Memory Forensics
Quick Navigation:
- Memory Forensics Definition
- Memory Forensics Explained Easy
- Memory Forensics Origin
- Memory Forensics Etymology
- Memory Forensics Usage Trends
- Memory Forensics Usage
- Memory Forensics Examples in Context
- Memory Forensics FAQ
- Memory Forensics Related Words
Memory Forensics Definition
Memory forensics is the process of analyzing a computer's volatile memory (RAM) to extract valuable forensic artifacts for security investigations, incident response, and digital forensics. It helps detect malicious software, unauthorized access, and cyberattacks by examining system memory snapshots.
Memory Forensics Explained Easy
Imagine your computer’s memory is like a whiteboard where temporary notes are written while you work. If someone erases something bad from a document, you might still see faint marks left behind. Memory forensics works like a detective using a special light to read those erased marks.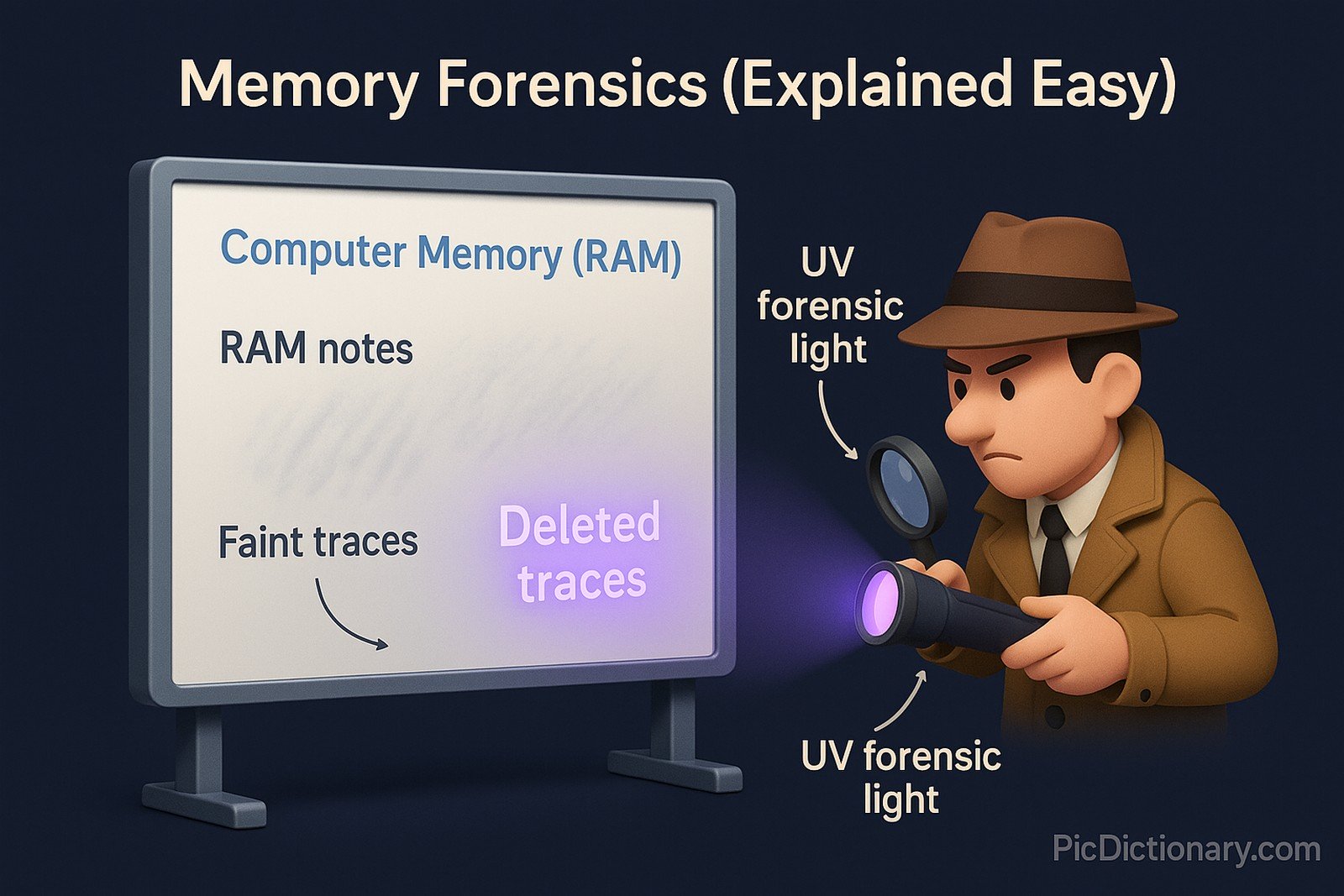
Memory Forensics Origin
Memory forensics emerged as an essential cybersecurity practice in the early 2000s when advanced threats became harder to detect using traditional disk-based analysis.
Memory Forensics Etymology
The term “memory forensics” combines “memory,” referring to a computer’s volatile RAM, and “forensics,” derived from the Latin *forensis*, meaning “pertaining to the forum” or legal proceedings.
Memory Forensics Usage Trends
The adoption of memory forensics has grown significantly with the rise of advanced cyber threats. Cybersecurity teams, government agencies, and forensic analysts increasingly rely on memory analysis.
Memory Forensics Usage
- Formal/Technical Tagging:
- Digital Forensics
- Incident Response
- Cyber Threat Intelligence - Typical Collocations:
- "memory forensic analysis"
- "RAM dump examination"
- "live memory investigation"
- "malware detection through memory forensics"
Memory Forensics Examples in Context
- A forensic analyst uses memory forensics to retrieve encryption keys from a compromised server.
- Security teams analyze RAM dumps to detect advanced persistent threats (APTs).
- Investigators use memory forensics to recover chat messages from a suspect’s laptop.
Memory Forensics FAQ
- What is memory forensics?
Memory forensics is the examination of a computer’s RAM to uncover security threats and forensic evidence. - What tools are used for memory forensics?
Popular tools include Volatility, Rekall, and Memoryze. - Can memory forensics detect fileless malware?
Yes, memory forensics is essential for identifying fileless malware. - What are some challenges of memory forensics?
Volatile memory is lost upon shutdown, and encryption can complicate data extraction.
Memory Forensics Related Words
- Categories/Topics:
- Digital Forensics
- Cybersecurity
- Malware Analysis
Did you know?
Memory forensics played a crucial role in uncovering the Stuxnet malware, one of the most sophisticated cyberattacks in history.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment