Trusted Execution Environment (TEE)

Quick Navigation:
- Trusted Execution Environment (TEE) Definition
- Trusted Execution Environment (TEE) Explained Easy
- Trusted Execution Environment (TEE) Origin
- Trusted Execution Environment (TEE) Etymology
- Trusted Execution Environment (TEE) Usage Trends
- Trusted Execution Environment (TEE) Usage
- Trusted Execution Environment (TEE) Examples in Context
- Trusted Execution Environment (TEE) FAQ
- Trusted Execution Environment (TEE) Related Words
Trusted Execution Environment (TEE) Definition
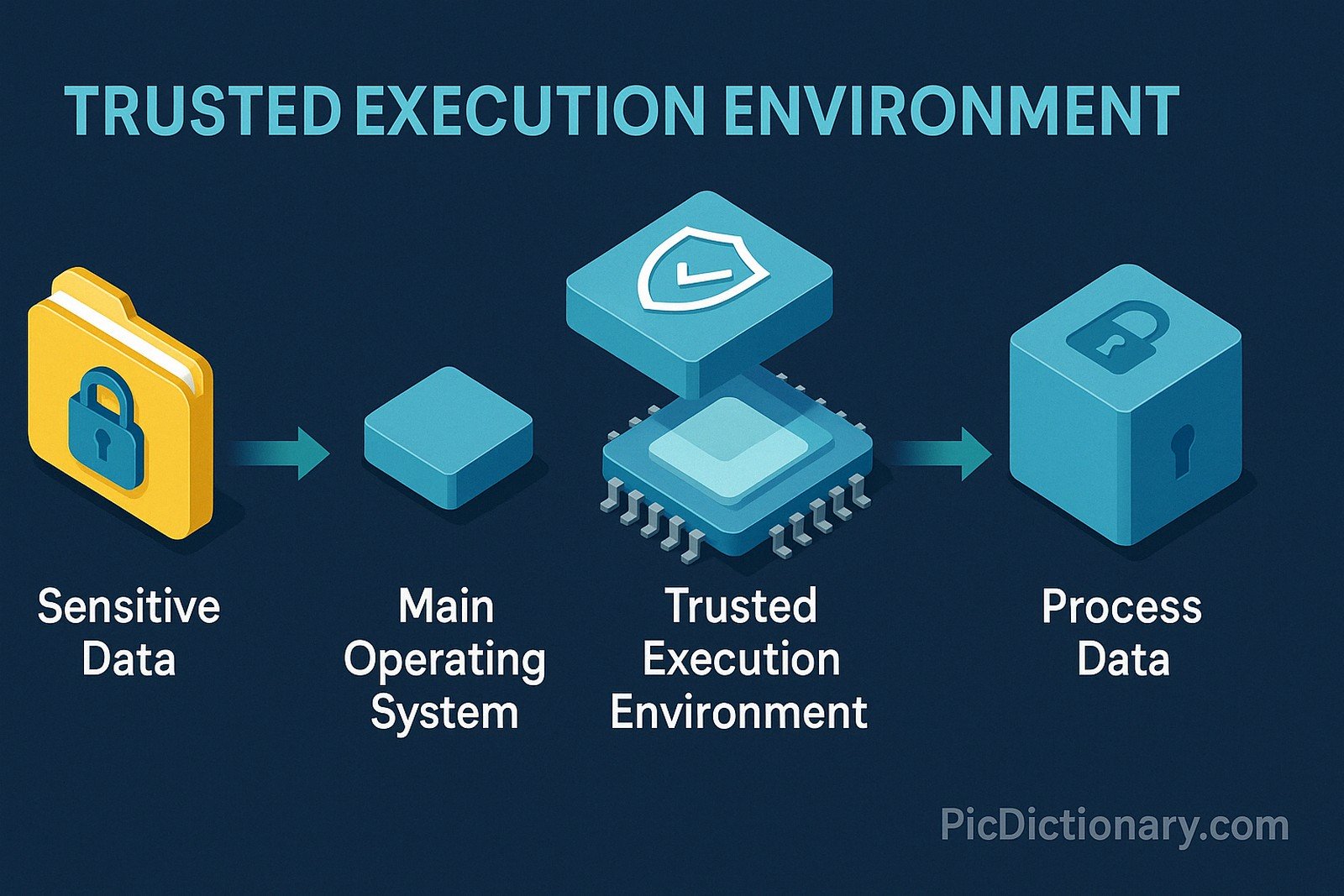
A Trusted Execution Environment (TEE) is a secure area within a processor that ensures sensitive data is stored, processed, and protected in an isolated environment. It prevents unauthorized access or tampering by separating critical code and data from the main operating system. TEEs provide confidentiality, integrity, and authentication for applications handling sensitive tasks like cryptographic operations, digital rights management, and secure payments.
Trusted Execution Environment (TEE) Explained Easy
Imagine having a secret safe inside your computer, where only trusted programs can go to open or store secret items. No one else, not even most parts of the computer, can peek inside. That’s what a Trusted Execution Environment does — it’s a private, safe space for your computer’s most important secrets.
Trusted Execution Environment (TEE) Origin
The concept of TEEs emerged from the need for stronger security in consumer devices and enterprise environments. Early implementations were seen in mobile processors to protect user data and cryptographic keys, gradually becoming integral in IoT devices and cloud computing infrastructure.
Trusted Execution Environment (TEE) Etymology
The term combines "trusted" (indicating reliability and security), "execution" (referring to running code), and "environment" (a contained area where tasks are performed).
Trusted Execution Environment (TEE) Usage Trends
Over the past decade, TEEs have seen rapid adoption across industries like banking, healthcare, and mobile technology. Their usage is growing in blockchain applications, secure authentication solutions, and confidential cloud computing. With increasing cyber threats, demand for hardware-based security features continues to rise.
Trusted Execution Environment (TEE) Usage
- Formal/Technical Tagging:
- Hardware Security
- Cryptography
- Secure Computing
- Confidential Computing - Typical Collocations:
- "TEE-based security"
- "hardware-backed trusted execution environment"
- "TEE application"
- "trusted enclave"
- "secure key storage in TEE"
Trusted Execution Environment (TEE) Examples in Context
- Smartphones use TEEs to protect fingerprint and face recognition data.
- TEEs enable secure PIN verification in mobile banking apps.
- Cloud providers utilize TEEs to run confidential workloads that protect sensitive data from other tenants.
Trusted Execution Environment (TEE) FAQ
- What is a Trusted Execution Environment?
A TEE is a secure area in a device’s processor that protects sensitive data and code from unauthorized access. - Why is a TEE important?
It allows applications to safely handle sensitive operations like cryptographic processing and secure transactions. - How does a TEE work?
It isolates sensitive computations and data from the rest of the system, allowing only verified code to access it. - Is a TEE hardware or software?
A TEE is a hardware-based security feature, although it works alongside trusted software components. - Where are TEEs commonly used?
They are found in smartphones, IoT devices, cloud environments, and secure financial systems. - Can TEEs be hacked?
Though designed to be highly secure, vulnerabilities can arise if the underlying hardware or firmware has flaws. - What companies provide TEEs?
Companies like ARM (TrustZone), Intel (SGX), and AMD (SEV) provide TEE solutions. - Are TEEs used in blockchain?
Yes, TEEs help secure smart contracts and confidential transactions in blockchain applications. - How do TEEs protect keys?
They store cryptographic keys in hardware-protected areas that are inaccessible to unauthorized applications. - Can a TEE protect against malware?
A TEE can protect sensitive operations from malware running in the regular operating system environment.
Trusted Execution Environment (TEE) Related Words
- Categories/Topics:
- Hardware Security
- Cryptography
- Secure Computing
- Confidential Computing
Did you know?
The first commercial smartphone to use TEE-based fingerprint authentication was the iPhone 5S in 2013, setting the stage for biometric security powered by trusted hardware environments.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment