Side-Channel Attacks

Quick Navigation:
- Side-Channel Attacks Definition
- Side-Channel Attacks Explained Easy
- Side-Channel Attacks Origin
- Side-Channel Attacks Etymology
- Side-Channel Attacks Usage Trends
- Side-Channel Attacks Usage
- Side-Channel Attacks Examples in Context
- Side-Channel Attacks FAQ
- Side-Channel Attacks Related Words
Side-Channel Attacks Definition
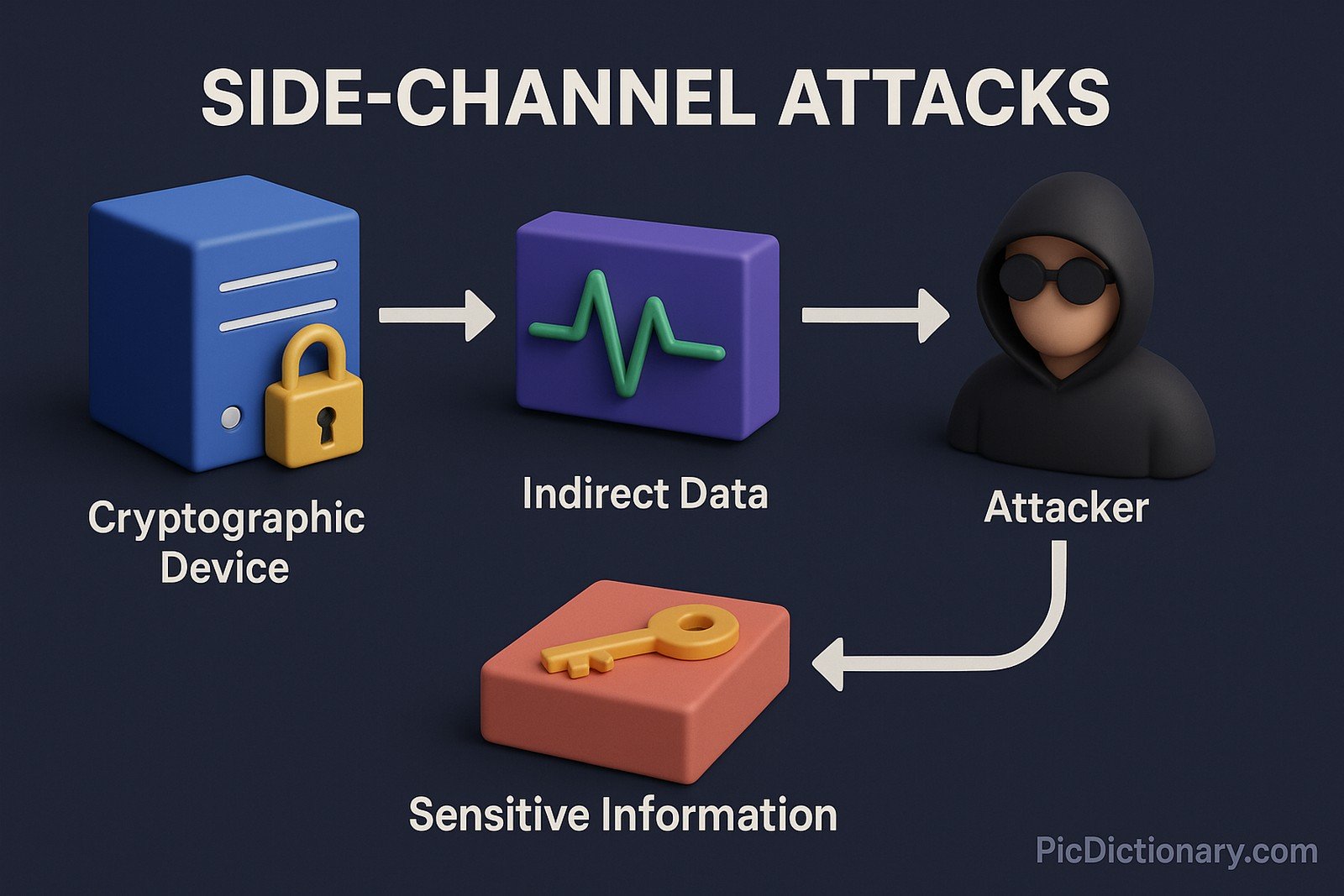
A side-channel attack is a security exploit that gains information from the physical implementation of a cryptographic system rather than exploiting weaknesses in the algorithm itself. These attacks analyze indirect data, such as power consumption, electromagnetic leaks, or timing variations, to extract sensitive information like encryption keys. Side-channel attacks are particularly dangerous because they bypass traditional cryptographic protections and can be executed without directly interfering with a system’s operations.
Side-Channel Attacks Explained Easy
Imagine you’re trying to guess a friend’s password. Instead of asking them directly, you watch their fingers move on the keyboard or listen to how they type. A side-channel attack works the same way: instead of cracking a password or hacking directly, attackers observe tiny details, like how long a computer takes to process a request, to figure out secret information.
Side-Channel Attacks Origin
Side-channel attacks have been studied since the 1960s, but they gained significant attention in the 1990s when researchers demonstrated practical attacks on cryptographic hardware. As computing devices became more advanced, attackers found new ways to exploit physical characteristics, making side-channel attacks a growing concern in modern cybersecurity.
Side-Channel Attacks Etymology
The term “side-channel” refers to an unintended or indirect pathway through which information is leaked. Unlike direct attacks that target the main communication channel, side-channel attacks use additional, often overlooked sources of data to infer secret information.
Side-Channel Attacks Usage Trends
With the rise of IoT devices, cloud computing, and hardware-based security measures, side-channel attacks have become a major concern. Researchers continuously study new countermeasures, but attackers also innovate, making it an ongoing cybersecurity arms race. Notably, side-channel attacks have been used to compromise high-profile encryption standards like RSA and AES.
Side-Channel Attacks Usage
- Formal/Technical Tagging:
- Cryptography
- Cybersecurity
- Hardware Security - Typical Collocations:
- "side-channel attack vulnerability"
- "mitigating side-channel attacks"
- "power analysis attack on encryption"
- "timing side-channel exploit"
Side-Channel Attacks Examples in Context
- In 2018, researchers demonstrated a side-channel attack on Intel processors, exposing sensitive information through speculative execution vulnerabilities.
- Smartcards used for secure transactions have been targeted with power analysis attacks to extract cryptographic keys.
- Side-channel attacks on cloud environments allow attackers to infer data from virtual machines running on shared hardware.
Side-Channel Attacks FAQ
- What is a side-channel attack?
A side-channel attack is a hacking technique that gathers information from a system’s physical properties rather than its algorithm. - How do side-channel attacks work?
These attacks analyze unintended data leaks, such as power usage, electromagnetic radiation, or timing delays, to extract confidential information. - Are side-channel attacks a real-world threat?
Yes, they have been used in practice against cryptographic devices, including credit cards and encryption software. - Can software alone prevent side-channel attacks?
No, countermeasures often require both hardware and software protections, such as masking, noise injection, and secure architectures. - Which cryptographic algorithms are vulnerable to side-channel attacks?
Algorithms like RSA, AES, and ECC have been shown to be vulnerable if implemented without side-channel protection. - What is a power analysis attack?
A power analysis attack measures the power consumption of a device to deduce its internal operations and extract sensitive data. - Can side-channel attacks be performed remotely?
Some advanced attacks, such as cache-timing attacks, can be executed remotely in cloud computing environments. - How do companies defend against side-channel attacks?
Companies use countermeasures like randomization techniques, hardware shielding, and constant-time algorithms to reduce leakage. - Are quantum computers vulnerable to side-channel attacks?
While quantum cryptography offers stronger security, the physical nature of quantum hardware may still be susceptible to side-channel exploits. - What are some famous examples of side-channel attacks?
Notable examples include the Spectre and Meltdown vulnerabilities, which exploited timing-based side-channel attacks on modern processors.
Side-Channel Attacks Related Words
- Categories/Topics:
- Cryptographic Security
- Cybersecurity Threats
- Hardware Exploits
Did you know?
In 2017, a group of researchers discovered that sound waves could be used as a side-channel attack method. By recording the noises emitted by a computer’s cooling fan, they successfully extracted encryption keys, proving that even seemingly unrelated physical properties can leak sensitive data.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment