Speculative Execution
 (Representational Image | Source: Dall-E)
(Representational Image | Source: Dall-E)
Quick Navigation:
- Speculative Execution Definition
- Speculative Execution Explained Easy
- Speculative Execution Origin
- Speculative Execution Etymology
- Speculative Execution Usage Trends
- Speculative Execution Usage
- Speculative Execution Examples in Context
- Speculative Execution FAQ
- Speculative Execution Related Words
Speculative Execution Definition
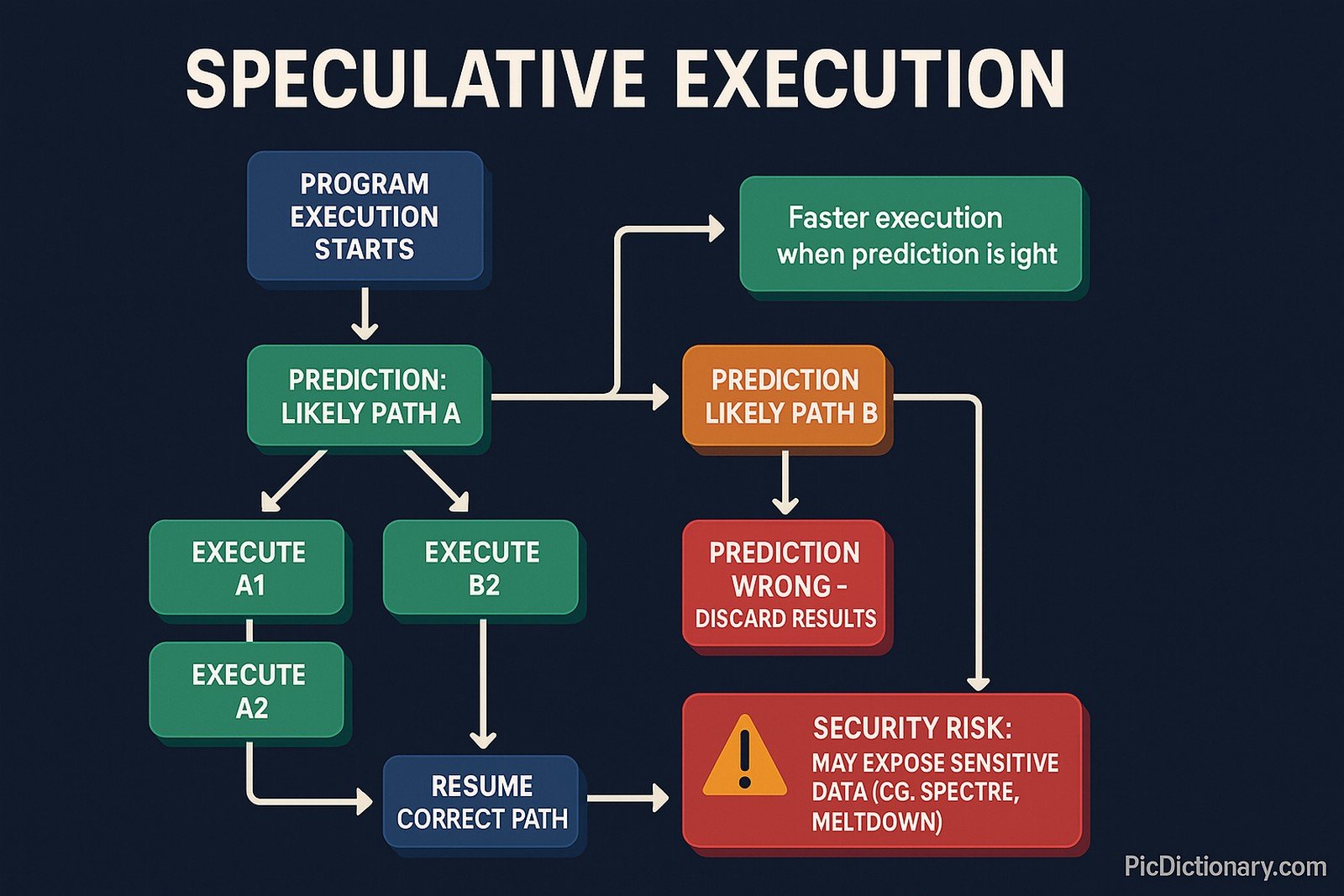
Speculative execution is a performance-enhancing technique used in modern processors where a CPU guesses the likely execution path of a program and begins executing instructions ahead of time. If the guess is correct, performance improves since the instructions were preprocessed. However, if incorrect, the CPU discards the results and rolls back to the correct path. This method is key to optimizing computing speed but has also led to security vulnerabilities like Spectre and Meltdown.
Speculative Execution Explained Easy
Imagine you’re waiting in line for food, and before you reach the counter, the chef starts preparing your favorite dish, guessing what you will order. If the guess is right, you get your food quickly. But if it’s wrong, they have to throw it away and start over. Speculative execution works the same way: the computer predicts what will happen next and prepares in advance to work faster.
Speculative Execution Origin
Speculative execution was first introduced in the 1960s in early supercomputers, but it became widely used in the 1990s with the rise of advanced pipelined and out-of-order execution processors. The goal was to improve efficiency by reducing idle time while waiting for data or instructions.
Speculative Execution Etymology
The term “speculative” originates from the Latin word speculatus, meaning "observed" or "examined," while "execution" refers to carrying out instructions in a computer. The phrase describes the process of making an educated guess to execute instructions before confirmation.
Speculative Execution Usage Trends
With the rise of multi-core processors and high-performance computing, speculative execution has become a fundamental optimization technique in CPUs. However, its widespread use led to security concerns, particularly after the discovery of vulnerabilities like Spectre and Meltdown in 2018, which exploited speculative execution to access sensitive data.
Speculative Execution Usage
- Formal/Technical Tagging:
- Computer Architecture
- CPU Optimization
- Security Vulnerabilities
- Typical Collocations:
- “speculative execution attack”
- “out-of-order execution”
- “speculative execution vulnerability”
- “performance optimization through speculation”
Speculative Execution Examples in Context
- Modern Intel and AMD processors use speculative execution to improve performance by predicting and executing future instructions.
- Security researchers discovered that speculative execution could be exploited to leak sensitive data, leading to industry-wide patches.
- Cloud computing providers had to update their infrastructure to mitigate speculative execution vulnerabilities.
Speculative Execution FAQ
- What is speculative execution?
Speculative execution is a CPU technique that predicts and executes future instructions to improve performance. - How does speculative execution work?
The CPU guesses which instructions will be needed next and processes them in advance. If correct, performance improves; if incorrect, results are discarded. - Why is speculative execution important?
It speeds up processing by reducing idle time while waiting for data or instructions. - What are the risks of speculative execution?
It can introduce security vulnerabilities, such as Spectre and Meltdown, which allow attackers to access protected data. - How do Spectre and Meltdown exploit speculative execution?
These attacks manipulate speculative execution to leak sensitive data from memory that should remain inaccessible. - Can speculative execution be disabled?
Some security patches restrict speculative execution, but completely disabling it can significantly reduce CPU performance. - Which processors use speculative execution?
Almost all modern CPUs, including those from Intel, AMD, and ARM, utilize speculative execution for performance gains. - How did the industry respond to speculative execution vulnerabilities?
Tech companies released security patches and redesigned CPUs to mitigate risks while maintaining performance. - Is speculative execution still used despite security risks?
Yes, but modern CPUs incorporate safeguards to minimize vulnerabilities while retaining the performance benefits. - Can software developers prevent speculative execution attacks?
Developers use techniques like software fencing and microcode updates to reduce risks associated with speculative execution.
Speculative Execution Related Words
- Categories/Topics:
- Computer Architecture
- Processor Security
- Performance Optimization
Did you know?
In 2018, Spectre and Meltdown exposed major security flaws in speculative execution, affecting billions of devices worldwide. This forced companies like Intel, AMD, and ARM to release emergency patches, slowing down some systems by up to 30% in the process.
PicDictionary.com is an online dictionary in pictures. If you have questions or suggestions, please reach out to us on WhatsApp or Twitter.Authors | Arjun Vishnu | @ArjunAndVishnu

I am Vishnu. I like AI, Linux, Single Board Computers, and Cloud Computing. I create the web & video content, and I also write for popular websites.
My younger brother, Arjun handles image & video editing. Together, we run a YouTube Channel that's focused on reviewing gadgets and explaining technology.



Comments powered by CComment