DMZ (Demilitarized Zone)
Quick Navigation:
- DMZ Definition
- DMZ Explained Easy
- DMZ Origin
- DMZ Etymology
- DMZ Usage Trends
- DMZ Usage
- DMZ Examples in Context
- DMZ FAQ
- DMZ Related Words
DMZ Definition
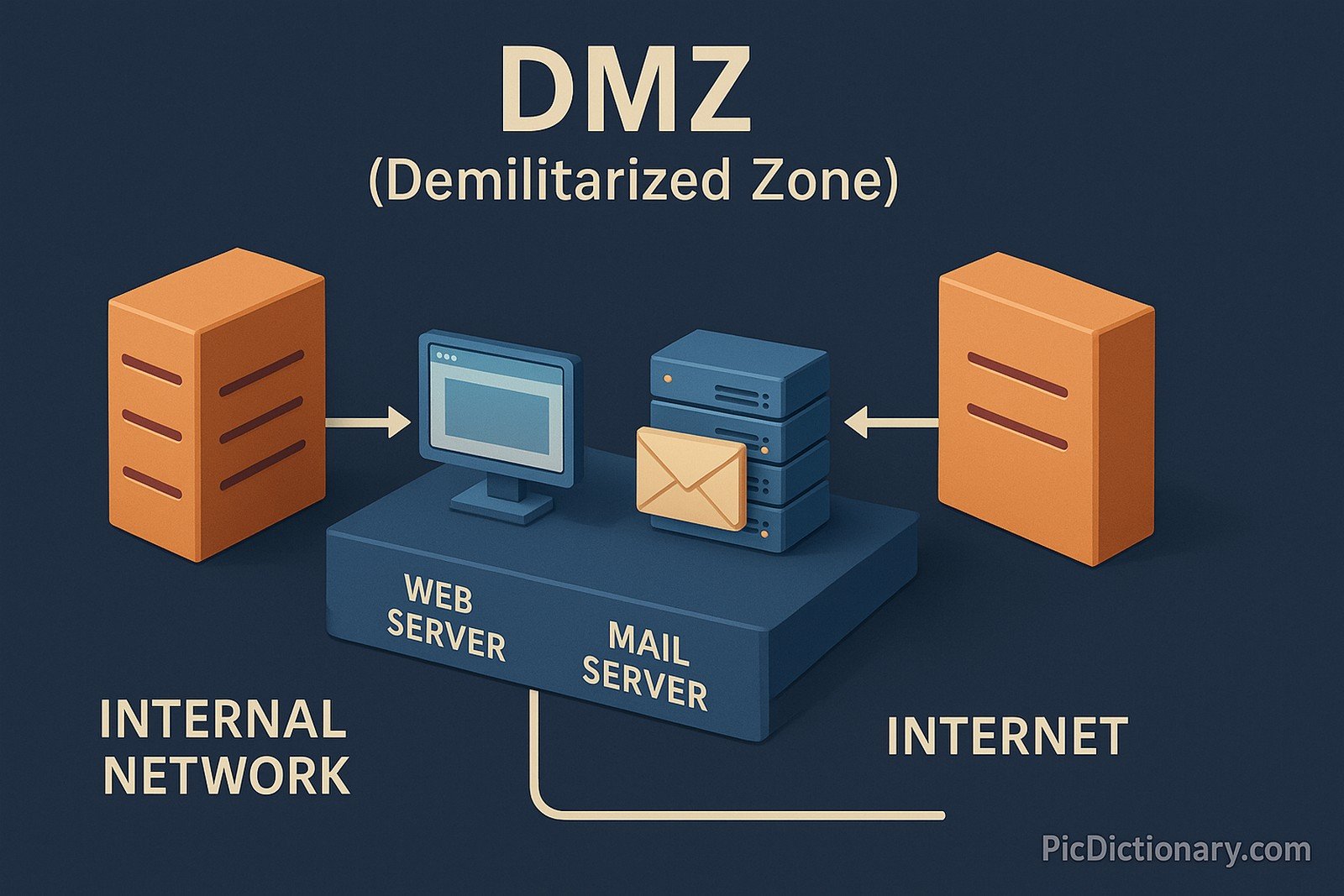
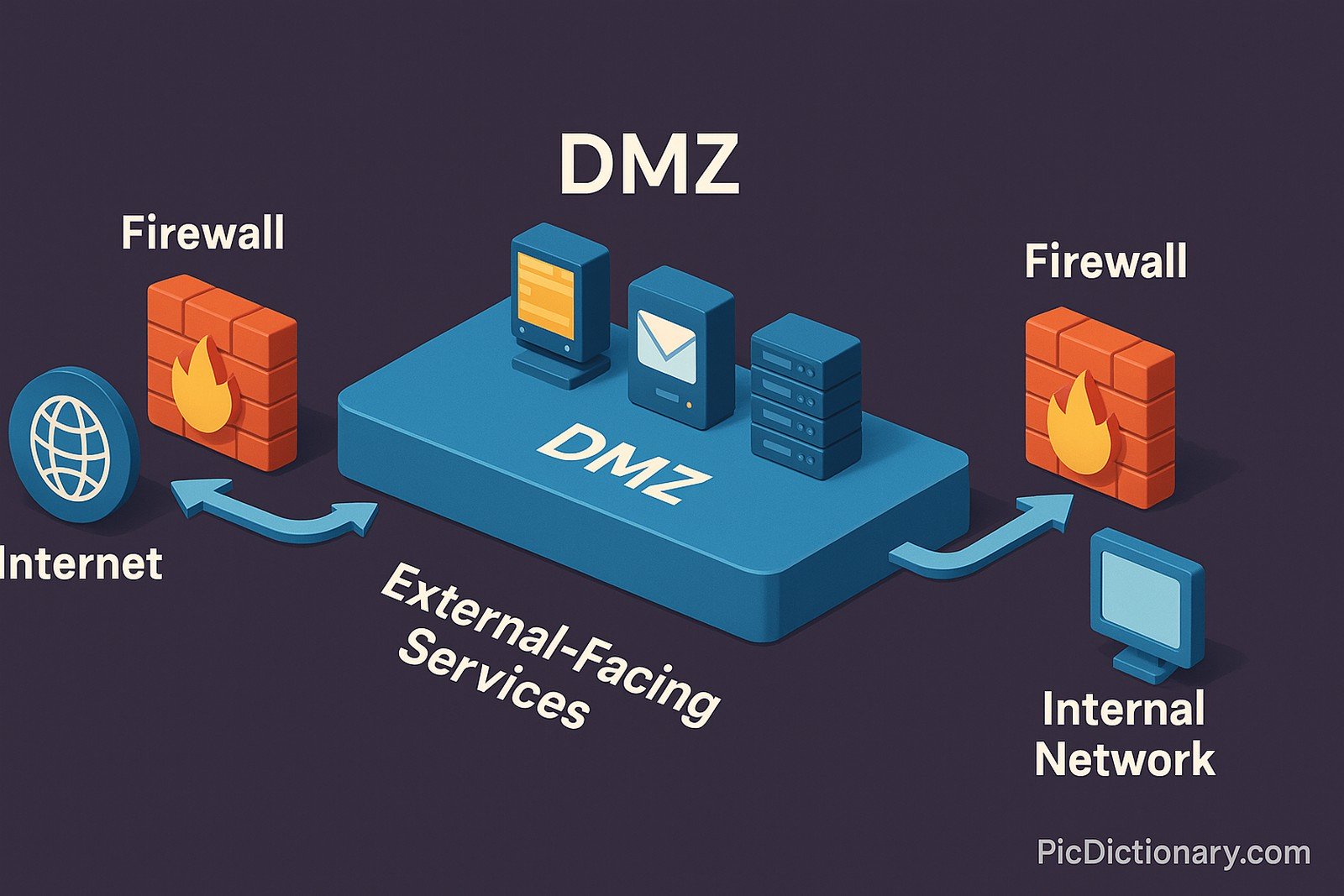
A DMZ, or Demilitarized Zone, in computer networking is a physical or logical subnetwork that separates an internal local area network (LAN) from untrusted external networks, usually the Internet. The DMZ adds an extra layer of security to an organization's network, acting as a buffer zone where external-facing services (like web servers, email servers, and DNS servers) reside. This setup ensures that even if a server in the DMZ is compromised, the internal network remains protected.
DMZ Explained Easy
Imagine your home has a front yard with a gate and a secure house behind it. The front yard is where visitors can come, but they can't enter your house directly. A DMZ is like that front yard — it allows outsiders to interact with certain services while keeping the internal parts of your network safe.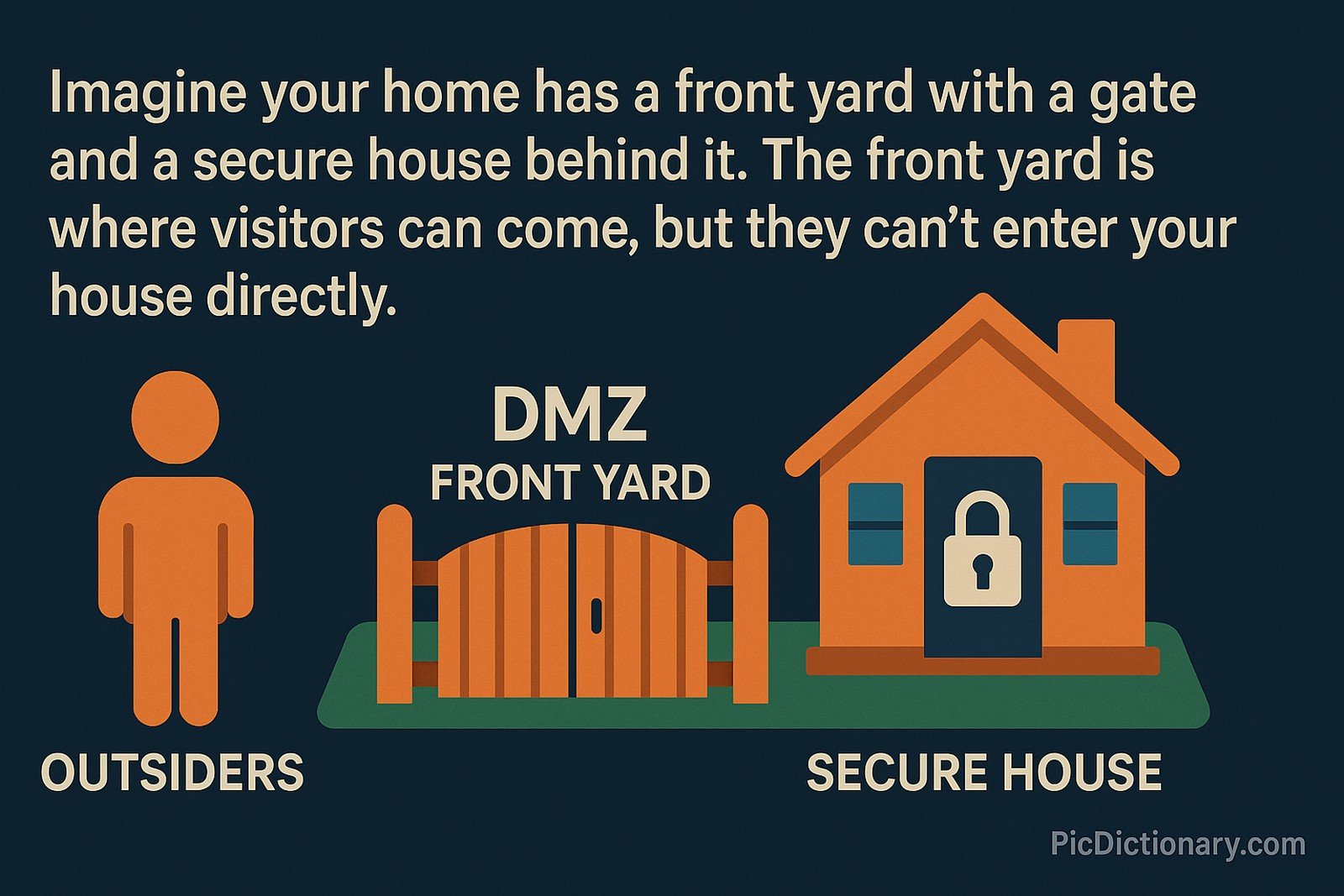
DMZ Origin
The concept of a DMZ in networking is derived from military terminology, where a demilitarized zone is an area where military forces are not allowed. In computing, it became widely adopted in the early days of the Internet when organizations needed to expose services to the public while protecting their core systems.
DMZ Etymology
The term is adapted from military language and was introduced into networking contexts to describe a zone with limited trust and restricted access.
DMZ Usage Trends
As cyber threats have grown, the use of DMZs has evolved. Modern DMZs now often incorporate cloud services, virtual networks, and micro-segmentation to further enhance security. While traditional DMZs are still used, more organizations are turning to software-defined perimeters and zero-trust architectures.
DMZ Usage
- Formal/Technical Tagging:
- Network Security
- Perimeter Defense
- Firewall Configuration - Typical Collocations:
- "DMZ configuration"
- "place it in the DMZ"
- "DMZ security"
- "DMZ firewall rules"
DMZ Examples in Context
- A company's public web server is placed in the DMZ to protect internal databases.
- Firewalls use specific rules to control traffic between the DMZ, the internal network, and the Internet.
- DMZ setups are common in hosting environments to isolate services exposed to the public.
DMZ FAQ
- What is a DMZ in networking?
A DMZ is a subnetwork that adds a security layer between an internal network and external threats. - Why do companies use a DMZ?
It protects sensitive internal systems by isolating public-facing servers. - Is a DMZ still relevant with cloud services?
Yes, DMZ principles apply to cloud architectures for secure external-facing services. - What devices are placed in a DMZ?
Common devices include web servers, mail servers, and DNS servers. - Does having a DMZ prevent all cyberattacks?
No, but it reduces risk by isolating potentially vulnerable systems. - How does a DMZ work with firewalls?
Firewalls manage and restrict traffic to and from the DMZ, internal network, and the Internet. - Can home networks use a DMZ?
Yes, some routers allow DMZ configurations for gaming consoles or specific devices. - Is DMZ part of a zero-trust strategy?
It complements zero-trust by creating segmented and monitored environments. - What are common DMZ vulnerabilities?
Misconfigurations, outdated services, and overly permissive firewall rules. - Should DMZ services be regularly updated?
Absolutely, as public-facing systems are prime targets for attackers.
DMZ Related Words
- Categories/Topics:
- Network Security
- Firewall
- Intrusion Prevention
Did you know?
The first usage of the term DMZ in computing dates back to the 1990s when organizations began implementing perimeter defenses against rapidly increasing cyber threats. Today, DMZs are an integral part of layered security strategies in both physical and cloud environments.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment