Rowhammer Exploit

Quick Navigation:
- Rowhammer Exploit Definition
- Rowhammer Exploit Explained Easy
- Rowhammer Exploit Origin
- Rowhammer Exploit Etymology
- Rowhammer Exploit Usage Trends
- Rowhammer Exploit Usage
- Rowhammer Exploit Examples in Context
- Rowhammer Exploit FAQ
- Rowhammer Exploit Related Words
Rowhammer Exploit Definition
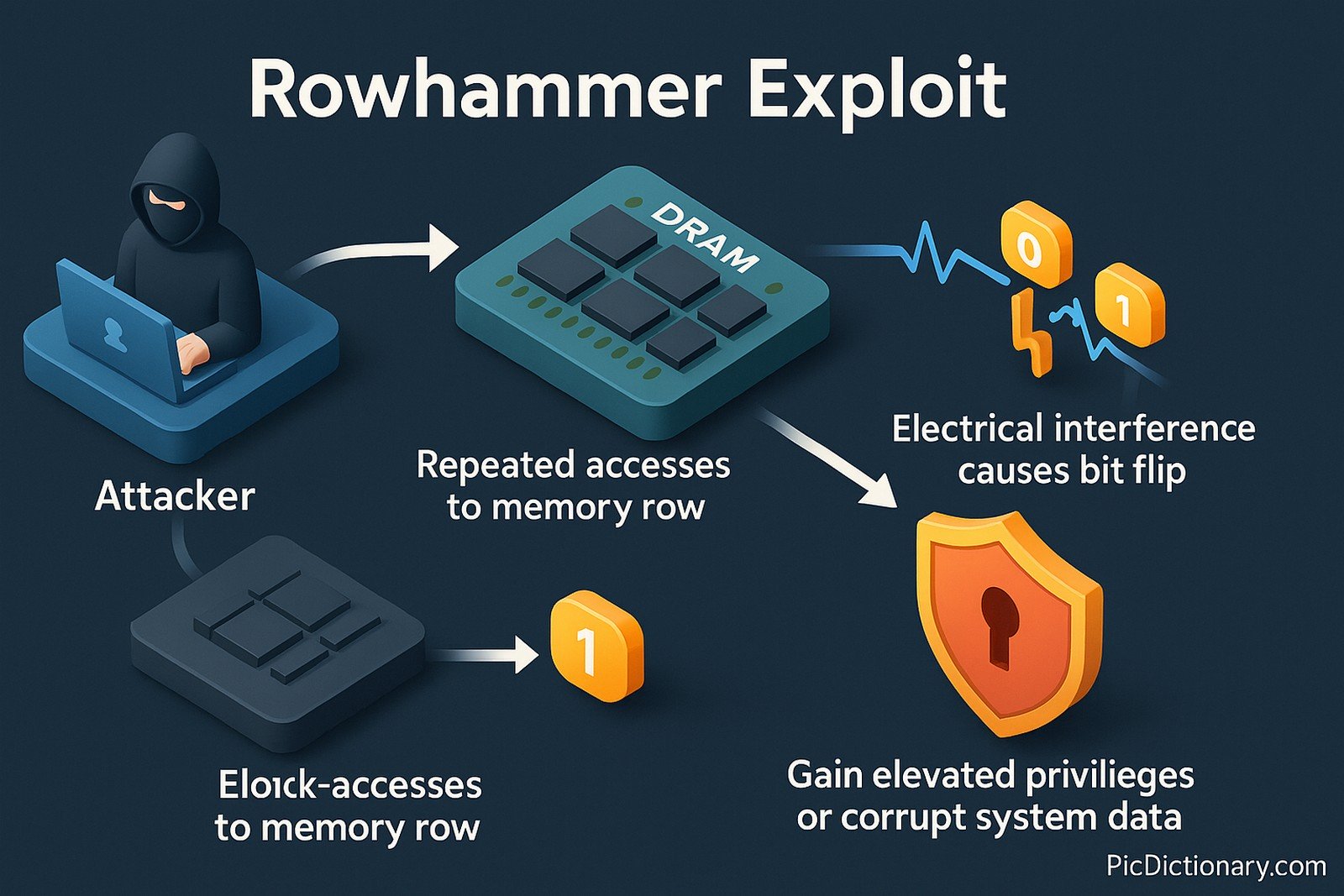
Rowhammer is a security exploit that leverages a hardware vulnerability in DRAM chips. It occurs when a high number of repeated accesses to a memory row (hammering) cause electrical interference that flips bits in adjacent rows. This unintended bit flip can be exploited by attackers to gain elevated privileges or corrupt system data.
Rowhammer Exploit Explained Easy
Imagine you have a big bookshelf with many books. If you keep tapping on one shelf over and over, eventually, the books on the next shelf start to shake and fall. Rowhammer works the same way: by repeatedly accessing one memory row, it causes nearby rows to get unstable and change their data.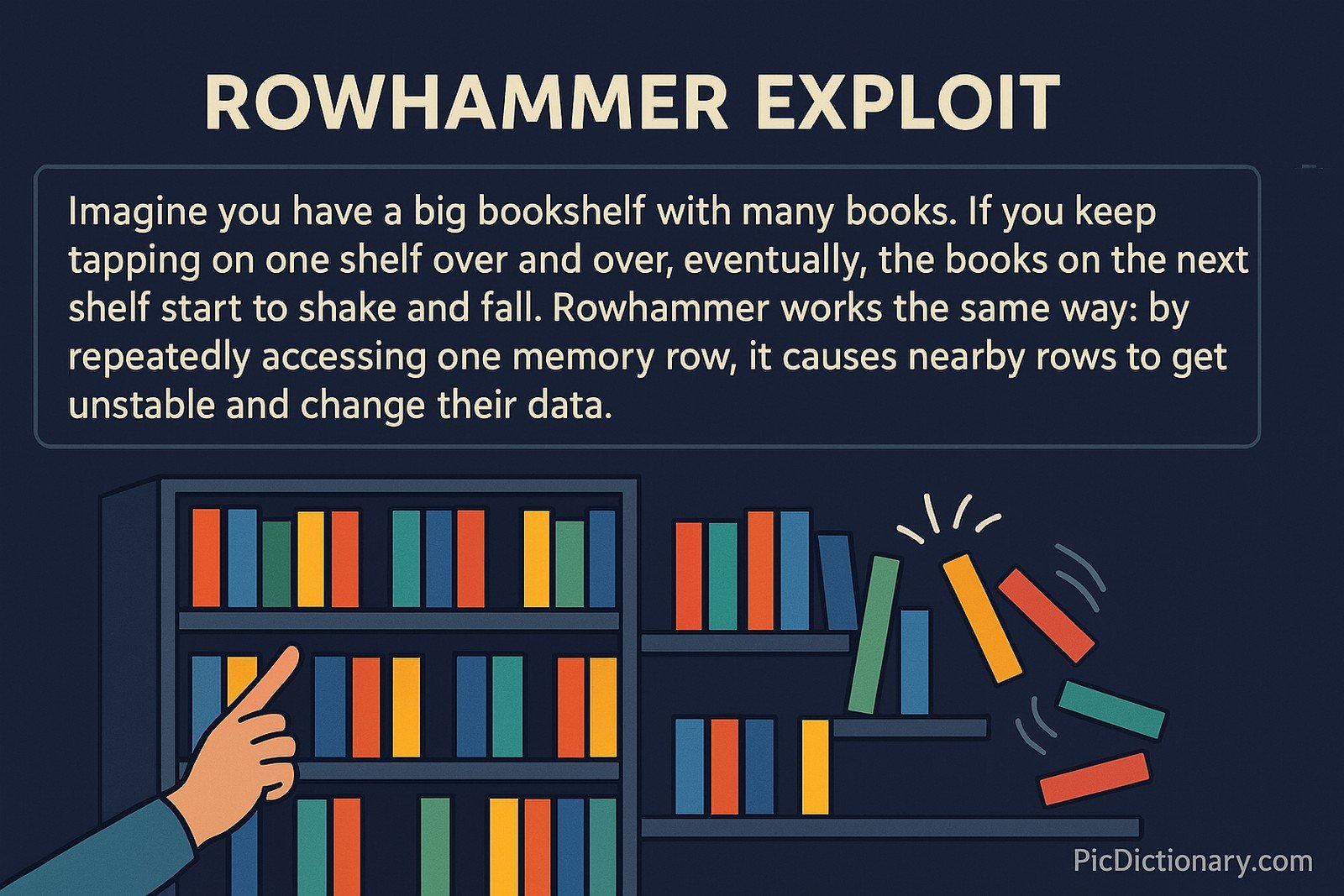
Rowhammer Exploit Origin
Rowhammer was first documented as a security issue in 2014 when researchers discovered that intensive memory access patterns could induce bit flips in adjacent memory rows.
Rowhammer Exploit Etymology
The name "Rowhammer" comes from the method used in the exploit—aggressively "hammering" a specific memory row by rapidly reading or writing to it.
Rowhammer Exploit Usage Trends
Rowhammer has evolved from a theoretical attack into a practical threat, with several variations developed over time. Researchers have demonstrated software-based Rowhammer exploits that require no physical access to hardware.
Rowhammer Exploit Usage
- Formal/Technical Tagging:
- Hardware Security
- Memory Corruption
- DRAM Vulnerabilities - Typical Collocations:
- "Rowhammer-based attack"
- "bit-flip vulnerability"
- "exploiting DRAM weaknesses"
Rowhammer Exploit Examples in Context
- Security researchers demonstrated that a Rowhammer attack could be used to gain root access on Linux systems.
- A variant of Rowhammer was used in cloud-based attacks.
- Manufacturers have developed TRR (Target Row Refresh) as a defense mechanism against Rowhammer.
Rowhammer Exploit FAQ
- What is the Rowhammer exploit?
Rowhammer is a security vulnerability in DRAM chips where repeated memory accesses cause unintended bit flips in adjacent memory rows. - Why is Rowhammer a serious threat?
Rowhammer can allow attackers to manipulate system memory, leading to unauthorized access. - How does Rowhammer work?
It exploits the physical properties of DRAM by repeatedly accessing specific memory rows.
Rowhammer Exploit Related Words
- Categories/Topics:
- Computer Security
- Hardware Vulnerabilities
- Memory Exploits
Did you know?
Google researchers developed a cloud-based Rowhammer attack, proving that it was possible to execute the exploit remotely.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment