Remote Attestation

Quick Navigation:
- Remote Attestation Definition
- Remote Attestation Explained Easy
- Remote Attestation Origin
- Remote Attestation Etymology
- Remote Attestation Usage Trends
- Remote Attestation Usage
- Remote Attestation Examples in Context
- Remote Attestation FAQ
- Remote Attestation Related Words
Remote Attestation Definition
Remote attestation is a security mechanism that enables a system to verify the integrity of a remote device. It ensures that software and hardware running on a system remain untampered using cryptographic proofs. This technology is widely used in cloud computing and IoT security to maintain trust in distributed systems.
Remote Attestation Explained Easy
Imagine playing an online game where a referee checks that no one is cheating. Remote attestation works similarly—it verifies that a system is running genuine, untampered software before allowing interactions.
Remote Attestation Origin
The concept emerged alongside secure computing initiatives, gaining prominence with the rise of TPMs and cloud security frameworks in the early 2000s.
Remote Attestation Etymology
The term "attestation" comes from the Latin word "attestari," meaning to bear witness. In computing, it signifies proof of integrity.
Remote Attestation Usage Trends
Remote attestation is increasingly used in cloud security, IoT devices, and Zero Trust models, ensuring only verified systems can access sensitive resources.
Remote Attestation Usage
- Formal/Technical Tagging:
- Trusted Computing
- Security Protocols
- Cryptographic Verification - Typical Collocations:
- "Remote attestation protocol"
- "TPM-based remote attestation"
- "Cloud security with remote attestation"
Remote Attestation Examples in Context
- Cloud providers use remote attestation to ensure virtual machines are running untampered software.
- Intel SGX employs remote attestation to validate applications inside secure enclaves.
- IoT devices rely on remote attestation to maintain operational security.
Remote Attestation FAQ
- What is remote attestation?
A security mechanism that allows devices to prove their integrity remotely. - Why is remote attestation important?
It prevents unauthorized modifications in computing environments. - How does remote attestation work?
A system generates a cryptographic proof, which is verified remotely. - What role do TPMs play?
TPMs provide cryptographic functions supporting remote attestation. - Can remote attestation be bypassed?
Strong encryption minimizes risks, but attacks on verification processes exist. - How does remote attestation fit in Zero Trust?
It continuously verifies system integrity before granting access. - Is remote attestation used in cloud computing?
Yes, it is vital for securing virtual machines. - What is Intel SGX remote attestation?
A method to ensure applications inside Intel’s secure enclaves remain untampered. - Can IoT devices use remote attestation?
Yes, it verifies device software authenticity. - Which industries benefit from remote attestation?
Cloud computing, healthcare, finance, and government security sectors.
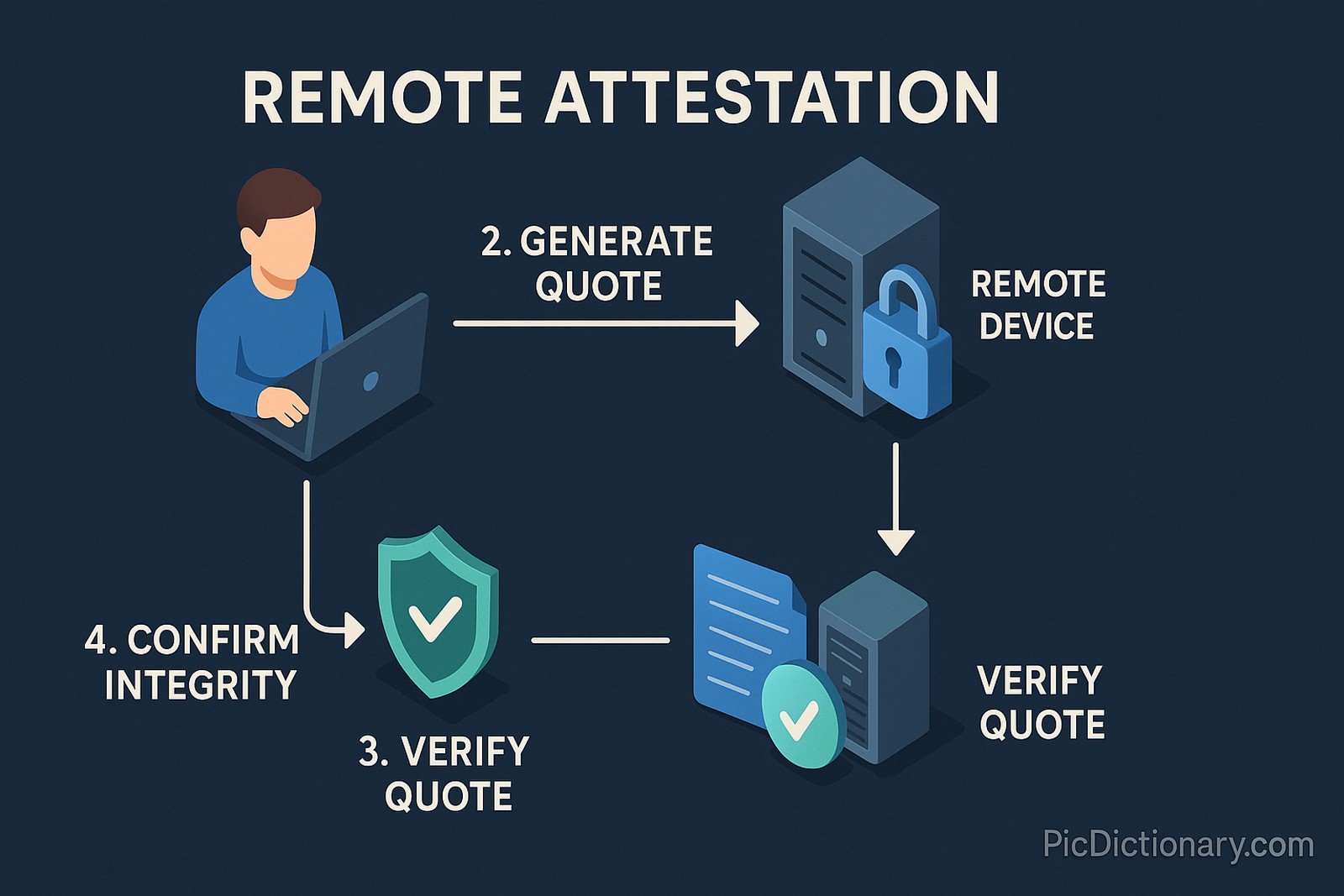
Remote Attestation Related Words
- Categories/Topics:
- Trusted Computing
- Secure Boot
- Cryptographic Attestation
Did you know?
Remote attestation was used to secure cloud-based voting systems, ensuring election software integrity.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment