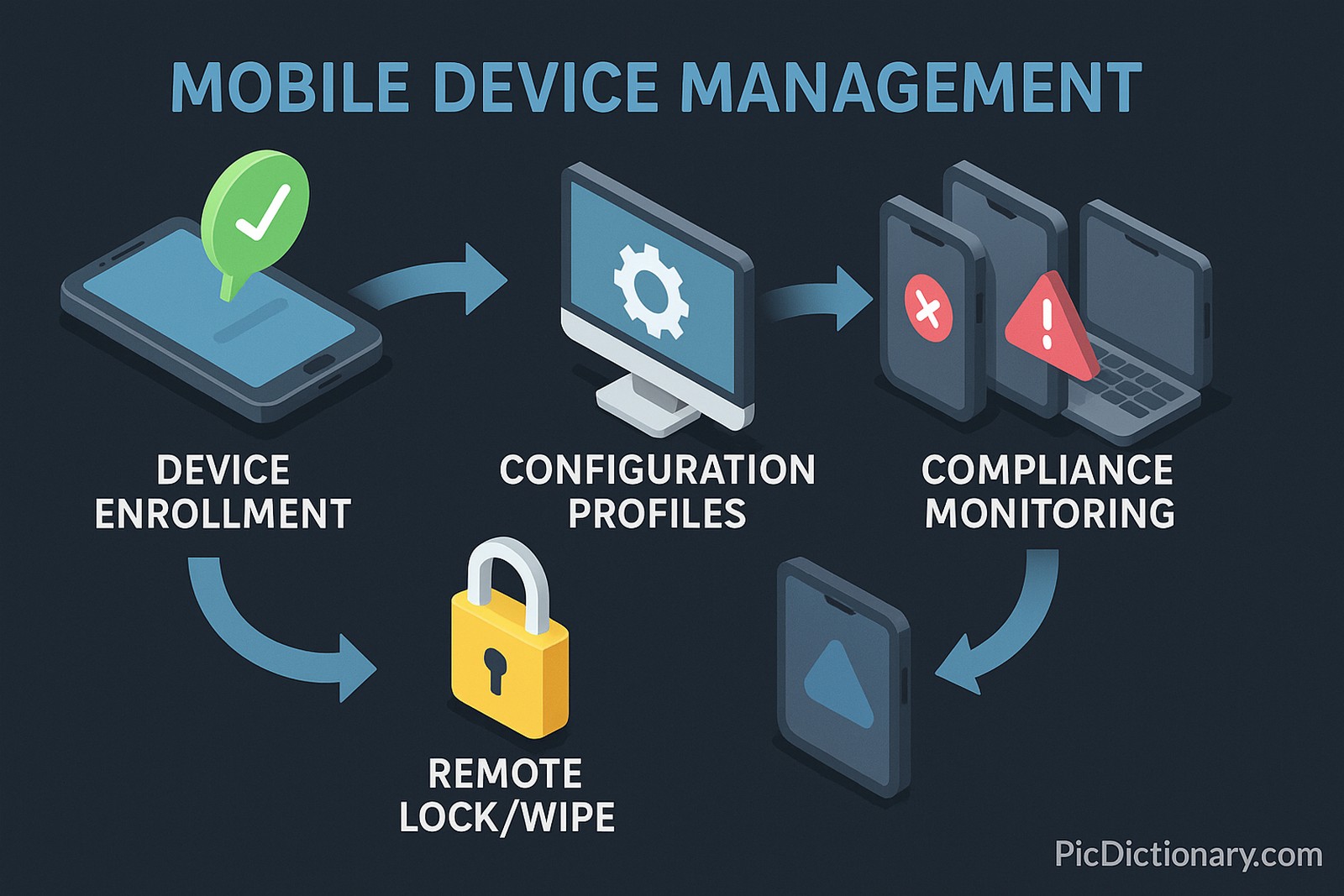
Mobile Device Management (MDM) refers to a set of technologies, policies, and practices used by organizations to monitor, manage, and secure employees’ mobile devices, such as smartphones, tablets, and laptops. MDM enables IT administrators to remotely configure devices, enforce security policies, deploy applications, track device locations, and wipe data in case of loss or theft. Common features of MDM solutions include device enrollment, remote lock/wipe, app management, and compliance monitoring. MDM is essential for maintaining data security in enterprise environments, especially with the rise of BYOD (Bring Your Own Device) practices.
Mobile Device Management (MDM) Explained Easy
Think of MDM like a remote control for your school’s tablets. The teacher (company IT) can make sure everyone has the right apps, that the devices are safe, and can even lock or reset them if someone loses one. It’s a smart way for companies to take care of all their devices without holding each one in their hands.
Mobile Device Management (MDM) Origin
Mobile Device Management (MDM) emerged in the late 2000s, following the explosion of smartphones and tablets in business use. As organizations began allowing employees to use their own devices, security and management challenges increased. MDM solutions developed as a response, evolving from basic device configuration tools to comprehensive enterprise mobility management platforms.
Mobile Device Management (MDM) Etymology
The term combines "mobile device" (portable computing equipment) with "management" (the act of controlling or overseeing something).
Mobile Device Management (MDM) Usage Trends
MDM adoption has grown significantly with the rise of remote work, hybrid environments, and BYOD policies. Modern MDM platforms now incorporate features like zero-touch deployment, AI-based threat detection, and integration with identity management. Sectors like healthcare, finance, and education are leading adopters, relying on MDM to protect sensitive information and maintain regulatory compliance.
Mobile Device Management (MDM) Usage
- Formal/Technical Tagging:
- Enterprise Mobility Management
- Endpoint Security
- Device Administration - Typical Collocations:
- "MDM solution"
- "device enrollment"
- "remote wipe"
- "BYOD policy management"
Mobile Device Management (MDM) Examples in Context
- A company uses MDM to ensure all employees’ smartphones have encrypted email access.
- Schools use MDM to control the apps students can install on school-issued tablets.
- Hospitals implement MDM to secure patient data on doctors’ mobile devices.
Mobile Device Management (MDM) FAQ
- What is Mobile Device Management (MDM)?
Mobile Device Management (MDM) refers to technologies that help manage and secure mobile devices used within an organization. - How does MDM work?
It works by enrolling devices into an MDM platform, which allows IT to configure settings, deploy apps, and enforce security remotely. - What devices can be managed with MDM?
MDM can manage smartphones, tablets, laptops, and even some smartwatches. - Why is MDM important?
MDM ensures data security, reduces risks from lost or stolen devices, and helps maintain compliance. - What industries use MDM the most?
Healthcare, education, finance, and large enterprises rely heavily on MDM. - Can MDM track device location?
Yes, most MDM solutions offer GPS tracking for devices. - Is MDM only for company-owned devices?
No, MDM can also manage personal devices under BYOD policies. - Can MDM delete data remotely?
Yes, IT can perform a remote wipe in case a device is lost or compromised. - Does MDM slow down devices?
Properly implemented MDM should not noticeably slow down devices. - Is MDM secure?
Yes, MDM solutions are designed with strong security features and encryption to protect data.
Mobile Device Management (MDM) Related Words
- Categories/Topics:
- Enterprise Security
- Endpoint Management
- BYOD (Bring Your Own Device)
Did you know?
In 2019, a major airline used MDM to ground thousands of devices that were found to have a critical vulnerability, preventing potential safety issues mid-flight. This real-world example shows how powerful MDM can be in crisis prevention.
Authors | Arjun Vishnu | @ArjunAndVishnu

PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.
I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.















Comments (0)
Comments powered by CComment